Risk Level: Medium
Description
This plugin ensures that tiered Auto Scaling Groups are using the CloudWatch logs agent. EC2 instances available within tiered Auto Scaling Group (ASG) should have logging enabled. It is recommended to have logging enabled as it is necessary to collect logs from Amazon EC2 instances, CloudTrail, and other sources.
Configuration Parameters
Cloudwatch Agent Install Command: This parameter denotes the command configured to install cloudwatch logs for the autoscaling group. An issue will be generated if the specified command is not configured.
By default, its value is set to “#!/bin/bash curl https://s3.amazonaws.com//aws-cloudwatch/downloads/latest/awslogs-agent-setup.py -O chmod +x ./awslogs-agent-setup.py ./awslogs-agent-setup.py -n -r -c s3://”.
Auto Scaling Group Tag Keys: This parameter denotes the list of keys used by auto-scaling groups to indicate tiered groups.
By default, the value is set to null.
About the Service
AWS Auto Scaling: As the name suggests, AWS AutoScaling monitors the running resources and if required, increases the scaling capability at the lowest possible costs. AutoScaling is easy to set up and automatically maintains the performance of your cloud infrastructure.
Impact
With proper logs enabled for instances, data will not be available to audit and investigate in case of any accidental exposure or attack. For the collection of logs from required resources, it is necessary to have the Cloudwatch logs agent installed.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon EC2 Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- Scroll down and select Auto Scaling Groups under the Auto Scaling section from the left pane.
- A list of Auto Scaling Groups will be displayed, select the one you want to investigate by clicking on its Launch Configuration column.
- In the Details section of the launch configuration selected, click on View user data.

- The user data will be displayed. Find the Cloudwatch Agent Install Command in the data displayed. If it could not be found, the vulnerability exists.
- Repeat steps for all the Auto Scaling groups you want to investigate.
Steps for Remediation
Update tiered Auto Scaling Group to use CloudWatch Logs agent.
- Log In to your AWS Console.
- First, create the cloudwatch logs configuration file required. Use the template to create and save a file named “app-instance-logs.cfg”. Next, upload this file in an S3 bucket.
[general]
state_file = /var/awslogs/state/agent-state
[/var/log/messages]
file = /var/log/messages
log_group_name = /var/log/messages
log_stream_name = {instance_id}
datetime_format = %b %d %H:%M:%S
- Open the Amazon EC2 Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- Scroll down and select Auto Scaling Groups under the Auto Scaling section from the left pane.

- A list of Auto Scaling Groups will be displayed, select the vulnerable group by clicking on its Launch Configuration column.
- Click on Copy Launch Configuration in the Details section.
- Scroll down to the Additional configuration section and expand the Advanced options category.
- In the user data input box, type in the following command
“#!/bin/bash
curl https://s3.amazonaws.com//aws-cloudwatch/downloads/latest/awslogs-agent-setup.py -O
chmod +x ./awslogs-agent-setup.py
./awslogs-agent-setup.py -n -r <AWS_REGION> -c s3://<S3_BUCKET_NAME>/app-instance-logs.cfg”
replacing the variables with the S3 file uploaded.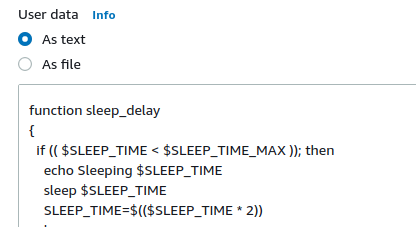
- Click on Create Launch Configuration.
- Move back to the Auto Scaling Group section. Select the vulnerable group by clicking on the checkbox next to it.
- Click on Edit. In the Launch Configuration section, select the newly created Launch Configuration.
- Repeat steps for all the vulnerable Auto Scaling groups.
