Risk Level: LOW
Description:
This plugin guarantees that the SQL Server Auditing retention policy is set to a value that is higher than the preset value. Enabling SQL Server Auditing guarantees that all actions, including potentially harmful behaviour, are appropriately logged. All logs are stored for auditing and legal purposes if you have a long retention policy. For databases hosted on Azure SQL servers, the retention period is the number of days to keep audit log data.
PingSafe strongly recommends ensuring that the storage account retention policy for each SQL server is set to greater than the configured number of days.
Configuration Parameters
Minimum Audit Retention Period In Days: This parameter denotes the desired number of days for which the audit should be retained. An alert will be generated if it's lower than the preset value.
By default, the value is set to 90 days, so it will show vulnerability if it is set lower than 90.
About the Service :
Azure SQL is a set of managed, secure, and intelligent SQL Server database solutions that run in the Azure cloud. Because Azure SQL is based on the well-known SQL Server engine, applications can be easily transferred while keeping the existing tools, languages, and resources.
Impact :
A log data retention term of 90 days or more should allow you to collect enough audit data to check for abnormalities and potential security breaches, as well as abuse of information and SQL database access.
Steps to Reproduce :
- Sign in to your Azure portal with your Azure account.
https://portal.azure.com/#home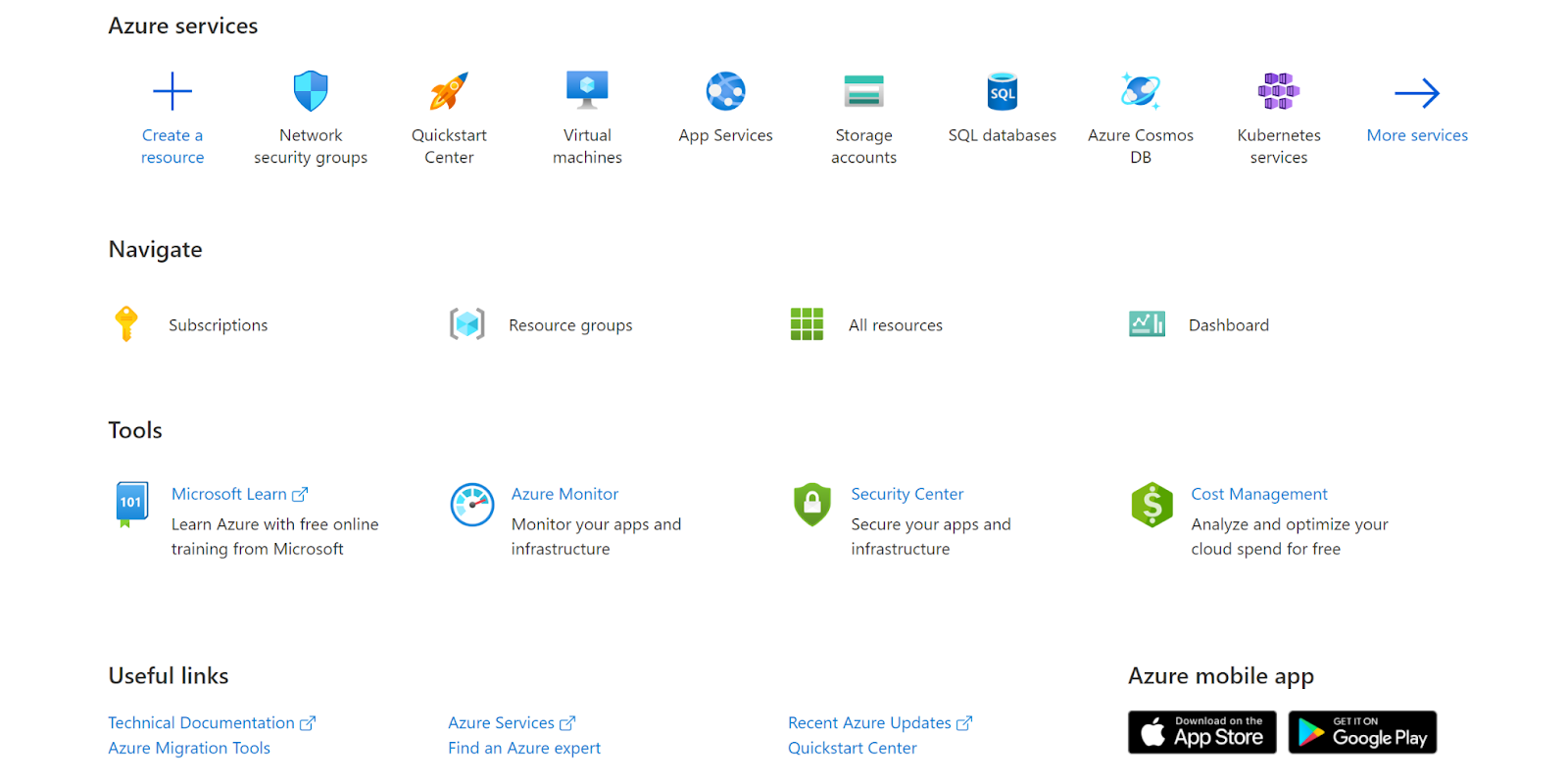
- Navigate to Azure’s All Resources.
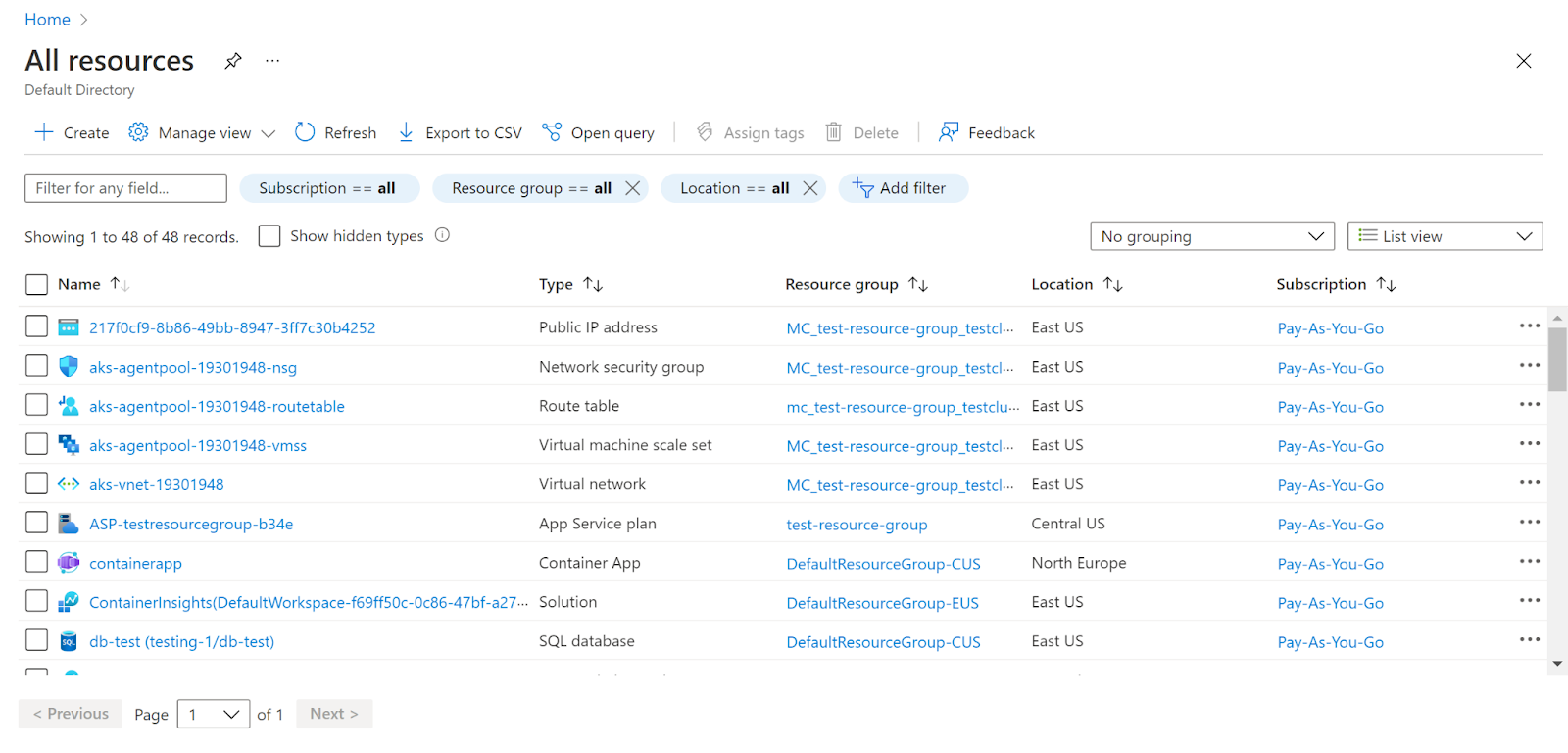
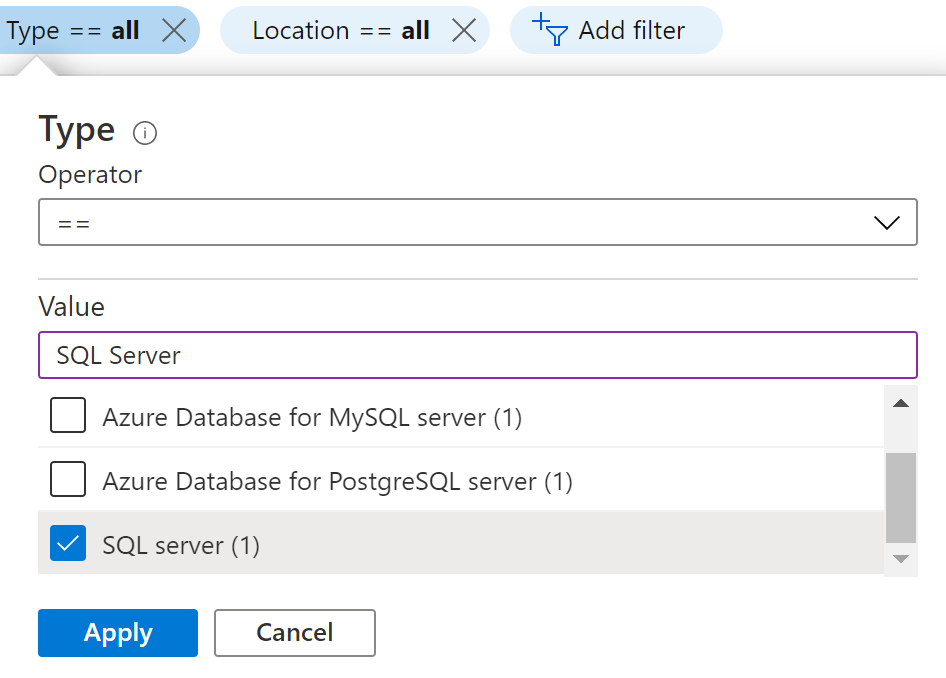
- In the Type filter select the value as SQL Servers and click Apply.
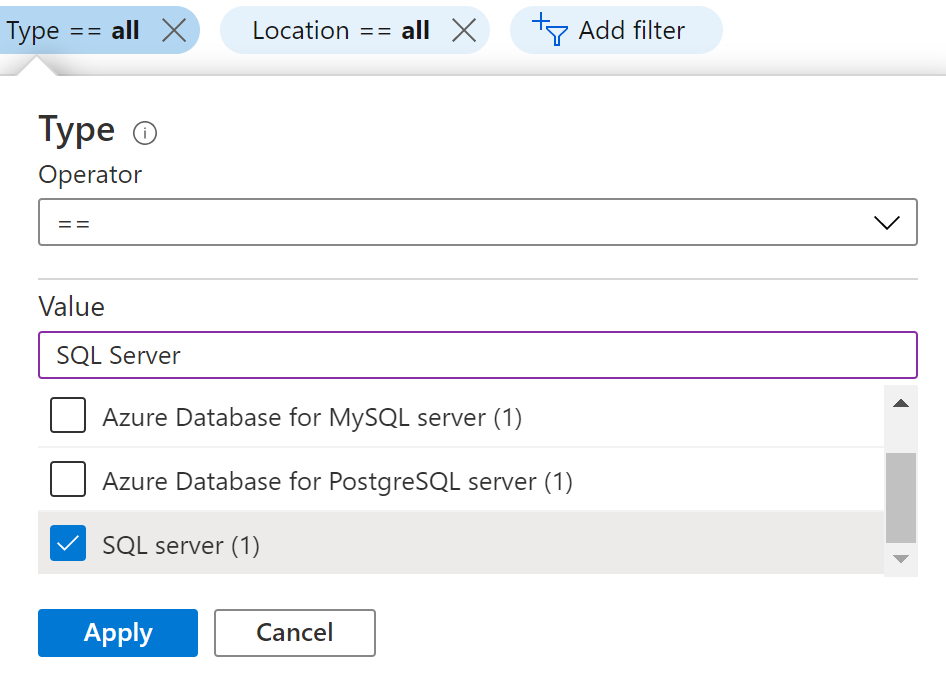
- Next, select the SQL Server that you want to examine.
- Click on Auditing under Security in the navigation pane.
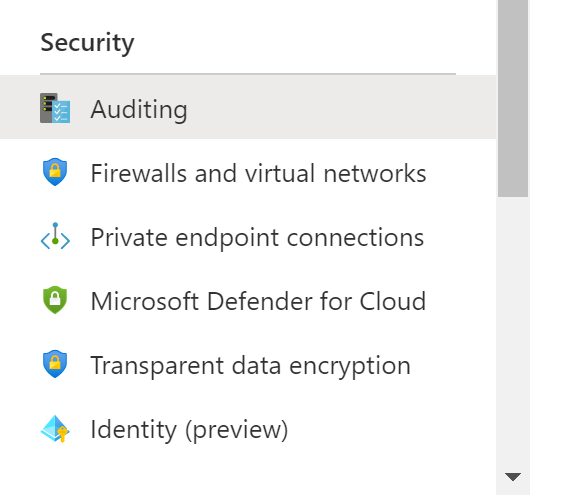
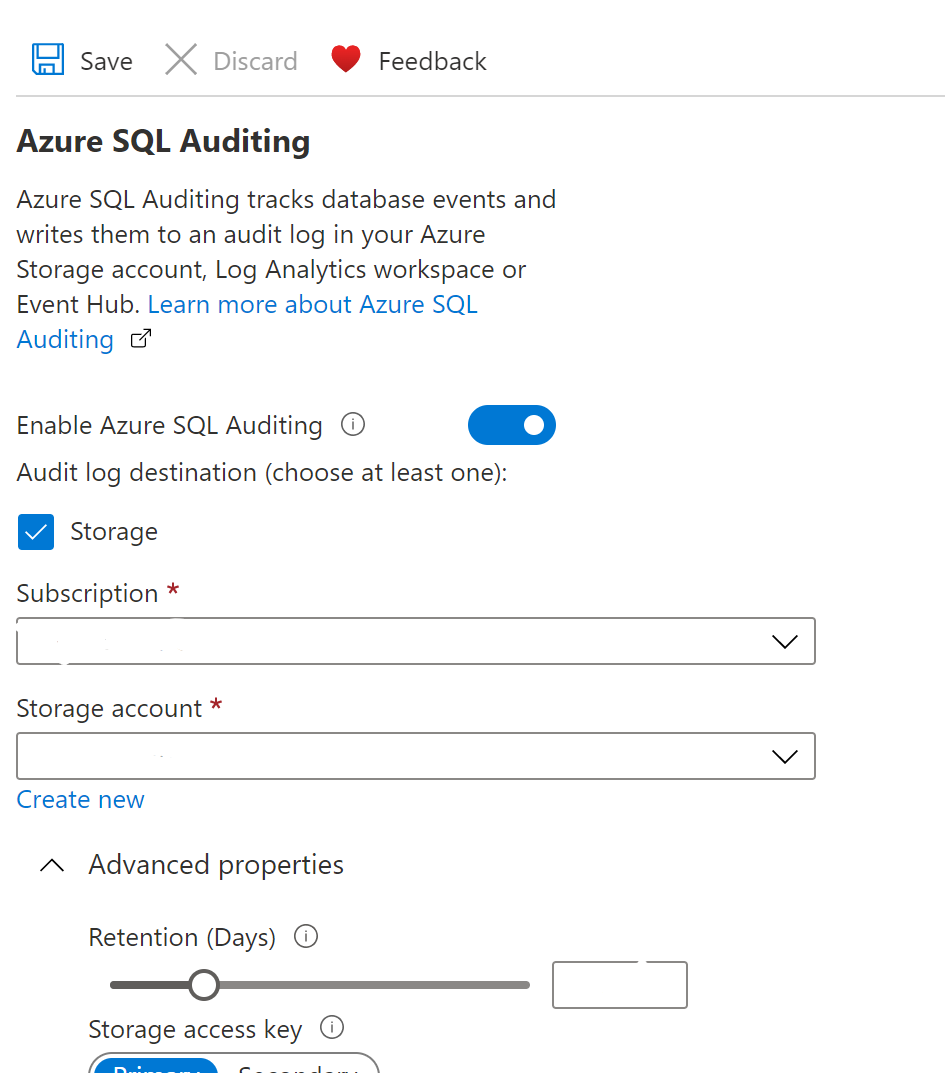
- Check whether the Retention days under the Advanced options in the auditing. If the storage account retention policy for each SQL server is not set to greater than the configured number of days then there is low audit retention policy.
- Repeat the same steps for other servers as well.
Steps for Remediation :
- Sign in to your Azure portal with your Azure account.
https://portal.azure.com/#home
- Navigate to Azure’s All Resources.
- In the Type filter select the value as SQL Servers and click Apply.
- Next, select the SQL Server that you want to examine.
- Click on Auditing under Security in the navigation pane.
- Check whether the Retention days under the Advanced options in the auditing. If the storage account retention policy for each SQL server is not set to greater than configured number of days then there is low audit retention policy.
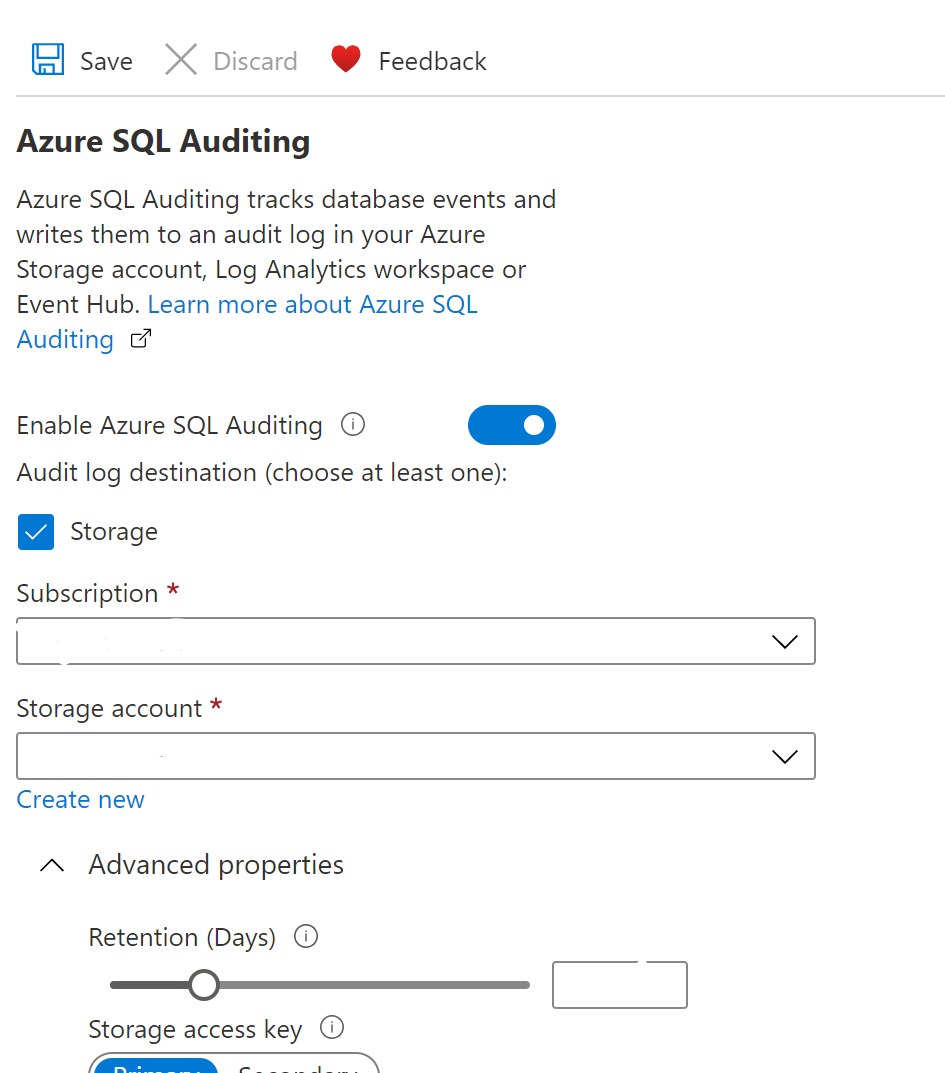
- Now, enter the number of retention days to be greater than the previous one and then click on Save.
- Repeat the same steps for other servers as well.
References :
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support
