Risk Level: Medium
Description
The plugin ensures that App services have authentication enabled so that unauthorized users are redirected to the login page first. The service ensures authentication of users with specific providers as well such as Azure AD, Microsoft Account, Twitter, etc.
About the Service
App Services: The app services at azure offers to host web applications, the REST API and backend services for mobile and web applications. Hosting web apps on Azure lets users focus on managing the application and its data.
Impact
The latest version of any software comes not only with improved features but also with security patches for loopholes that existed in the previous versions. Thus, selecting older versions of Software in the runtime stack provides threat actors with a loophole to damage and misuse the application’s resources and assets.
Steps to Reproduce
- Log in to the Azure portal.
- Click on App Services.
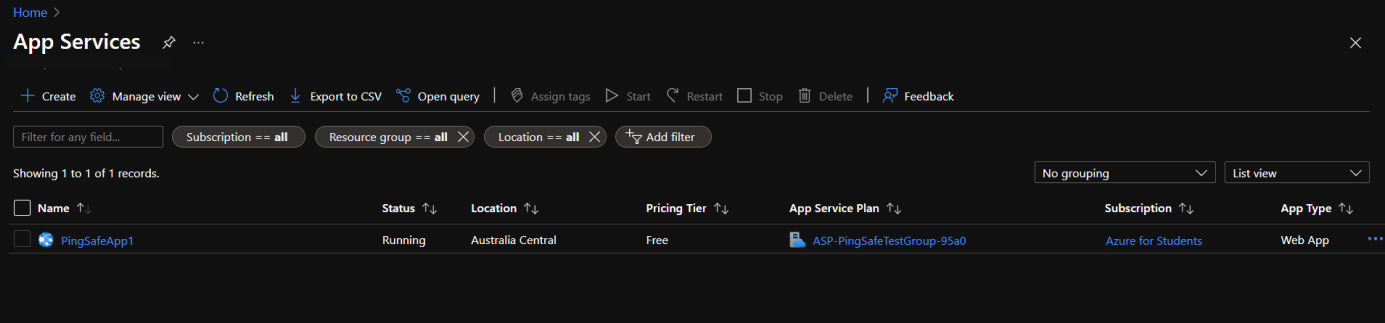
- Select an App Service plan from the listed apps.
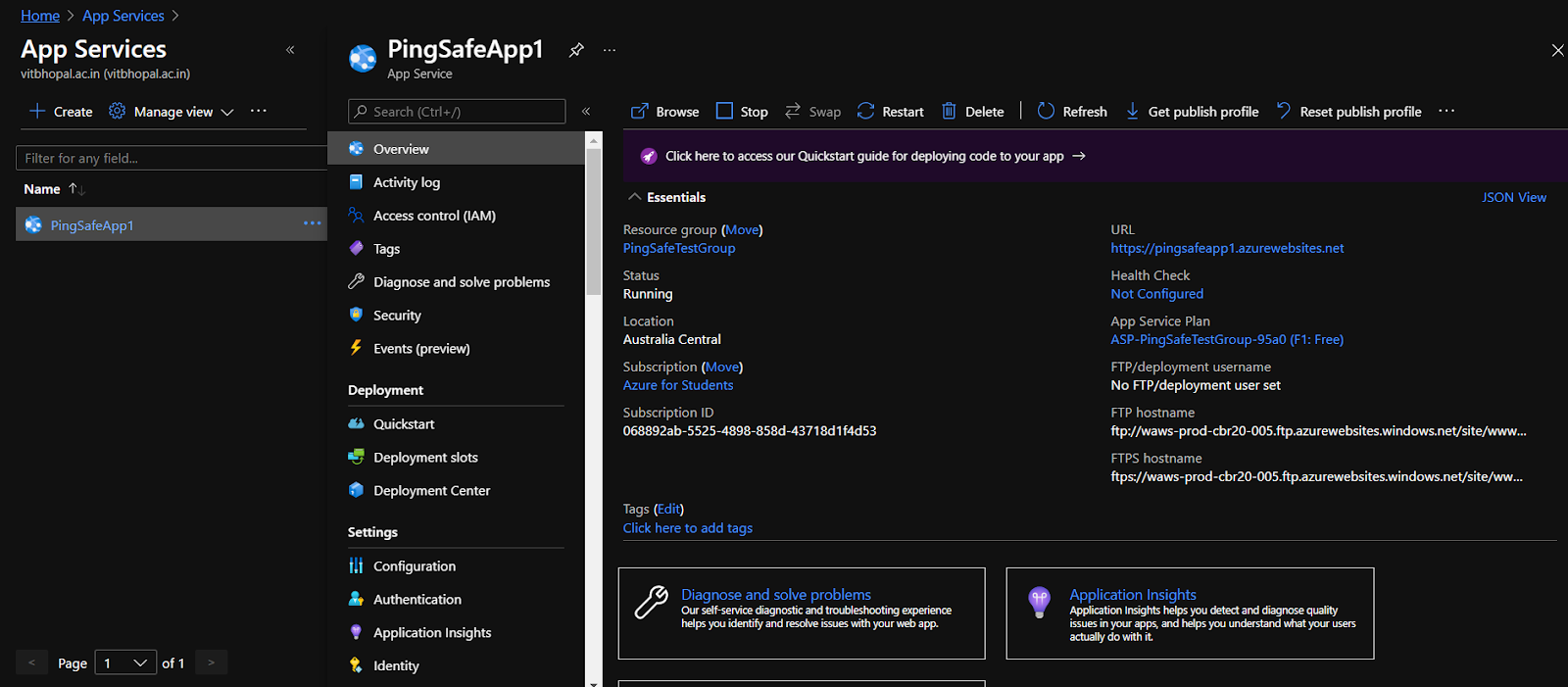
- Under the Settings section, click on Authentication.
- If the Authentication window shows a blank screen with the option of Add identity provider, go to Steps for Remediation section and then proceed.
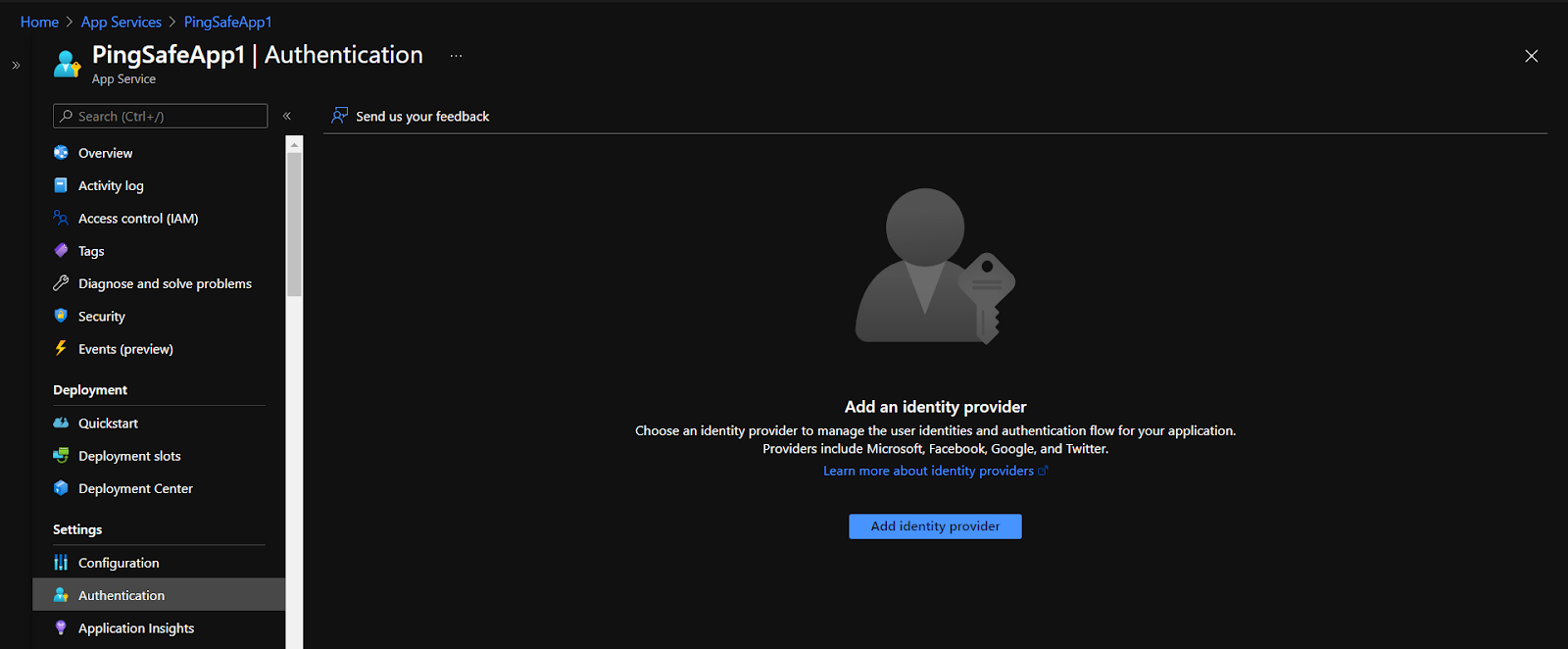
- Even if the window is not blank, under the Authentication Settings section check the value for App Service Authentication. If it says “Disabled”, go to the Steps for Remediation section for steps to enable authentication.
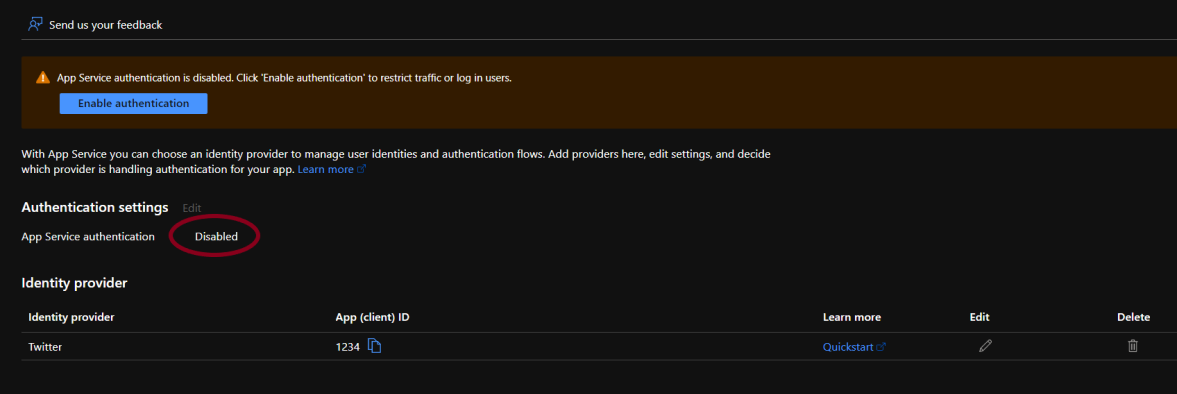
- Repeat the steps for other applications as well.
Steps for Remediation
Using Azure Portal:
- Log in to the Azure portal.
- Click on App Services.

- Select an App Service plan from the listed apps.

- Under the Settings section, click on Authentication.

- If the authentication is disabled then users will see an alert box on the screen stating Enable Authentication, click on it. The authentication service will automatically be enabled.
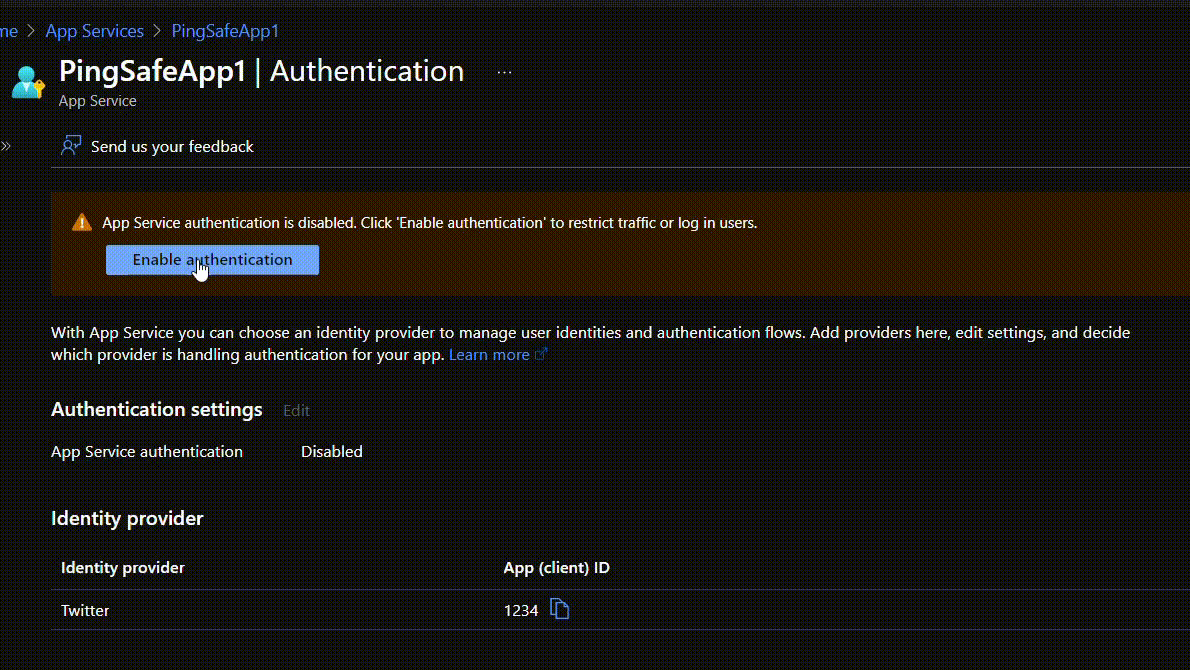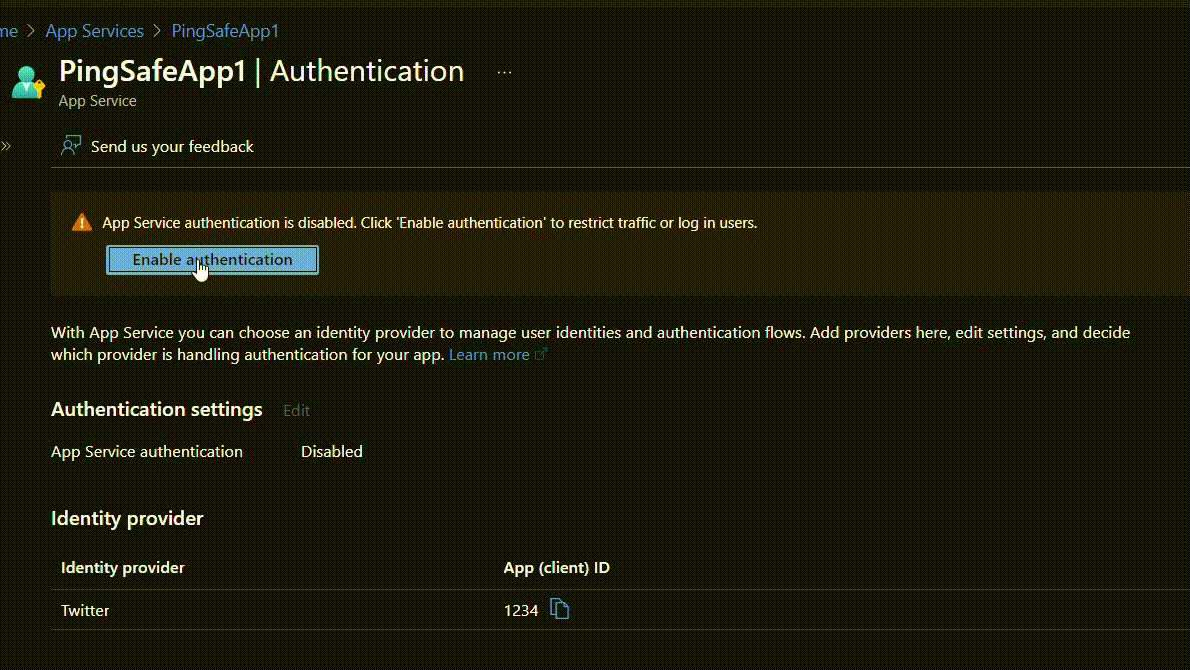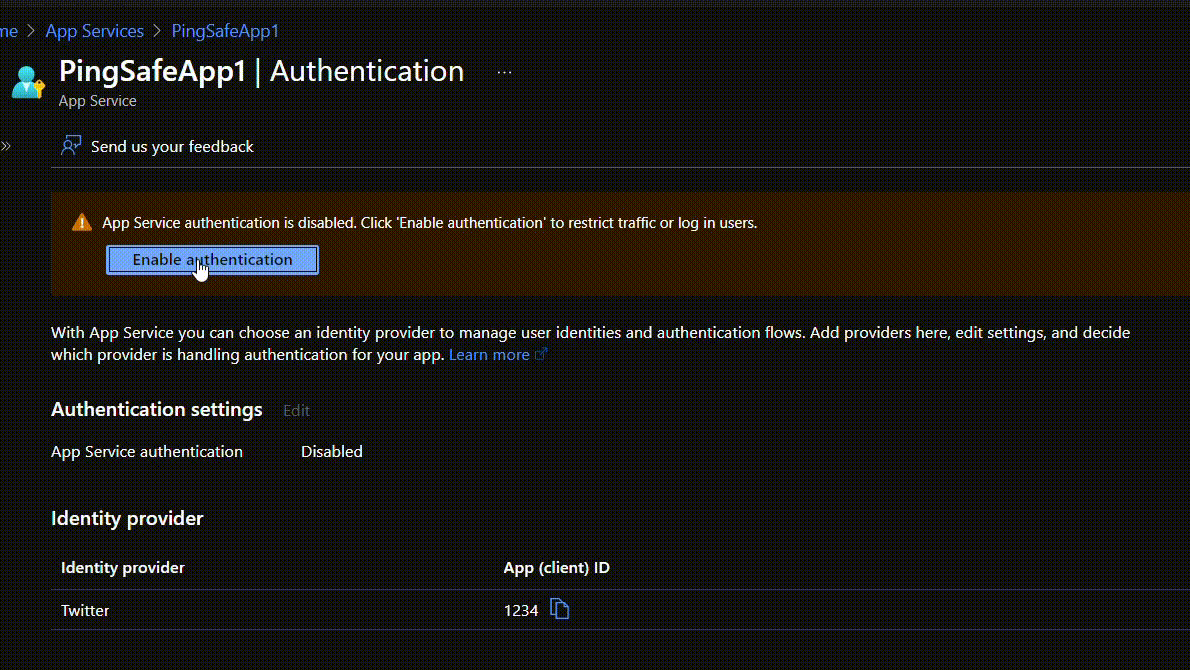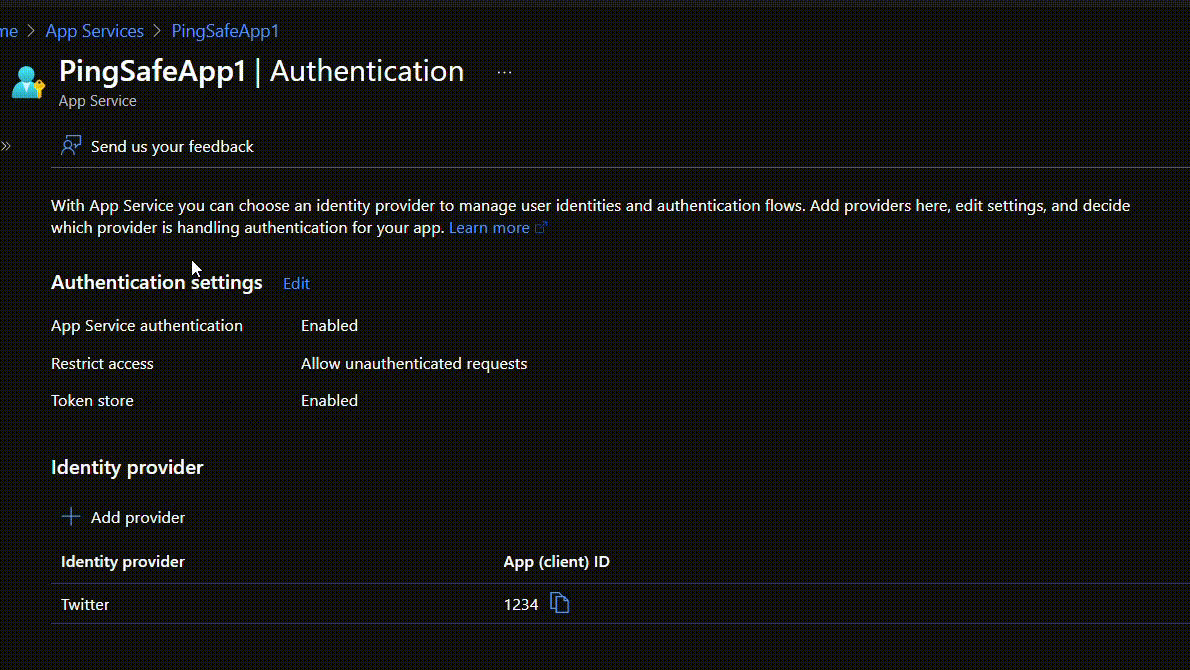
Using CLI Command:
In case of not receiving any notification, use the Azure CLI command to enable authentication:
- Login and authenticate Azure CLI:
az login
- Type the following command to enable authentication, specifying the resource group and application name of the vulnerable service:
az webapp auth update --resource-group ${resourceGroup} --name ${resourceName} --enabled truePlease feel free to reach out to support@pingsafe.com with any questions that you may have.
Thanks
PingSafe Support
