Risk Level: Medium
Description:
This plugin guarantees that ECR repository policies do not allow images to be accessed by multiple accounts. The use of account-level wildcards should be avoided in ECR repository policies, which should limit access to images to recognised IAM entities and AWS accounts.
About the Service :
Amazon's ECR private registries provide highly accessible and scalable container images. You may use your own private registry to manage private image repositories made out of images and artefacts from the Docker and Open Container Initiative (OCI). A default Amazon ECR registry is given for each AWS account.
Impact :
Amazon Elastic Container Registry utilizes access control policies based on resources. These kinds of authorization policies allow you to determine who has access and activities on your ECR repositories. The public access of your image repositories using Amazon ECR might lead to data leakage and/or data loss through resource-based rules.
Steps to reproduce :
- Log in to AWS Console.
- Navigate to the ECS dashboard.
https://us-east-2.console.aws.amazon.com/ecs/
- Click on “Repositories” in the left navigation panel under Amazon ECR.
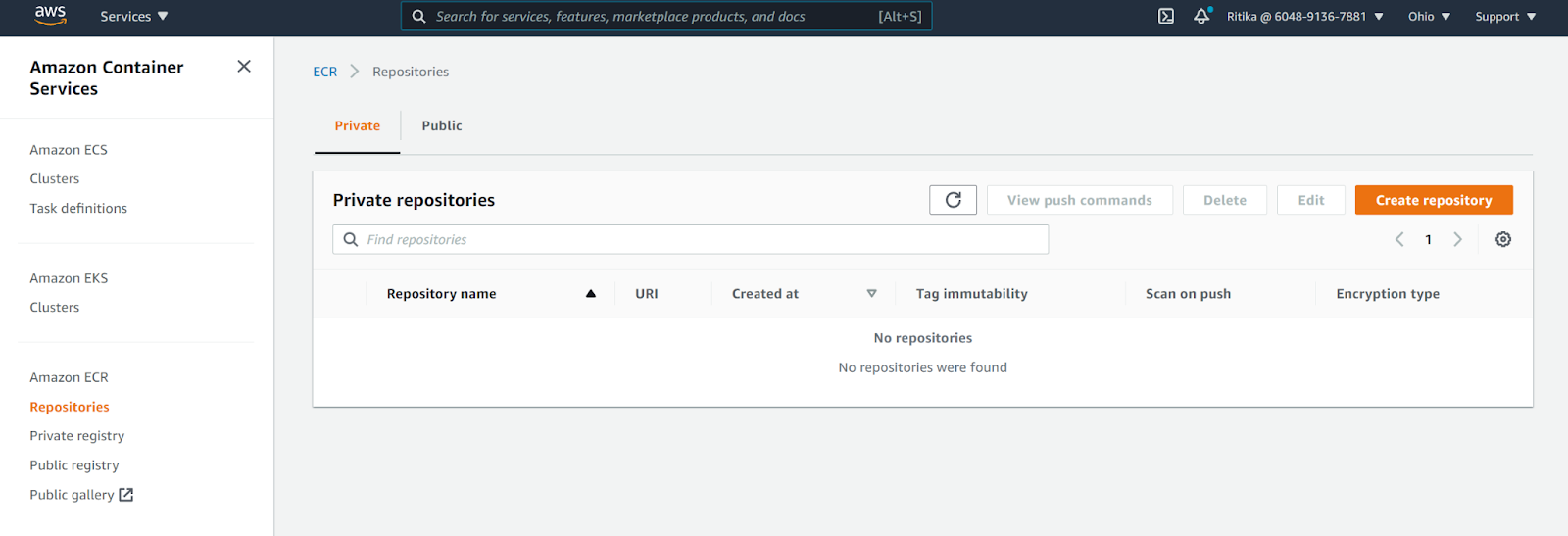
- Select the image repository that you want to examine.
- Click on the Permissions tab from the top panel to access the resource-based permissions set for the selected resource.
- Check the Principal elements values in the Policy document box to identify the AWS account ID.
- Sign in to the PingSafe console, compare the AWS account ID found in the AWS ECR Unknown Cross Account Access conformity rule settings. Cross account access to the specified AWS Elastic Container Registry (ECR) image repository is not protected if the identity (account) ID identified does not match any of the trusted entities IDs indicated on your Cloud Conformity dashboard.
- Repeat the steps for the rest of the Amazon ECR repositories available within the current region.
Steps for remediation :
- Log in to AWS Console.
- Navigate to the ECS dashboard.
https://us-east-2.console.aws.amazon.com/ecs/
- Click on “Repositories” in the left navigation panel under Amazon ECR.

- Select the image repository that you want to examine.
- Click on the Permissions tab to access the permission policy defined for the selected repository.
- Check the Principal elements values in the Policy document box to identify the AWS account ID.
- Sign in to the PingSafe console, compare the AWS account ID found in the AWS ECR Unknown Cross Account Access conformity rule settings. Cross account access to the specified AWS Elastic Container Registry (ECR) image repository is not protected if the identity (account) ID identified does not match any of the trusted entities IDs indicated on your Cloud Conformity dashboard.
- Replace the AWS account ID available within the Principal box with the account ID of the trusted AWS entity, defined in the conformity rule settings in the Principal section.
- Choose the actions that the principal is allowed to perform in the Actions section. At last click on Save Changes to apply the policy changes.
- Repeat the steps for each Amazon ECR image repository that you want to reconfigure, available in the current region.
References:
