Risk Level: Medium
Description:
This plugin guarantees that EMR clusters have encryption in transit enabled. Encryption in transport should be enabled for EMR clusters.
PingSafe strongly recommends updating the security configuration associated with the EMR cluster to enable encryption in transit.
About the Service :
Amazon EMR (Amazon Elastic MapReduce) is a managed cluster platform that makes it easier to run big data frameworks on AWS, such as Apache Hadoop and Apache Spark, to process and analyse large amounts of data. You may process data for analytics and business intelligence tasks using these frameworks and related open-source projects. Amazon EMR also allows you to convert and transport massive volumes of data into and out of other AWS data storage and databases, such as Amazon S3 and Amazon DynamoDB.
Impact :
When working with production data, encryption is strongly advised to safeguard the data from unwanted access and to meet your organization's compliance needs for data-at-rest and in-transit encryption.
Steps to reproduce :
- Log in to your AWS Management Console.
https://console.aws.amazon.com/ - Navigate to the EMR Dashboard.
https://console.aws.amazon.com/elasticmapreduce/
- In the left navigation panel, click on Clusters.
- Click on the cluster that you want to examine.
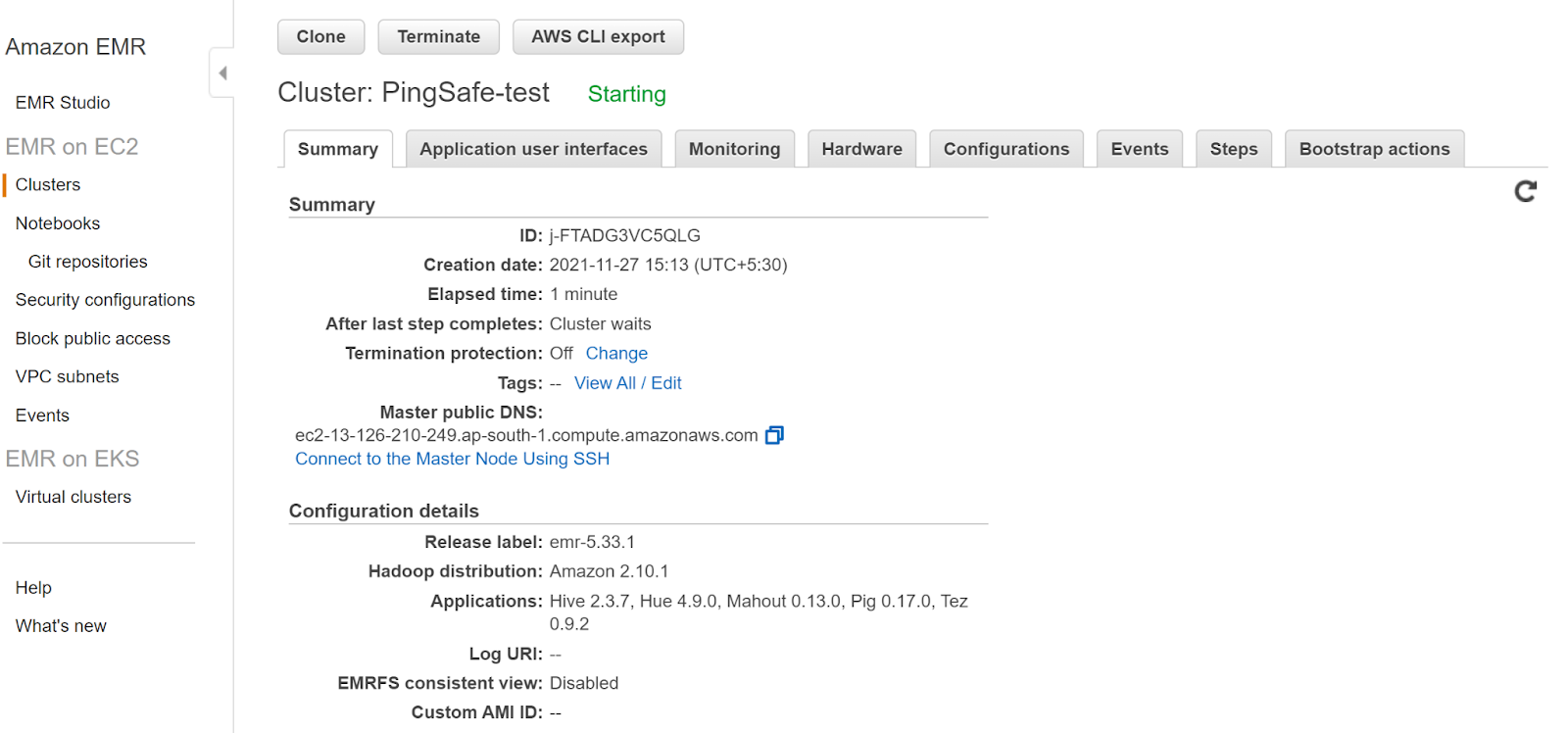
- In the Security and Access section, check the Security Configuration attribute. If there is no such attribute then EMR encryption in transit is disabled.
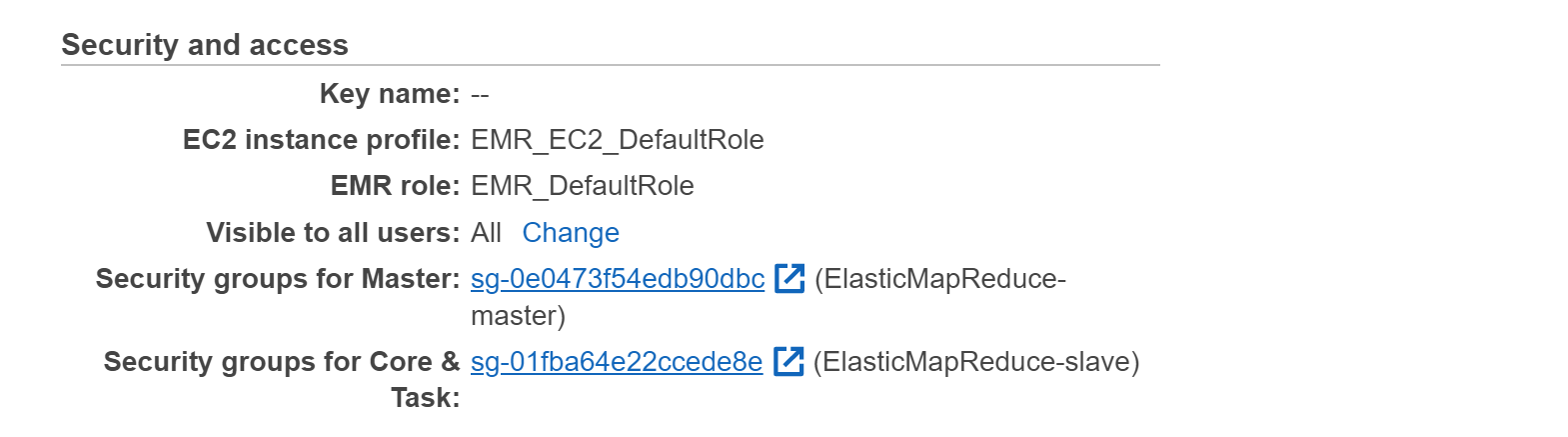
- Repeat the steps for other clusters as well.
Steps for remediation :
- Log in to your AWS Management Console.
https://console.aws.amazon.com/ - Navigate to the EMR Dashboard.
https://console.aws.amazon.com/elasticmapreduce/
- In the left navigation panel, click on Clusters.
- Click on the cluster that you want to examine.
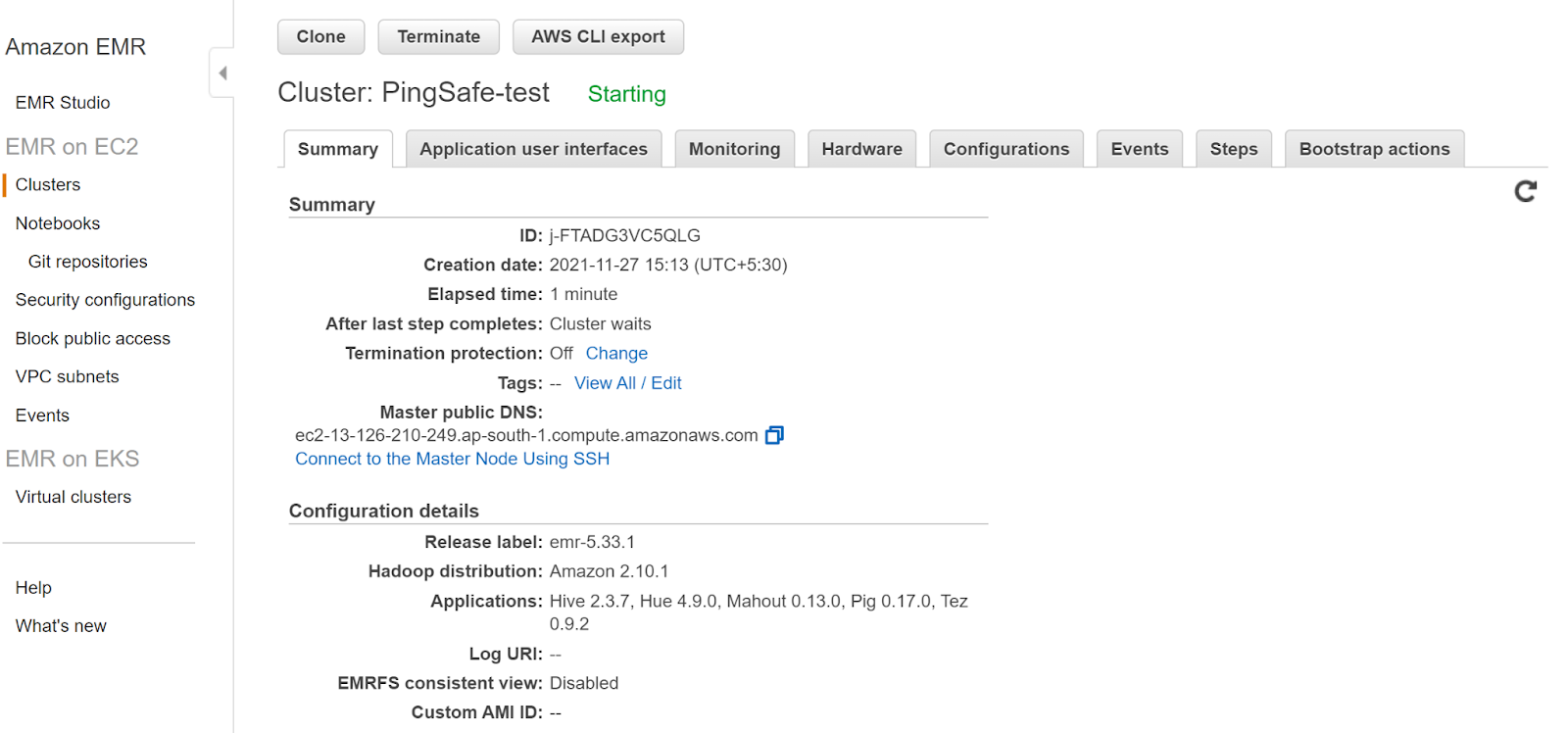
- In the Security and Access section, check the Security Configuration attribute. If there is no such attribute then EMR encryption in transit is disabled.

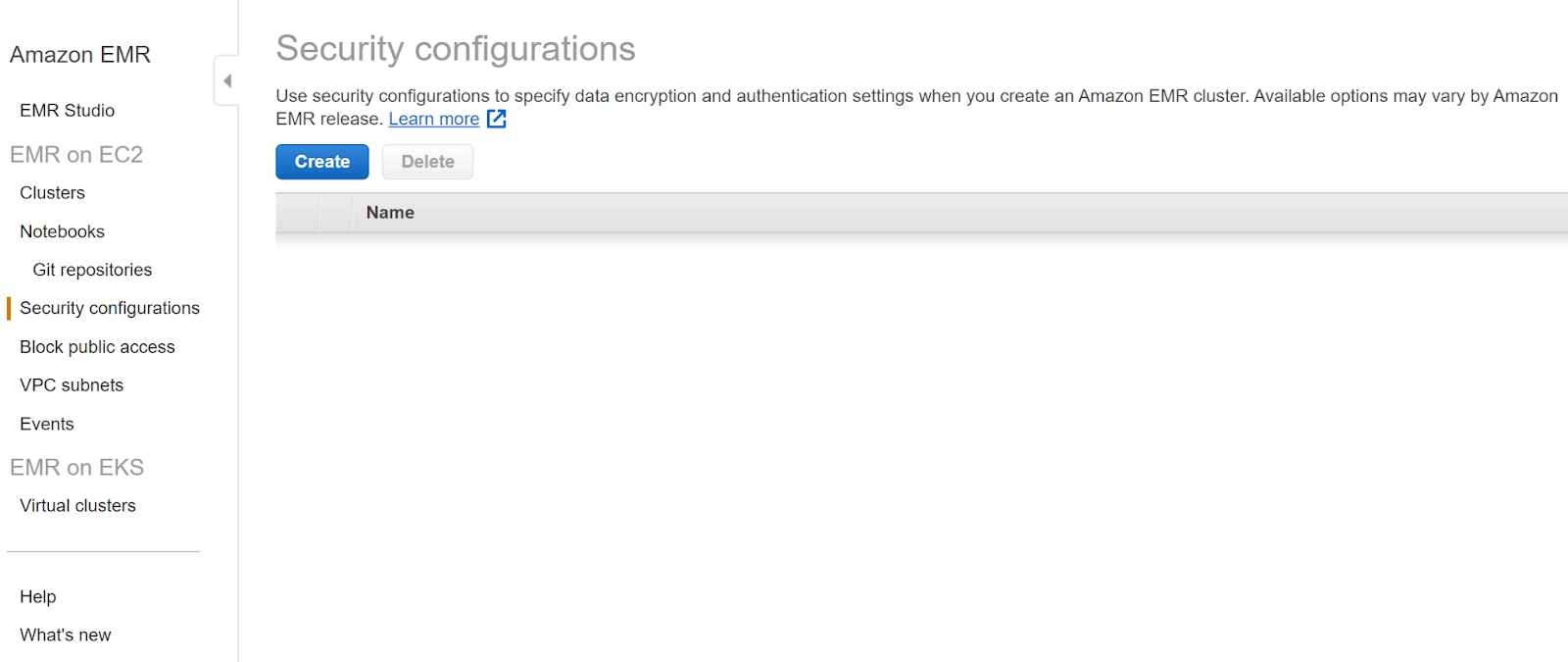
- Click on the Security Configuration in the left navigation pane and then click on Create.
- In the Data in Transit Encryption check the Enable in transit encryption and fill the required fields.
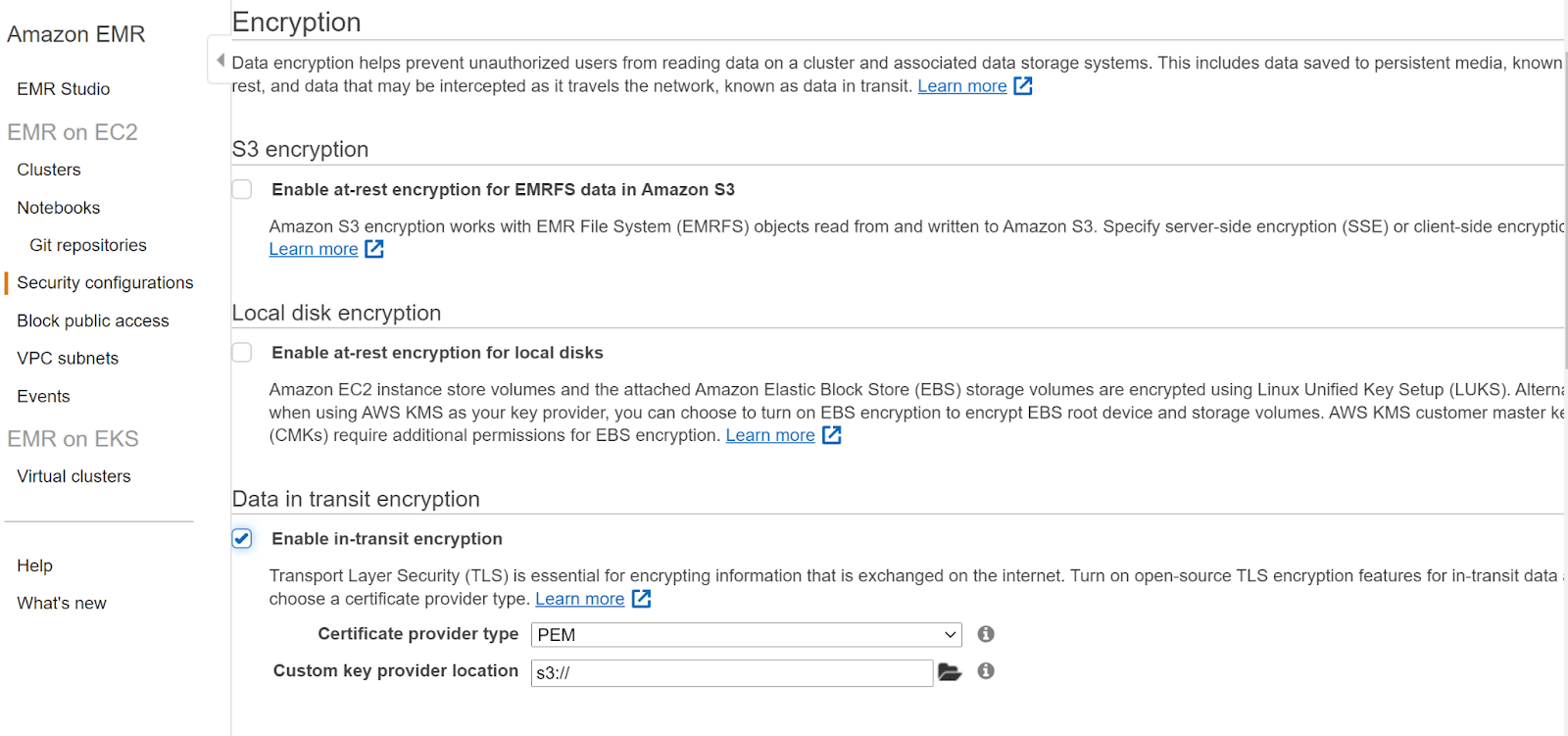
- Next click on Create and head back to the clusters page and click on Clone for the cluster that you want to relaunch.In the cloning page within the security options click Authentication and Encryption and then select the name of the security configuration created earlier.
- Click Next and once this cluster is up terminate the old cluster by clicking on Terminate.
- Repeat the steps for other clusters as well.
References:
