This plugin ensures that CloudTrail logs are delivered to CloudWatch in a timely manner
Risk Level: MEDIUM
Description:
This plugin ensures that CloudTrail logs are delivered to CloudWatch in a timely manner. Sending CloudTrail logs to CloudWatch allows for easy interaction with AWS CloudWatch alerts as well as additional backup log storage.
Recommended Action: Enable CloudTrail CloudWatch integration for all regions.
About the Service :
AWS CloudTrail is an AWS service that allows you to manage your AWS account's governance, compliance, operational, and risk auditing. In CloudTrail, actions done by a user, role, or AWS service are recorded as events. Actions made in the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs are all considered events.
Impact:
You won't be able to manage your AWS infrastructure efficiently without the CloudTrail - CloudWatch combination. For example, you won't get an SNS notification if your AWS account's authorization fails, thus you won't have as much control over account user access.
Steps to reproduce :
- Sign in to your AWS management console.
- Navigate to the CloudTrail dashboard at: https://console.aws.amazon.com/cloudtrail/
- On the left panel, select Trails.
- Click on the trail you want to examine.
- Check the CloudWatch Logs section.
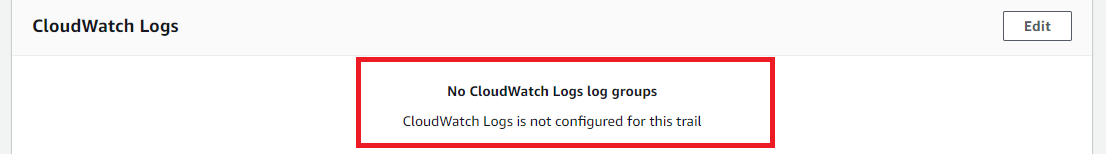
- If there aren't any CloudWatch Logs log groups defined, you must create one in order to enable CloudTrail integration with CloudWatch.
Steps for remediation :
Create a custom log group for the selected CloudTrail trail in order to enable AWS CloudWatch monitoring.
- Sign in to your AWS management console.
- Navigate to the CloudTrail dashboard at: https://console.aws.amazon.com/cloudtrail/
- On the left panel, select Trails.
- Click on the trail you want to examine.
- Check the CloudWatch Logs section and click Edit.
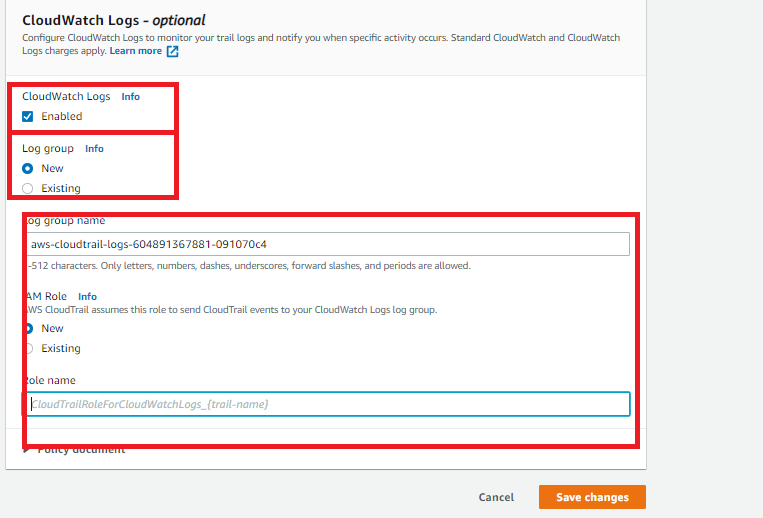
- For the CloudWatch logs option click on the Enable checkbox to select it.
- In the New or existing log group field, enter a name for a new or existing CloudWatch log group and click Continue.
- Do the same for the IAM role as we did for log groups in sub-step 7.
- Click on Save changes.
Create a Simple Notification Service (SNS) topic in order to send notifications whenever the CloudWatch alarm will fire based on a selected CloudTrail log event.
- Sign in to your AWS management console.
- Navigate to the SNS dashboard at: https://console.aws.amazon.com/sns/v2/
- Select Topics from the left navigation panel and click the Create new subject button.
- In the Create new topic dialog box, enter a name and a display name (optional) for the topic and click Create Topic.
- Select the newly created SNS topic by clicking on its ARN name.
- Under the Subscription section, click Create Subscription.
- From the Protocol selection list, choose a subscription protocol.
- Click and enter the email address where you'd want to receive CloudWatch alarm notifications. Make a Subscription.
- Open the message from AWS Notifications in your email client application, then click the appropriate link to confirm your membership.
Create AWS CloudWatch metric filters, metrics, and alarms to receive SNS notifications and take immediate action.
References:
