This plugin guarantees that CloudTrail is turned on for all regions in a given account.
Risk Level: High
Description:
This plugin guarantees that CloudTrail is turned on for all regions in a given account. To detect suspicious behavior in regions that aren't frequently accessed, CloudTrail should be enabled for all regions.
Recommended Action: Enable CloudTrail for all regions and ensure that at least one region monitors global service events
About the Service :
AWS CloudTrail is an AWS service that allows you to manage your AWS account's governance, compliance, operational, and risk auditing. In CloudTrail, actions done by a user, role, or AWS service are recorded as events. Actions made in the AWS Management Console, AWS Command Line Interface, and AWS SDKs and APIs are all considered events.
Impact:
Seeing as CloudTrail buckets contain important data, they should be secured against unwanted access. You won't be able to trace any requests made to access your CloudTrail buckets with S3 Server Access Logging disabled, and you couldn't even limit who can edit or remove the access logs to prevent a user from covering their tracks.
Steps to reproduce :
- Sign in to your AWS management console.
- Navigate to the CloudTrail dashboard at: https://console.aws.amazon.com/cloudtrail/
- On the left panel, select Trails.
- Click on the trail you want to examine.
- Copy the name of the S3 bucket associated with the trail.
- Visit S3 Dashboard, search for the copied S3 name, and open it.
- Under the Properties panel, check if the status of Server Acess Logging is given as disabled.
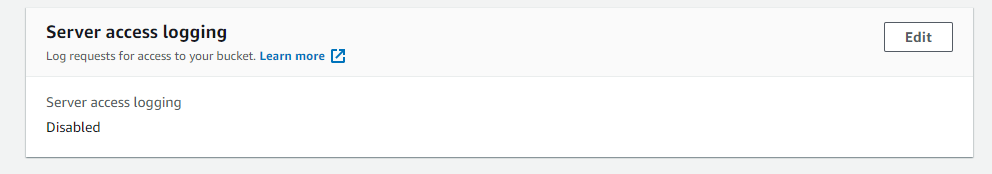
Steps for remediation :
- Sign in to your AWS management console.
- Navigate to the CloudTrail dashboard at: https://console.aws.amazon.com/cloudtrail/
- On the left panel, select Trails.
- Click on the trail you want to examine.
- Copy the name of the S3 bucket associated with the trail.
- Visit S3 Dashboard, search for the copied S3 name, and open it.
- Under the Properties panel, Click Edit on Server Access Logging and perform the following actions:
- Select the Enabled checkbox to enable the feature.
- In the Target Bucket field enter the name for the bucket that will store the access logs. You can use the selected bucket or create a new S3 bucket for these logs.
- In the Target Prefix field enter a name for the subdirectory where the access logs will be stored – useful to manage your logs.
- Click Save.
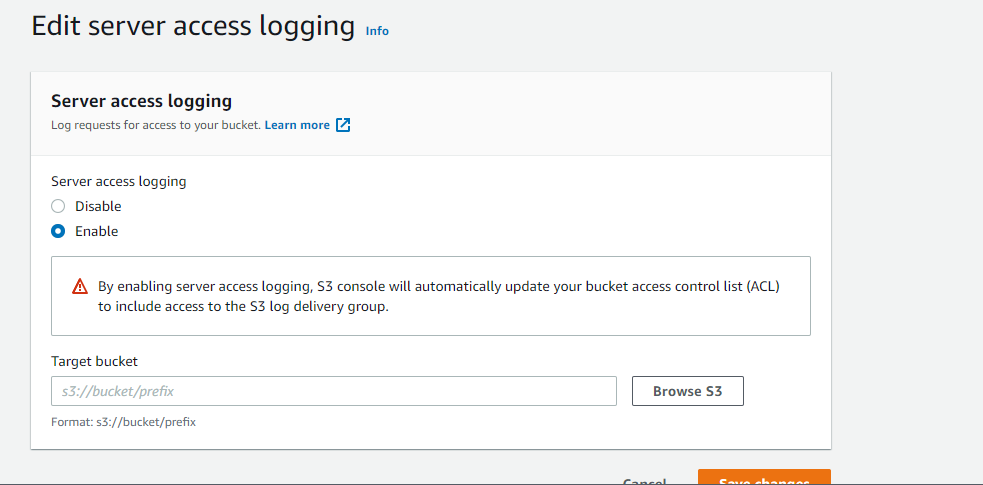
References:
- http://docs.aws.amazon.com/AmazonS3/latest/dev/ServerLogs.html
- http://docs.aws.amazon.com/awscloudtrail/latest/userguide/cloudtrail-concepts.html
