Ensure that all Kubernetes clusters are created with minimal access scope.
Risk Level: High
Description
This plugin ensures that the GKE node pools are not configured to use the default service account with full access to all cloud APIs. This violates the principle of least privilege. Thus, PingSafe strongly recommends that all the Kubernetes cluster node pools have minimal access scope.
About the Service
Google Cloud Kubernetes Engine:
The Google Cloud Kubernetes Engine is a Kubernetes-based service that includes a control plane, nodes that house pods, and Google Cloud services. It aids in the modernization of your programs by offering a platform for deploying, managing, and scaling containerized applications. The Google Cloud Console or kubectl can be used to interact with this Google Cloud Kubernetes Engine. To know more, read here.
Impact
If GKE clusters are configured to use the default service account with a scope of full access to all cloud APIs, it could result in privilege escalation. As a result, all users could be granted permission to perform various tasks that they are not meant to, eventually failing to follow the principle of least privilege. To know more about the principle of least privilege (POLP), read here.
Steps to Reproduce
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select the GCP project you want to investigate.

- From the navigation panel on the left side of the console, go to Kubernetes Engine and select Clusters. You can use this link here to navigate directly if you’re already logged in.
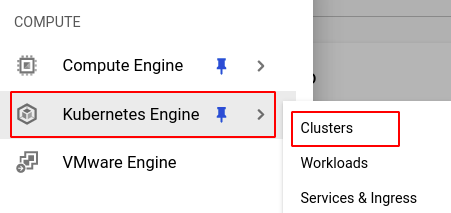
- Select the cluster you want to investigate from the list of clusters displayed and go to the NODES tab of the selected cluster.
- Under the Node pools section, select the node pool you want to verify from the list of node pools displayed in the table.
- In the Security section, check the configuration settings of all the Access scopes. If it is different from the ones shown in the screenshot below, the cluster is not using least privilege.
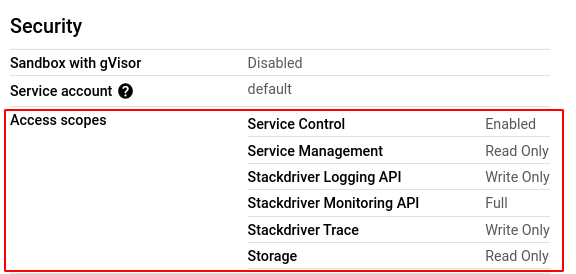
- Repeat steps 5 and 6 for all the node pools present in the selected cluster.
- Repeat steps 4 to 7 for all the clusters you want to investigate in the selected project.
- If you have multiple projects that you want to investigate, repeat steps 2-8 for each project in your GCP console.
Steps for Remediation
Make the necessary changes using the steps given below to ensure that the cluster node pools have minimal access scopes.
NOTE: The access scopes for node pools cannot be changed once the node pool is made. Hence, we must re-create the node pool.
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select the GCP project you want to investigate.

- From the navigation panel on the left side of the console, go to Kubernetes Engine and select Clusters. You can use this link here to navigate directly if you’re already logged in.

- Select the cluster you want to reconfigure from the list of clusters displayed and go to the NODES tab of the selected cluster. (In case you aren’t sure which node pool needs to be configured, follow the steps to reproduce listed above to determine which to choose.)

- Under the Node pools section, select the node pool you want to verify from the list of node pools displayed in the table and note down all the configuration details.
- Go back to the configuration page of the selected cluster and click on the ADD NODE POOL button.

- Enter and configure the desired details according to the configuration settings of the node pool you are re-creating.
- In the Security tab, choose the Allow default access option under Access scopes.
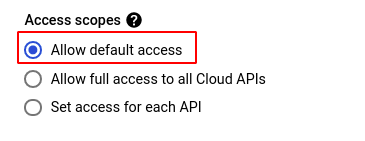
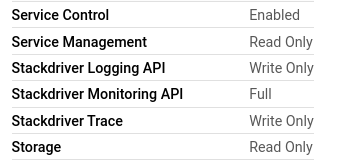
- If you wish to set your own access scopes for each API, ensure that the configurations for the ones shown in the screenshot below are followed.
- Click CREATE to create the new node pool.
- You can now delete the original node pool to avoid unwanted expenses. Click on the node pool and select the DELETE button from the top navigation bar and press DELETE in the pop-up box to confirm the deletion.

- Repeat steps 5 to 11 for all the node pools that you want to reconfigure in the selected cluster.
- Repeat steps 4 to 12 for all the clusters you want to reconfigure in the selected project.
- If you have multiple projects, repeat steps 2 to 13 for each project in your GCP console.
