This plugin ensures that the AWS Config service is configured to include Global resources within your AWS account.
Risk Level: Low
Description
This plugin ensures that the AWS Config service is configured to include Global resources within your AWS account. Since global resources such as IAM users, groups and roles are not tied to a specific AWS region, their configuration changes will not be recorded by AWS Config if this option is not enabled.
About the Service
AWS Config: AWS Config simplifies assessment, auditing and evaluation of the AWS resources’ configurations. It provides a detailed report on the relationship between various AWS resources based on their configuration. Apart from monitoring, AWS Config also determines the overall compliance based on the settings specified in your internal policies.
Impact
If the option is not enabled to include global resources, critical configuration changes for global services will not be recorded by AWS Config. In order to have complete visibility of your configuration changes, it is recommended to include global services for all active recorders.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the AWS Config console. You can use this link (https://console.aws.amazon.com/config) to navigate directly if already logged in.
- Scroll down and select Settings from the left navigation pane.
- From the General Settings, check the option for Include global resources (e.g., AWS IAM resources). If it is left unchecked, the vulnerability exists.
- Repeat steps for all the regions you want to investigate.
Steps for Remediation
On the Settings page, within Resource types to record section, check if Include global resources (e.g., AWS IAM resources) setting is enabled.
- Log In to your AWS Console.
- Open the AWS Config console. You can use this link (https://console.aws.amazon.com/config) to navigate directly if already logged in.
- Scroll down and select Settings from the left navigation pane.

- Ensure that the recoding is currently on. Click on the Edit button from the top right corner.
- From the General Settings, check the option for Include global resources (e.g., AWS IAM resources).
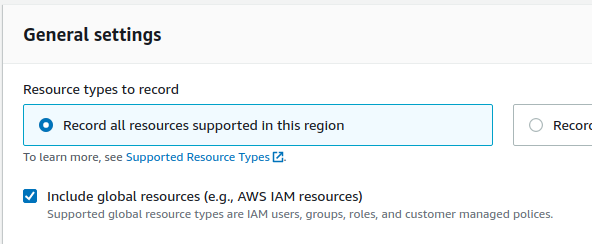
- Click on Save after making all the changes.
- Repeat steps for all the vulnerable regions.
