Risk Level: Medium
Description
This plugin guarantees that DNS Security isn't utilizing the RSASHA1 calculation for key or zone marking. DNS Security is a component that confirms all reactions to space name queries. This keeps aggressors from submitting DNS capturing or man-in-the-middle assaults.
About the Service
Google Cloud Load Balancing:
The Domain Name System Security Extensions (DNSSEC) is an element of the Domain Name System (DNS) that validates reactions to space name queries. It doesn't give security insurances to those queries, however keeps aggressors from controlling or harming the reactions to DNS demands. For full DNSSEC insurance, you should utilize a DNS resolver that approves marks for DNSSEC-marked areas. You can empower approval for individual frameworks or your neighbourhood storing resolvers assuming you oversee your organization's DNS administrations. To know more about GCP Cloud DNS click here.
Impact
DNS is an acronym for Domain name System. Despite the fact that DNS isn't straightforwardly identified with your Internet speed, it can impact how quick a singular site page shows up on your PC. When an association has been set up, however, it ought not to influence download speeds. To correct your switch's DNS servers nonetheless, this can assist with working on your general speed. This plugin is meant to ensure that DNS Security is enabled on all managed zones. DNS Security is a feature that authenticates all responses to domain name lookups. This prevents attackers from committing DNS hijacking or man in the middle attacks. The prescribed activity for the equivalent is to ensure DNSSEC is empowered for all oversaw zones in the cloud DNS administration.
Steps to Reproduce
Using GCP Console-
In order to ensure or determine, the type of DNSSEC Zone-Signing Key algorithm configured for all your DNS managed zones, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate.
- From the Navigation Menu on the left, you may find the Networking section.
- Click on the Network Services subsection under Networking.
-png-May-07-2022-06-55-51-39-AM-1.png)
- Under the Network Services navigation panel, you may find Cloud DNS as shown in the figure below.
-png-May-07-2022-06-55-59-18-AM-1.png)
- Click on the Cloud DNS navigation link and a Cloud DNS Page will appear on the screen. Click to open directly from here.
- On the Cloud DNS page, click on the Zones Tab, present at the top of the navigation bar. This is to access the list of all the Zone Names present within the Google Cloud DNS in your GCP Project.
-png-May-07-2022-06-56-10-25-AM-1.png)
- The list of all the DNS managed Zones will be displayed.
-png-May-07-2022-06-56-17-63-AM-1.png)
- Under the Filter option box, choose the Zone Name, DNS name or description, and Type attributes and fill them with appropriate values respectively as shown.
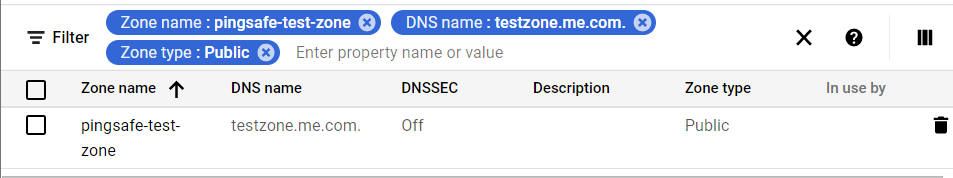
- Choose the “zone name” of the zone you want to examine. A new page with all the zone details will be opened up.
- Click on the Equivalent REST link available at the bottom of the details page. A new dialog box will appear on the screen with a JSOn file in it of that selected zone.
-png-May-07-2022-06-56-40-44-AM-1.png)
- Check for the algorithm property in the algorithm code. If the “algorithm” property is set to “RSASHA1”, then the DNSSEC ZSK algorithm is considered to be unsecured and deprecated. Thus, it should not be used until it is must to required for severe reasons and requirements.
- You may repeat steps 8-12 for other zones in your GCP Project.
- You may repeat the above-mentioned steps to check for the other GCP projects/folders in your organization.
Steps for Remediation
Using GCP Console-
In order to configure the Zone Signing Key (ZSK) algorithm used by the DNSSEC feature in your Google Cloud Platform (GCP) project, follow the steps mentioned below:
Note: Changing the DNSSEC Key algorithm is not possible using the GCP console.
- In case, the DNSSEC feature is enabled for that DNS Zone you are examining, then again disable the feature, now make the required changes, and then enable the configurations.
- Now, in the Windows/Linux/macOS CLI, run the command dns managed-zones update using the public DNS Zone name, for which you want to reconfigure as identifier parameter.
- The commands are:
-png-May-07-2022-06-56-54-87-AM-1.png)
- The command output will return the update process status for that selected DNS Zone:
-png-May-07-2022-06-57-02-29-AM-1.png)
- The upheld DNSSEC calculation choices and key lengths are accessible on this Google Cloud documentation page. These are likewise recorded in the accompanying table:
-png-May-07-2022-06-57-09-41-AM-1.png)
- Now, run dns managed-zones update command on your Windows/macOS/Linux, by utilizing the name of the public DNS zone that you need to reconfigure as identifier boundary, to change the Zone-Signing Key (ZSK) calculation by refreshing the DNSSEC highlight design not long prior to empowering it for the chose zone.
- This command will set the Zone-Signing-Key algorithm to “RSASHA256” and the length of the key equal to 1024.
-png-May-07-2022-06-57-17-12-AM-1.png)
- The command output will return the update process status for that selected DNS Zone:
-png-3-1.png)
- Repeat the above steps to reconfigure the DNSSEC ZSX algorithm for other public DNS zones in your GCP Project.
