This plugin ensures that the latest version of Kubernetes is installed on EKS clusters.
Risk Level: High
Description
This plugin ensures that the latest version of Kubernetes is installed on EKS clusters. With Amazon EKS, you can create Kubernetes clusters with latest version support. The latest versions of Kubernetes contain bug fixes and security patches. It is recommended that you use the latest version of Amazon EKS.
About the Service
Amazon EKS: Amazon Elastic Kubernetes Service (Amazon EKS) is a managed container service for running and scaling Kubernetes applications in the cloud or on premises. With Amazon EKS, you can take advantage of all the performance, scale, reliability, and availability of AWS infrastructure, as well as integrations with AWS networking and security services.
Impact
Latest version of Kubernetes installed ensures that your cluster is free from major bugs and security threats.
Outdated and deprecated versions can make your applications incompatible and also open doors for attackers to exploit the security vulnerabilities.
Steps to Reproduce
Using AWS Console-- Log In to your AWS Console.
- Open the Amazon EKS console. You can use this link (https://console.aws.amazon.com/eks) to navigate directly if already logged in.
- From the list of clusters available, check the Kubernetes version of the cluster you wish to examine. For the list of latest versions, check this link.
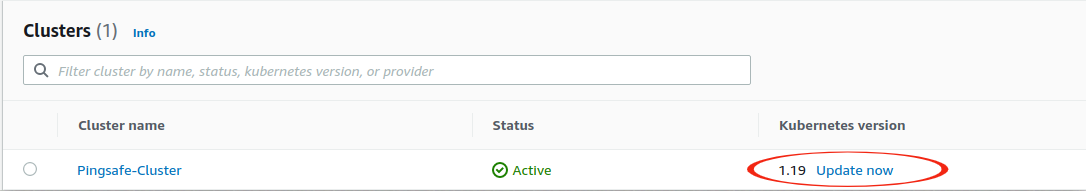
- If AWS says it to Update now, the version needs to be updated.
- Repeat the steps from 3 to 4 for all the clusters you wish to investigate.
Steps for Remediation
Upgrade the version of Kubernetes on all EKS clusters to the latest available version.
- Log In to your AWS Console.
- Open the Amazon EKS console. You can use this link (https://console.aws.amazon.com/eks) to navigate directly if already logged in.
- From the list of clusters available, click on Update now in the Kubernetes version cloumn of the vulnerable cluster.

- Select the available versions from the drop-down box, then click on Update.
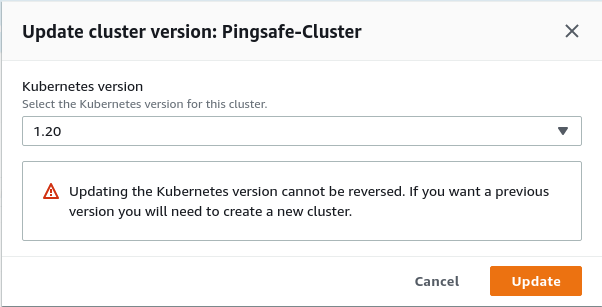
- Repeat the steps from 3 to 4 for all the vulnerable clusters.
References
- https://aws.amazon.com/eks/features/
- https://docs.aws.amazon.com/eks/latest/userguide/kubernetes-versions.html
