Risk Level: Medium
Description:
This plugin guarantees that EKS clusters are set up to use KMS to encrypt Kubernetes secrets in the envelope. To comply with security best practices for apps that contain sensitive data, Amazon EKS clusters should be configured to enable envelope encryption for Kubernetes secrets.
About the Service :
Amazon Elastic Kubernetes Service (Amazon EKS) is a managed container service for running and scaling Kubernetes applications in the cloud or on-premises. With Amazon EKS, you can take advantage of all the performance, scale, reliability, and availability of AWS infrastructure, as well as integrations with AWS networking and security services.
Impact :
In case the secrets are not encrypted the sensitive data will be exposed to threats and security best practices will not necessarily be followed. Moreover, the KMS key is a part of a defence in depth security strategy.
Steps to reproduce :
- Log In to your AWS Console.
- Open the Amazon EKS console. You can use this link (https://console.aws.amazon.com/eks) to navigate directly if already logged in.
- From the list of clusters available in the Clusters under Amazon Container Services, click on the Cluster name of the cluster you wish to investigate.
- Move to the Details tab of the cluster configuration page and then navigate to the Secrets Encryption.
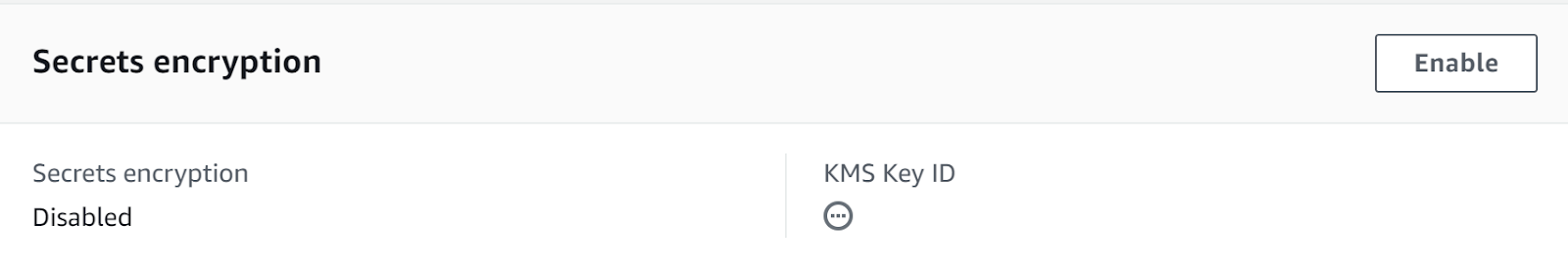
- Check if the secret encryption is enabled or not. Since it is not encrypted hence it is not following the best security practices.
- Repeat steps for other clusters as well.
Steps for remediation :
- Log In to your AWS Console.
- Open the Amazon EKS console. You can use this link (https://console.aws.amazon.com/eks) to navigate directly if already logged in.
- From the list of clusters available in the Clusters under Amazon Container Services, click on the Cluster name of the cluster you wish to investigate.

- Move to the Details tab of the cluster configuration page and then navigate to the Secrets Encryption.

- Check if the secret encryption is enabled or not. Since it is not encrypted hence it is not following the best security practices.
- Click on Enable to enable the secret encryption, select the KMS key and then click Enable.
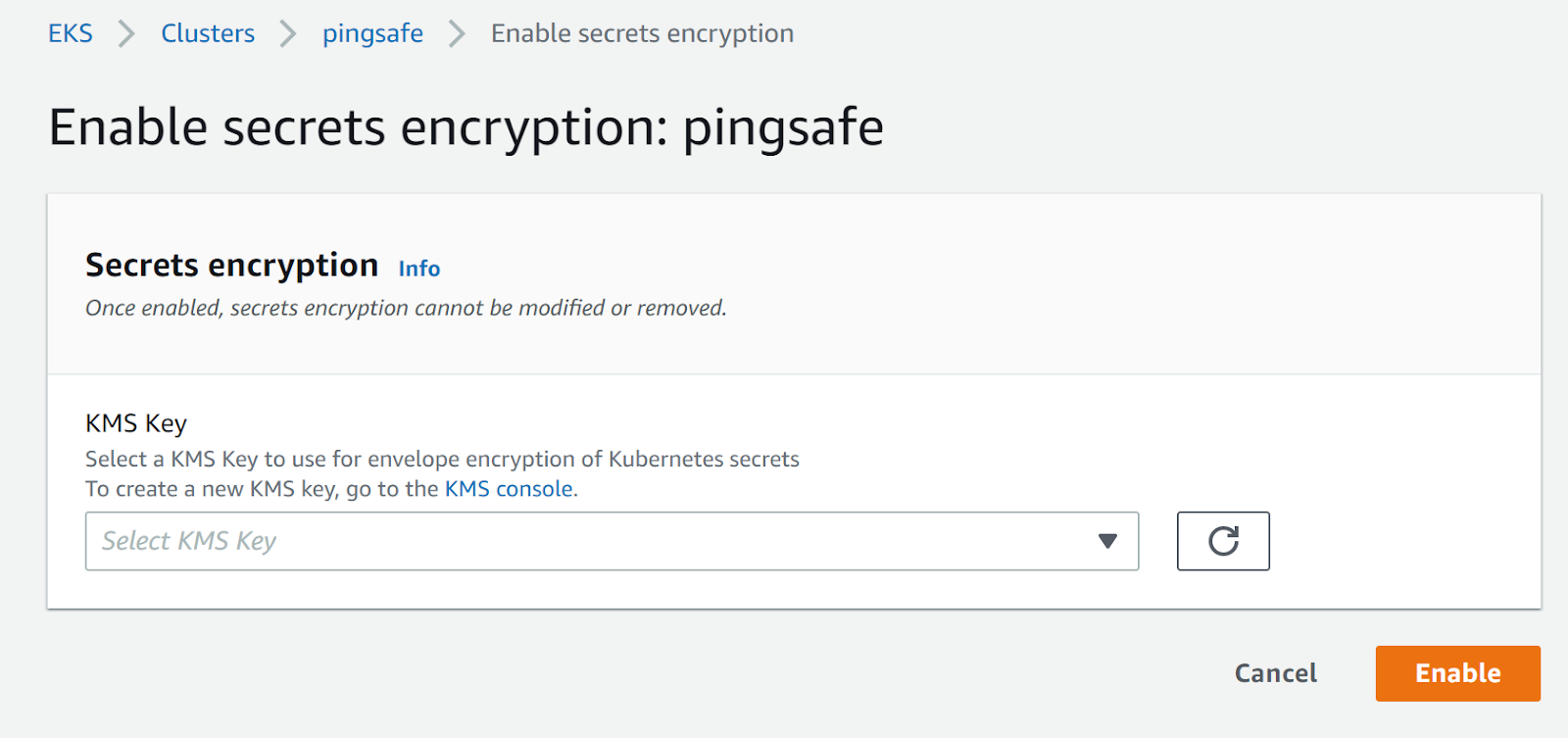
- Repeat steps for other clusters as well.
References:
