This plugin ensures that the EKS control plane only allows incoming data traffic on port 443.
Risk Level: High
Description
This plugin ensures that the EKS control plane only allows incoming data traffic on port 443. The EKS control plane only requires access to port 443. Security groups for the control layer should not add any access from additional ports.
About the Service
Amazon EKS: Amazon Elastic Kubernetes Service (Amazon EKS) is a managed container service for running and scaling Kubernetes applications in the cloud or on premises. With Amazon EKS, you can take advantage of all the performance, scale, reliability, and availability of AWS infrastructure, as well as integrations with AWS networking and security services.
Impact
Open ports inside your Amazon EKS security groups allows attackers to scan ports and identify applications and services running on your EKS clusters.
This can enable them to exploit vulnerabilities present in your EKS cluster. It is highly recommended to only allow inbound traffic via port 443 using security groups.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon EKS console. You can use this link (https://console.aws.amazon.com/eks) to navigate directly if already logged in.
- From the list of clusters available, click on the Cluster name of the cluster you wish to investigate.
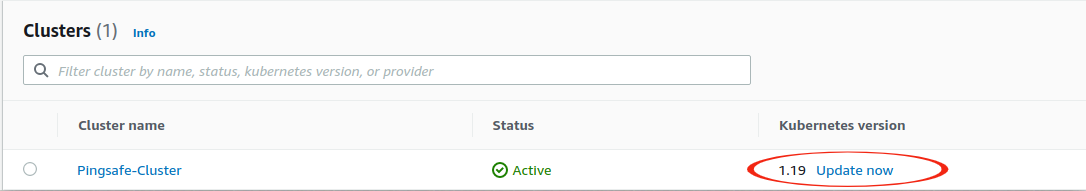
- Move to the Networking tab.
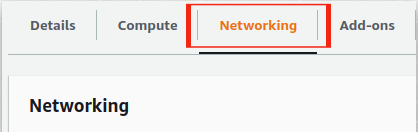
- Check the Security Groups section. Click on the security group attached.
- This will open a new tab with the security group displayed. Move to the Inbound Rules section.

- In the rules, check the Type, Protocol and Port Range. If the security group allows incoming traffic from ports other than 443, it is vulnerable.
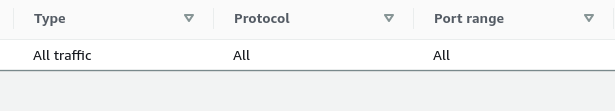
- Repeat the steps from 3 to 7 for all the clusters you wish to investigate.
Steps for Remediation
Configure security groups for the EKS control plane to allow access only on port 443.
- Log In to your AWS Console.
- Open the Amazon EKS console. You can use this link (https://console.aws.amazon.com/eks) to navigate directly if already logged in.
- From the list of clusters available, click on the Cluster name of the cluster you wish to investigate.

- Move to the Networking tab.

- Check the Security Groups section. Click on the security group attached.
- This will open a new tab with the security group displayed. Move to the Inbound Rules section.

- Click on Edit Inbound Rules.
- Delete all the vulnerable rules. And add the rule which allows access though TCP protocol to port 443.
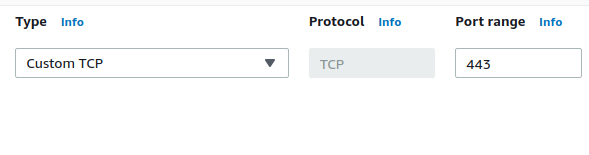
- Click on the Save rules button after doing the changes.
- Repeat the steps from 3 to 7 for all the vulnerable clusters.
References
