This plugin ensures global access is not enabled on Amazon Elasticsearch domains via access policies.
Risk Level: High
Description
This plugin ensures global access is not enabled on Amazon Elasticsearch domains via access policies. Policies are an important way to secure your OpenSearch domains. They must be properly set up to deny public access to the domains.
Configuration Parameters
ElasticSearch Domain Policy Allowed Condition Keys: The parameter holds the list of AWS IAM condition keys which by default has values, 'aws:PrincipalArn', 'aws:PrincipalAccount', 'aws:PrincipalOrgID', 'aws:SourceAccount', 'aws:SourceArn', 'aws:SourceOwner', 'kms:CallerAccount' and 'kms:ViaService'. The values provided in the parameter will not be scanned by PingSafe.
About the Service
Amazon OpenSearch: With Amazon OpenSearch, one can analyze, query and visualize petabytes of text and unstructured data. It makes the complex process of performing interactive log analytics, real-time application monitoring, website search, an easy process. Apart from this, Amazon OpenSearch also provides the possibility to capture observability logs and metrics.
Impact
Publically accessible OpenSearch domains are a serious security threat to the cloud infrastructure. Using policies, it can be made public. Such public domains are exploited by attackers to gain access to critical logs and queries generated by the service.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon OpenSearch Console. You can use this link (https://console.aws.amazon.com/esv3/) to navigate directly if already logged in.
- From the left navigation pane, click on Domains from the left panel.
- A list of domains will be displayed. Select the domain you want to examine by clicking on it’s name.
- Move to the Security Configurations tab.
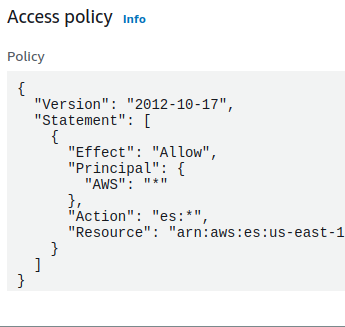
- Examine the Access policy. If the principal is set to “*” and the effect is “Allow”, the vulnerability exists. Also check for the whitelisted conditions which secure the domain.
- Repeat steps 3 to 6 for all the domains you wish to examine.
Steps for Remediation
Modify Elasticsearch domain access policy to remove global access. If policy is already restricted using conditions then make sure to whitelist condition keys in plugin configuration.
- Log In to your AWS Console.
- Open the Amazon OpenSearch Console. You can use this link (https://console.aws.amazon.com/esv3/) to navigate directly if already logged in.
- From the left navigation pane, click on Domains from the left panel.

- A list of domains will be displayed. Select the vulnerable domain by clicking on it’s name.
- Move to the Security Configurations tab.

- Click on the Edit button from the top-right corner.
- There can be four ways to secure the domain-
- Set the Effect element to “Deny”, instead of Allow.
- Change the Principal element to known IP addresses, or known AWS ARN.
- Add whitelisted Conditions to the statement to secure it.
- If the policy is already secured with the condition, add them to the plugin configuration parameters.
- Repeat steps 3 to 7 for all the insecure domains.
