Risk Level: Low
Description:
This plugin ensures Firehose Delivery Stream encryption is enabled. The data sent through the process in AWS Firehose Delivery Stream must be encrypted in order to secure the data flow. It is recommended to use customer-managed keys instead of default keys to have more flexibility.
About the Service :
Amazon Kinesis is a service that provides an easy process to collect, analyze real-time streaming data and derive valuable insights from it. As per the AWS description, it is highly scalable and can help you ingest real-time data such as video, audio, application logs, website clickstreams, and IoT telemetry data for machine learning, analytics, and other applications. Kinesis delivers real-time insights instead of waiting for the stream to end to come up with analytics.
Impact :
It is highly recommended to properly encrypt AWS Kinesis Firehose Delivery Stream with customer-managed KMS keys. AWS Customer managed keys provide better flexibility to increase encryption level and thus, deliver better security for the delivery stream. The default keys provide a minimal level of security.
Steps to reproduce :
- Log in to AWS Console.
- Navigate to the Kinesis Dashboard. You can use the link (https://console.aws.amazon.com/firehose) if already logged in.
- Select Delivery Streams in the left navigation panel.
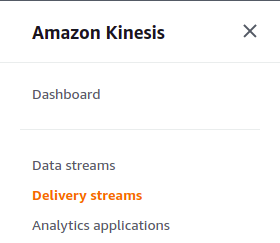
- Click on the stream that you want to examine by clicking on its Name.
- Move to the Configuration tab.

- Scroll down to the Server-side encryption (SSE) section and check if it is enabled or not. If the value is set to enabled, but the Encryption type is “AWS-owned CMK” the vulnerability exists.
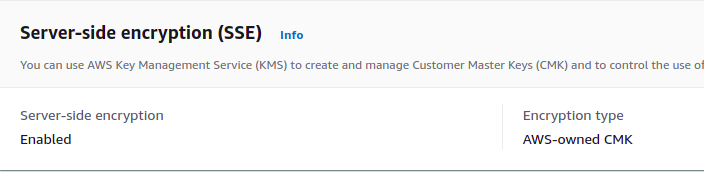
- Repeat steps for other delivery streams.
Steps for remediation :
Enable encryption using CMK KMS for all Firehose Delivery Streams:
- Log in to AWS Console.
- Navigate to the Kinesis Dashboard. You can use the link (https://console.aws.amazon.com/firehose) if already logged in.
- Select Delivery Streams in the left navigation panel.

- Click on the vulnerable stream by clicking on its Name.
- Move to the Configuration tab.

- Scroll down to the Server-side encryption (SSE) section and click on Edit.
- Select CMK KMS and specify the KMS key ARN you wish to use for encryption.
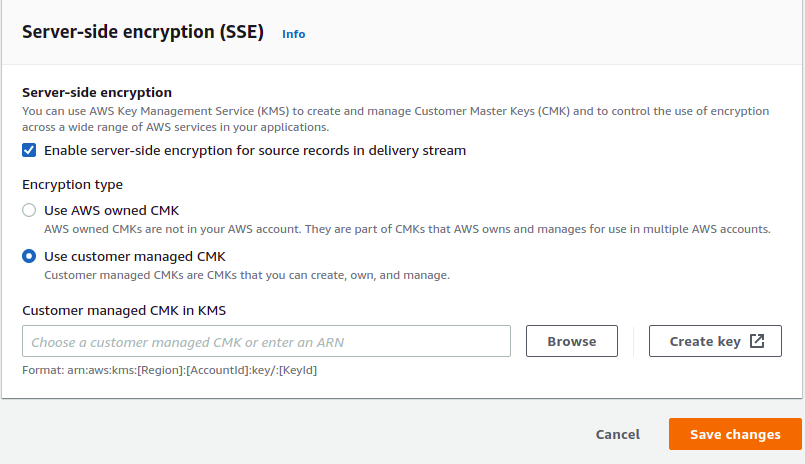
- Click on Save changes after completing the configuration.
- Repeat steps for other delivery streams.
