RISK LEVEL
Medium
DESCRIPTION
This plugin ensures that firewall rule logging for each firewall rule whose connections you need to log is enabled, regardless of the action (allow or deny) or direction (inbound or outbound) of the rule. Once the VPC firewall rule logging is enabled, Google Cloud creates a connection record each time the rule allows or denies traffic. You can use Google Cloud Logging to view these records and export the log files to any destination supported by the service. Each connection record contains the source and destination IP addresses, the protocol, and port(s) used the connection date and time, and a reference to the firewall rule that managed the traffic.
ABOUT THE SERVICE
Google Cloud VPC:
According to Google definitions, VPC which stands for a Virtual Private Network is a virtual version of a physical layer, implemented inside of Google’s Production Network, using Andromeda. The Virtual Private Network offers various features including, connectivity for your Compute Engine Virtual Machine (VM) instances, Google Kubernetes Engine (GKE) clusters, etc. It helps to load balancing and proxy systems for internal system affairs. It even allows assistance in the traffic from Google Cloud external load to backends. Users can have the advantage of containing multiple VPC Networks over a single GCP Project. Various default features are already enabled with VPC Networks, for instance, logging metadata is incorporated into your Virtual Private Cloud (VPC) firewall log files. Click here to read more about Google Cloud VPC Networks.
IMPACT
Firewall rule logging permits you to confirm, break down, and review the impacts of your VPC firewall rules on your cloud assets. For instance, you can decide whether a firewall rule intended to deny network traffic is working as planned. This sort of logging is likewise valuable on the off chance that you really want to decide the number of associations is impacted by a given VPC firewall rule.
Empower Virtual Private Cloud (VPC )firewall rule logging for every firewall rule whose associations you really want to log, paying little mind to the activity (permit or deny) or bearing (inbound or outbound) of the standard. When the VPC firewall rule logging is empowered, Google Cloud makes an association record each time the standard permits or denies traffic. You can utilize Google Cloud Logging to see these records and product the log documents to any objective upheld by the assistance. Every association record contains the source and objective IP addresses, the convention and port(s) utilized, the association date and time, and a reference to the firewall decide that dealing with the traffic.
STEPS TO REPRODUCE
Using GCP Console-
In order to ensure if logging is enabled or authorized for the Virtual Private Cloud Network firewall rules, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.
- From the Navigation Menu on the left, you may find the Networking section.
- Click on the VPC Network subsection under Networking.
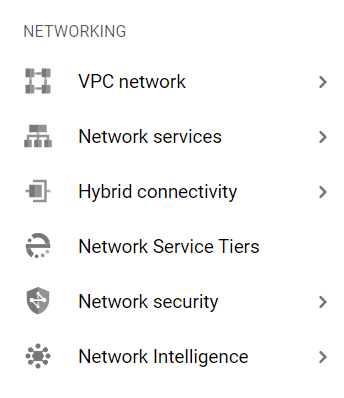
- Under the VPC Network navigation panel, you may find Firewall as shown in the figure below.
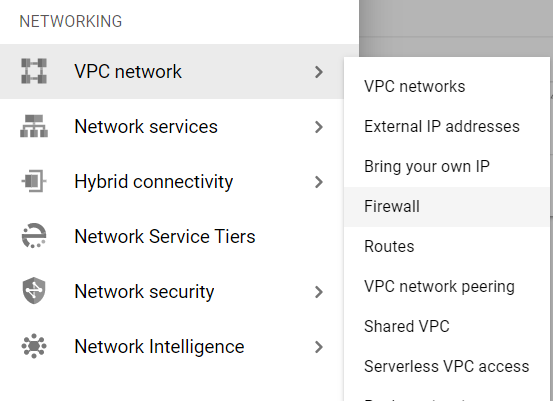
- Click on the Firewall navigation link and a VPC Network Firewall dashboard will appear on the screen. Click to open directly from here.
- On the Firewall dashboard, reach the Filter option in the table and click on it.
- Set the values of properties in the Filter option as:
- Disabled: False
- Disabled: False
- Under Step 8.a, by setting Disabled property to False, it will list down all the egress and ingress rules enabled in your selected GCP Project for all the resources.
- Among the filtered list of firewall rules, click and open the firewall rule, you want to examine.
- Once you click a page will open for your selected firewall rule. Check out the Logs section available on the top.
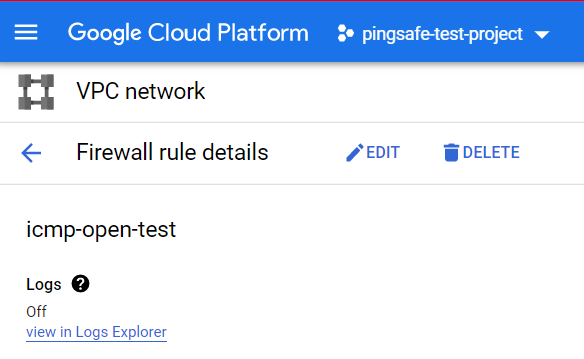
- If the Logs section is set to OFF, then the rule logging is not enabled in the VPC network firewall rule
- This way you can check out if logging is enabled for the Virtual Private Cloud Network firewall rules.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.
STEPS FOR REMEDIATION
Using GCP Console
In order to enable the logging for firewall rules in your GCP Virtual Private Cloud (VPC) network, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find the Networking section.
- Click on the VPC Network subsection under Networking.

- Under the VPC Network navigation panel, you may find Firewall as shown in the figure below.

- Click on the Firewall navigation link and a VPC Network Firewall dashboard will appear on the screen. Click to open directly from here.
- On the Firewall dashboard, reach the Filter option in the table and click on it.
- Set the values of properties in the Filter option as:
- Disabled: False

- Disabled: False
- Under Step 8.a, by setting Disabled property to False, it will list down all the egress and ingress rules enabled in your selected GCP Project for all the resources.
- Among the filtered list of firewall rules, click and open the firewall rule, you want to examine.
- Once you click a page will open for your selected firewall rule. Check out the Logs section available on the top.

- Click on the Edit Button to reconfigure the settings. Change the Logs option to ON status.

- After ensuring your edited options, click on SAVE Button to apply changes and go back to the previous page.
- You may repeat steps 10-12 for other firewall rules in your GCP Project.
- You may repeat the above steps for other GCP Projects under your organization.
