The plugin ensures that the password policy guarantees that the previous password is not reused.
Risk Level: Medium
Description:
The plugin ensures that the password policy guarantees that the previous password is not reused. Strong password policies provide minimum duration, expiry, reuse, and use of symbols.
PingSafe strongly recommends increasing the minimum number of previous passwords that can be reused to the minimum threshold specified.
Configuration Parameters
Password Reuse Threshold: The enforcement of the AWS IAM password's strength is critical when it comes to keeping your AWS account safe and secure. The parameter holds the threshold limit for a previous password to be reused. PingSafe will raise an issue when the password reuse policy remembers fewer than this many past passwords. By default, the value is 5.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
The enforcement of the AWS IAM password's strength, pattern, and rotation are critical when it comes to keeping your AWS account safe and secure. The absence of a strong password policy will increase the risk of password guessing and brute-forcing.
Steps to reproduce :
- Login to AWS Management Console.
https://console.aws.amazon.com/ - Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam
- Select Account Settings under Access Management.
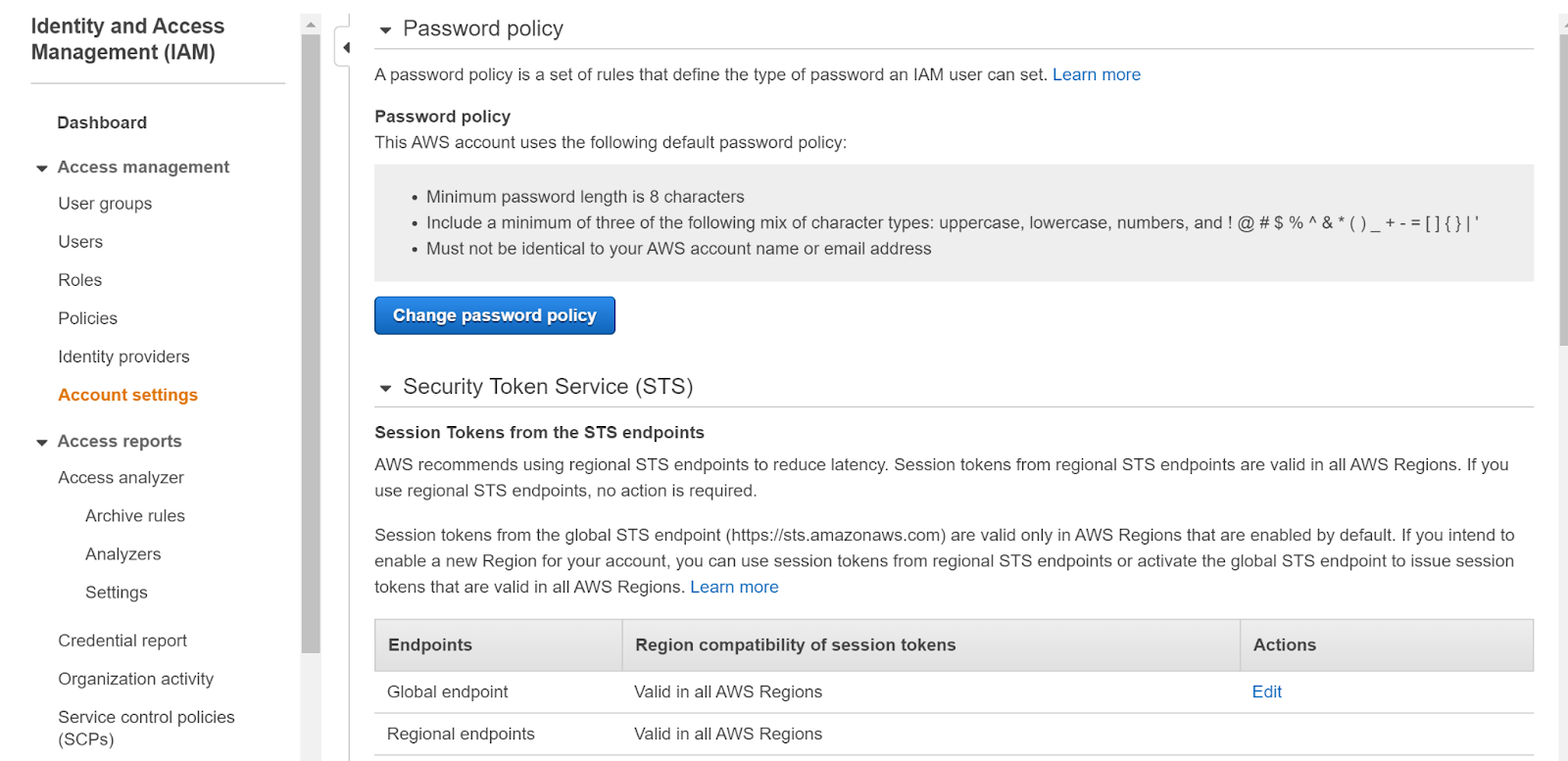
- This page displays a section named Password policy which shows the password policy of the account.
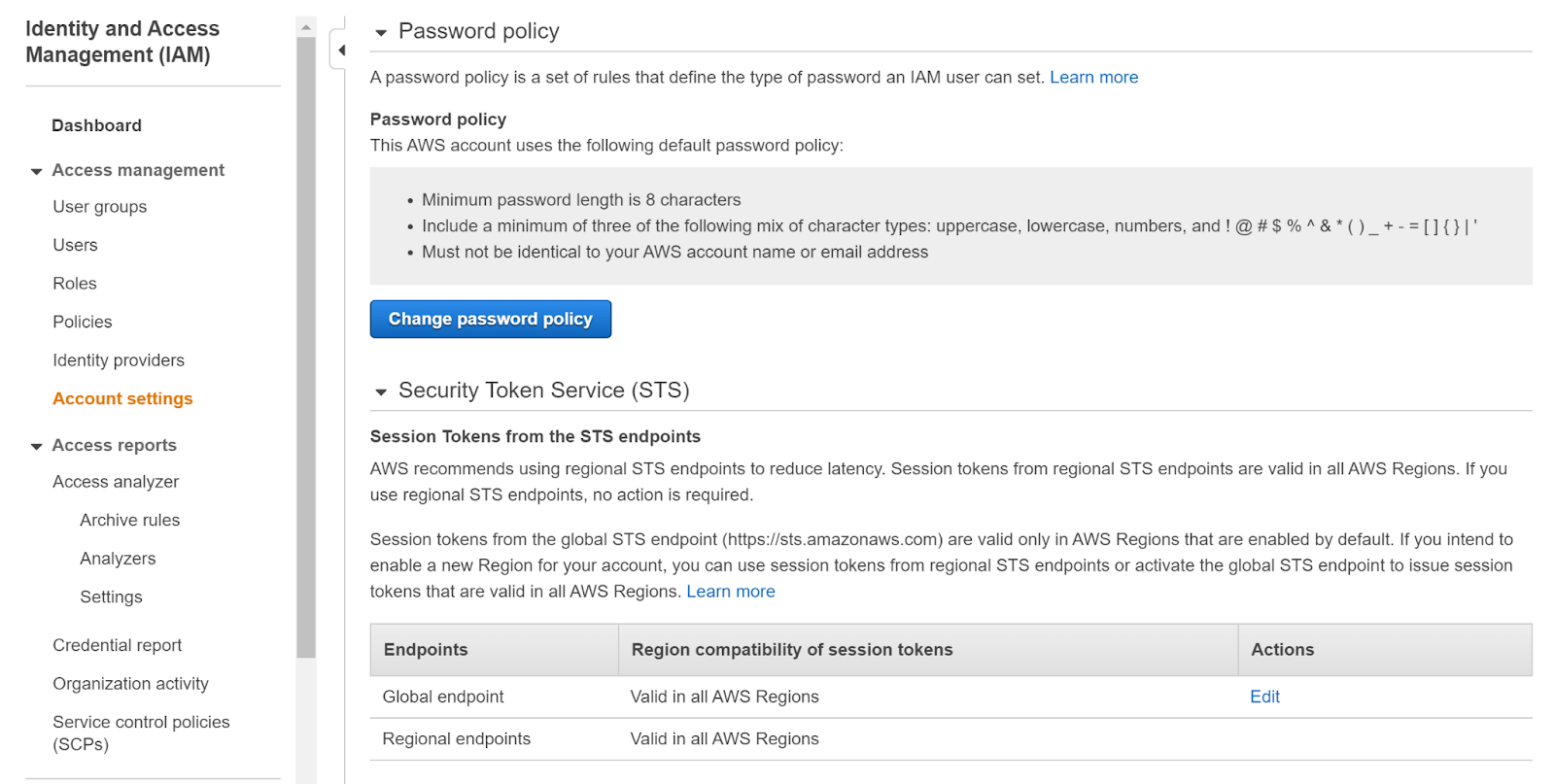
- This page clearly reflects that the password policy does not include the password reuse prevention policy making it a weak password policy.
- This presses the need to set the appropriate password policy of the account to keep the security in check.
- Repeat steps for other accounts as well.
Steps for remediation :
- Login to AWS Management Console.
https://console.aws.amazon.com/ - Navigate to the IAM dashboard.
https://console.aws.amazon.com/iam
- Select Account Settings under Access Management.

- This page displays a section named Password policy which shows the password policy of the account.

- This page clearly reflects that the password policy does not include the password reuse prevention policy making it a weak password policy.
- This presses the need to set the appropriate password policy of the account to keep the security in check.
- Select the Change password policy button. In the Set Password Policy tab that appears check Prevent password reuse and then enter at least the minimum threshold in the box that appears. Finally, click on Save changes.
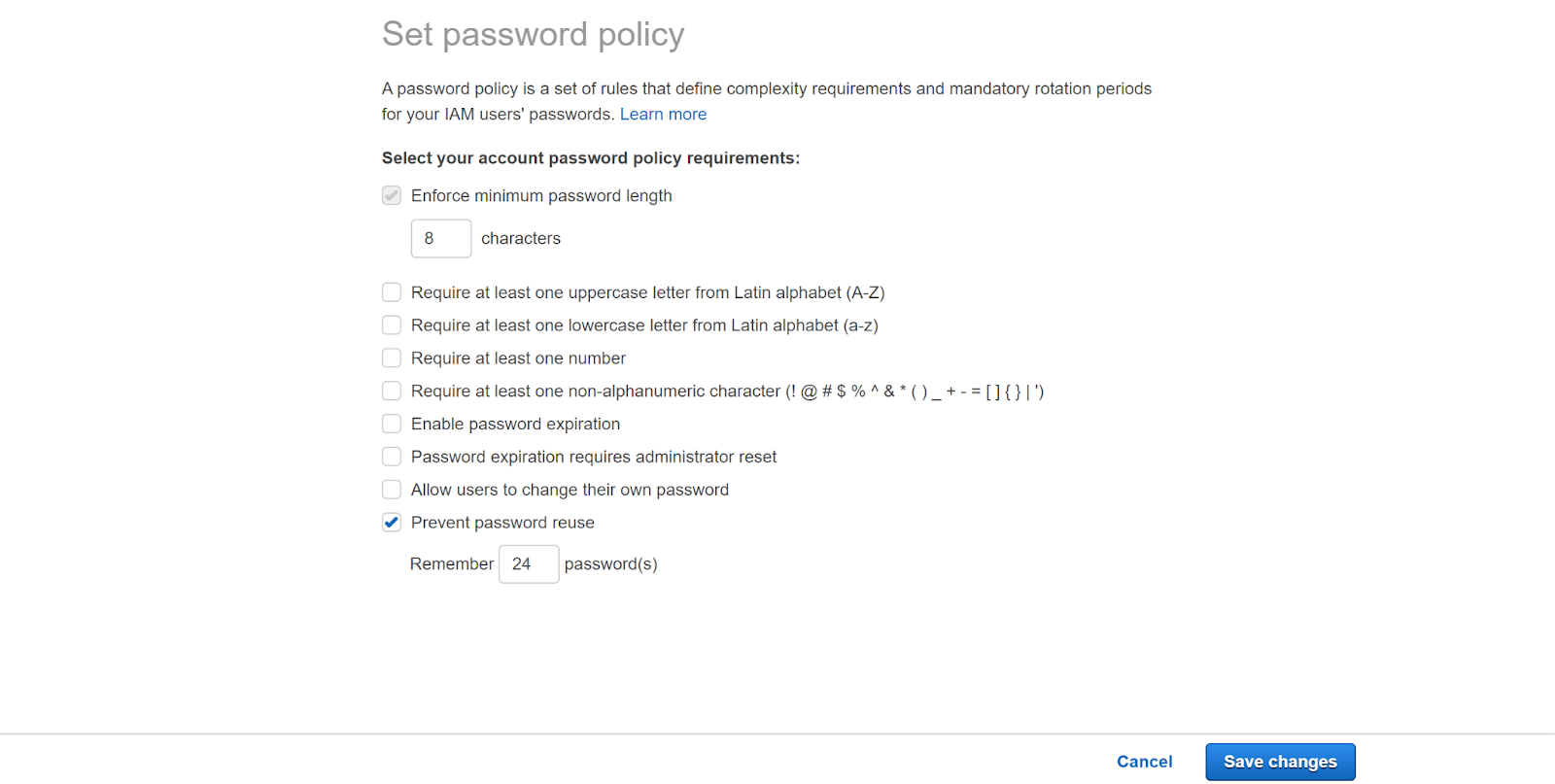
- Repeat steps for other accounts with the same problem as well.
References:
