Ensures that the KMS keys are not accessible to the public.
Risk Level: High
Description
The access for the Google Cloud KMS resources is managed by IAM roles. This plugin ensures that all the “allAuthenticatedUsers” and “allUsers” IAM member bindings are removed so that the KMS keys do not have anonymous or public accessibility.
About the Service
Google Cloud Key Management Service (KMS):
The Google Cloud Key Management Service (KMS) allows you to manage your encryption keys in the cloud. You can use this service to create, rotate, utilize, and remove keys. To produce a key and assure its security, Google employs a number of cryptographic algorithms. Users can then perform operations on Google Cloud services and data based on their role and the access granted to them. To know more, read here.
Impact
If “allAuthenticatedUsers” and “allUsers” are granted access to the KMS keys, all the users will be able to access the keys. As a result, the data's security and privacy are at risk. To ensure that the principle of least privilege is followed, the access permissions need to be given only to the required users.
Steps to Reproduce
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select the GCP project you want to investigate.
- From the navigation panel on the left side of the console, go to Security under the More products section and select Key management. You can click this link here to navigate directly if you’re already logged in.
-png-4-1.png)
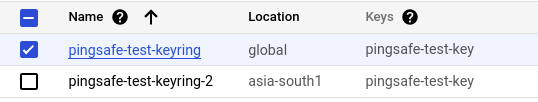
- In the KEY RINGS tab, select the key ring you want to verify from the list of key rings available.
- Choose the key you want to investigate in the KEYS tab of the selected key ring.
- Click on the SHOW INFO PANEL button, available on the right corner of the top bar, and go to the PERMISSIONS tab to see the permissions.
-png-3-1.png)
- Turn off the Show inherited permissions toggle bar.
-png-2-1.png)
- Set Role/Principal to allAuthenticatedUsers and allUsers in the Filter box as shown in the screenshot below.
-png-2-1.png)
If one or more results are displayed, the selected key is publicly accessible. - Repeat the above steps for all the other keys present in the selected key ring.
- If you have multiple key rings, repeat the steps for each key ring in your GCP Console
Steps for Remediation
Determine whether or not you truly require the keys to be publicly accessible. If not, make the necessary changes using the steps given below.
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select your desired GCP project.
- From the navigation panel on the left side of the console, go to Security under the More products section and select Key management. You can click this link here to navigate directly if you’re already logged in.
-png-May-07-2022-05-31-57-57-AM-1.png)
- In the KEY RINGS tab, select the key ring you want to verify from the list of key rings available. (In case you aren’t sure which key ring needs to be configured, follow the steps to reproduce listed above to determine which key ring to choose.)
-png-1-1.png)
- Choose the key you want to investigate in the KEYS tab of the selected key ring.
- Click on the SHOW INFO PANEL button, available on the right corner of the top bar, and go to the PERMISSIONS tab to see the permissions.
-png-Jun-14-2022-02-31-17-51-PM.png)
- Turn off the Show inherited permissions toggle bar.
-png-Jun-14-2022-02-31-14-34-PM.png)
- Set Role/Principal to allAuthenticatedUsers and allUsers in the Filter box as shown in the screenshot below.
-png-Jun-14-2022-02-31-17-90-PM.png)
- Click on the delete icon next to the member name you wish to delete. Click REMOVE in the confirmation pop-up box to confirm the deletion.
- Repeat steps 5 to 9 for all the keys you want to recreate in the selected key ring.
- If you have multiple key rings, repeat steps 4 to 10 for each key ring you want to recreate in your GCP console.
