- CNS Policies
- Azure Knowledge Base
- Azure Key Vaults
-
AWS Knowledge Base
- Amazon EKS
- Amazon RDS
- Amazon Kinesis
- AWS Organizations
- Amazon SQS (Simple Queue Service)
- AWS Cloudtrail
- AWS Certificate Manager
- AWS IAM
- AWS Workspaces
- Amazon S3
- AWS Systems Manager (AWS SSM)
- Amazon EC2
- Amazon Redshift
- Amazon EMR
- Amazon CloudFront
- Amazon DynamoDB
- Amazon Managed Workflows for Apache Airflow (MWAA)
- Amazon Route 53
- AWS Key Management Service (KMS)
- Amazon CloudWatch
- Amazon ElasticSearch
- AWS Database Migration Service
- AWS Config
- AWS X-Ray
- Amazon API Gateway
- Amazon Athena
- Amazon SageMaker
- AWS Elastic Load Balancing (ELB)
- AWS Lambda
- AWS Auto Scaling
- Amazon GuardDuty
- Amazon Elastic File System (Amazon EFS)
- Amazon Elastic Container Registry (Amazon ECR)
- AWS Glue
- Amazon Simple Notification Service (SNS)
- AWS Elastic Beanstalk
- AWS CodeBuild
- AWS Secrets Manager
- AWS Transfer Family
- Amazon Access Analyzer
-
Azure Knowledge Base
- Container Registries
- Azure Virtual Machines
- Network Security Group
- PostgreSQL
- Azure Monitor
- Azure Security Center
- SQL Databases
- SQL Servers
- Storage Accounts
- Azure Key Vaults
- Load Balancers
- App Services
- Azure Active Directory
- Activity Log
- Azure Policy
- Kubernetes Services
- Azure Resources
- Azure Cosmos DB
- CDN Profiles
- MySQL Servers
- Azure Virtual Network
- Azure Network Watcher
- Azure Cache for Redis
-
GCP Knowledge Base
- Google Cloud VPC
- Google Cloud IAM
- Google Cloud Load Balancing
- Google Cloud Logging
- Google Cloud Kubernetes Engine
- Google Cloud Pub/Sub
- Google Compute Engine
- Google Cloud Key Management Service (KMS)
- Google Cloud DNS
- Google Cloud Storage
- Google Cloud Dataproc
- Google Cloud SQL
- Google Cloud Spanner
- Google Cloud Deployment Manager
- Google Cloud BigQuery
- Google Cloud Dataflow
-
DigitalOcean Knowledge Base
Key Vault Recovery Disabled
Risk Level: Medium
Description
The plugin checks that Purge protection and Soft Delete on all Key Vaults are enabled. In case of losing access to keys, purge protection and soft delete help in reaccessing of keys.
About the Service
Key Vaults: Azure provides a facility to store and manage sensitive data such as certificates, user ids and passwords through key vaults service. The keys are embedded in the URL which reduces the accidental or intentional exposure of the keys.
Impact
In case purge protection and soft delete are not enabled, in case of loss of any vault key, recovery of the particular vault key will not be possible, leading to loss of the sensitive data and other information the key was holding.
Steps to Reproduce
- Log in to the Azure portal.
- Click on Key vaults under Services or type “Key vaults” in the search box.
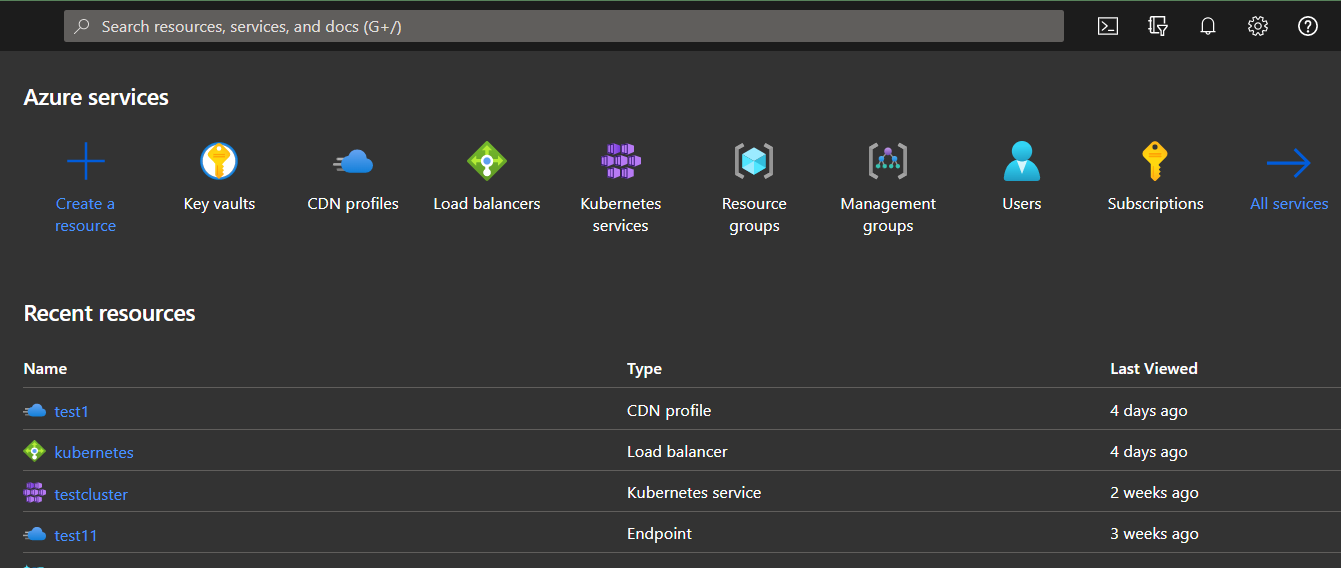
- Select a vault to check for the issue.
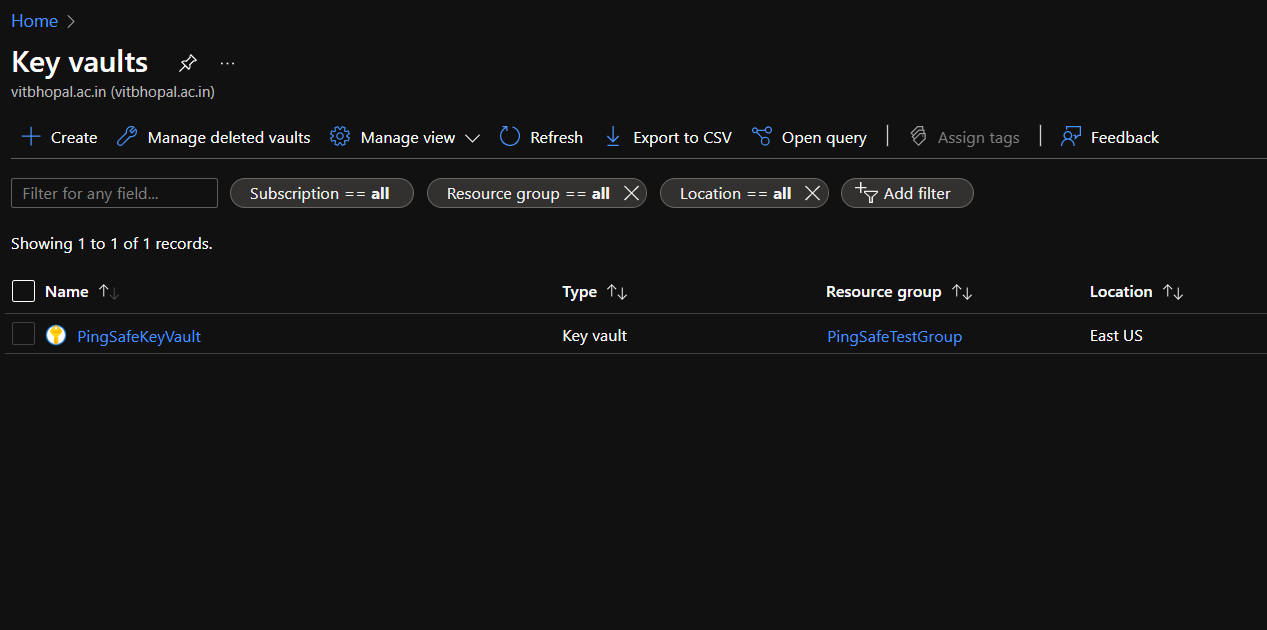
- From the navigation bar, go to the Settings section, click on Properties.
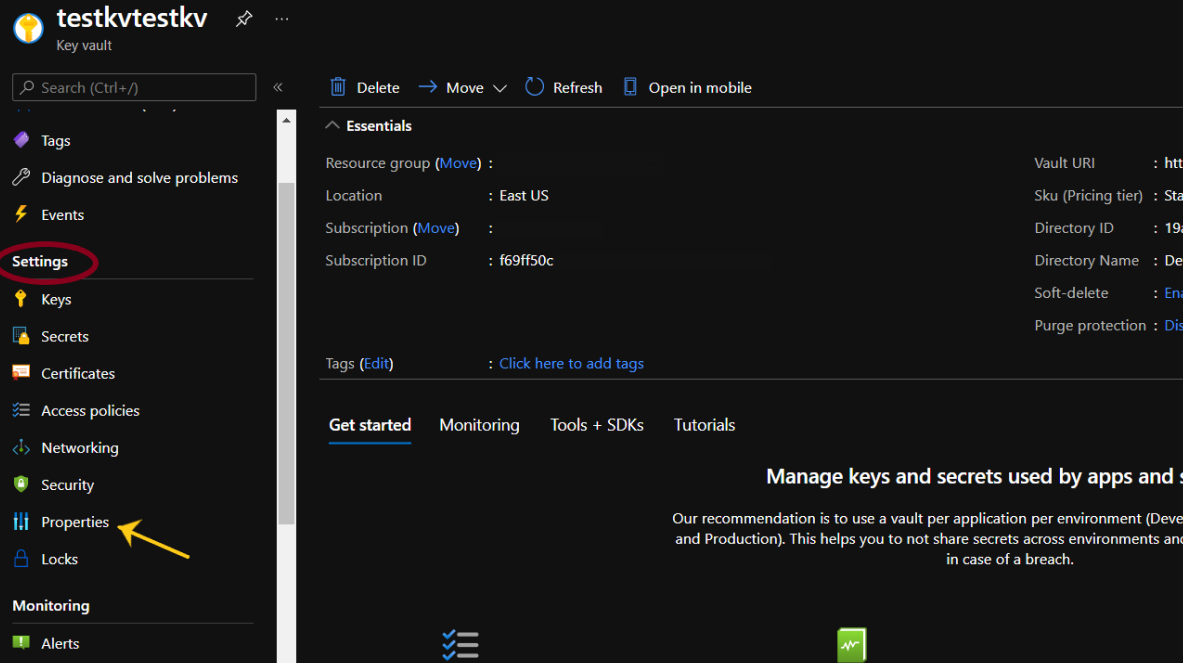
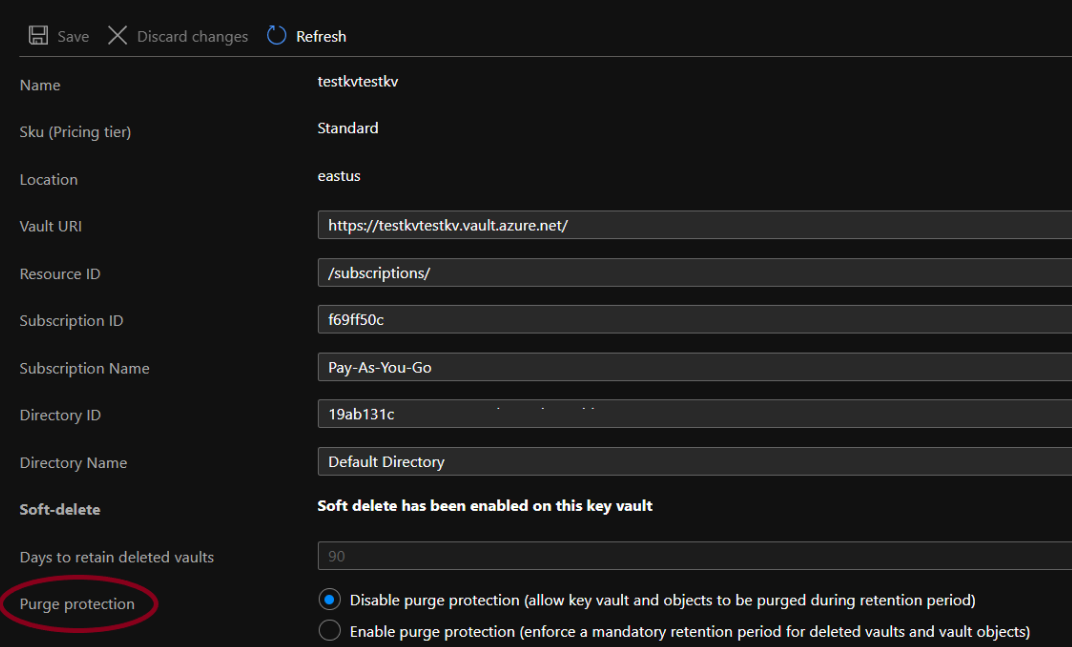
- In front of Purge Protection, if the value is set to “Disable purge protection (allow key vault and objects to be purged during retention period)”, visit the Steps for Remediation section.
- Repeat for other vaults as well.
Steps for Remediation
- Log in to the Azure portal.
- Click on Key vaults under Services or type “Key vaults” in the search box.

- Select a vault to check for the issue.

- From the navigation bar, go to Settings section, click on Properties.

- In front of Purge Protection, set value to “Enable purge protection (enforce a mandatory retention period for deleted vaults and vault objects)”, visit steps to remediation section. Click on Save button given at the top and wait for the changes to get saved.
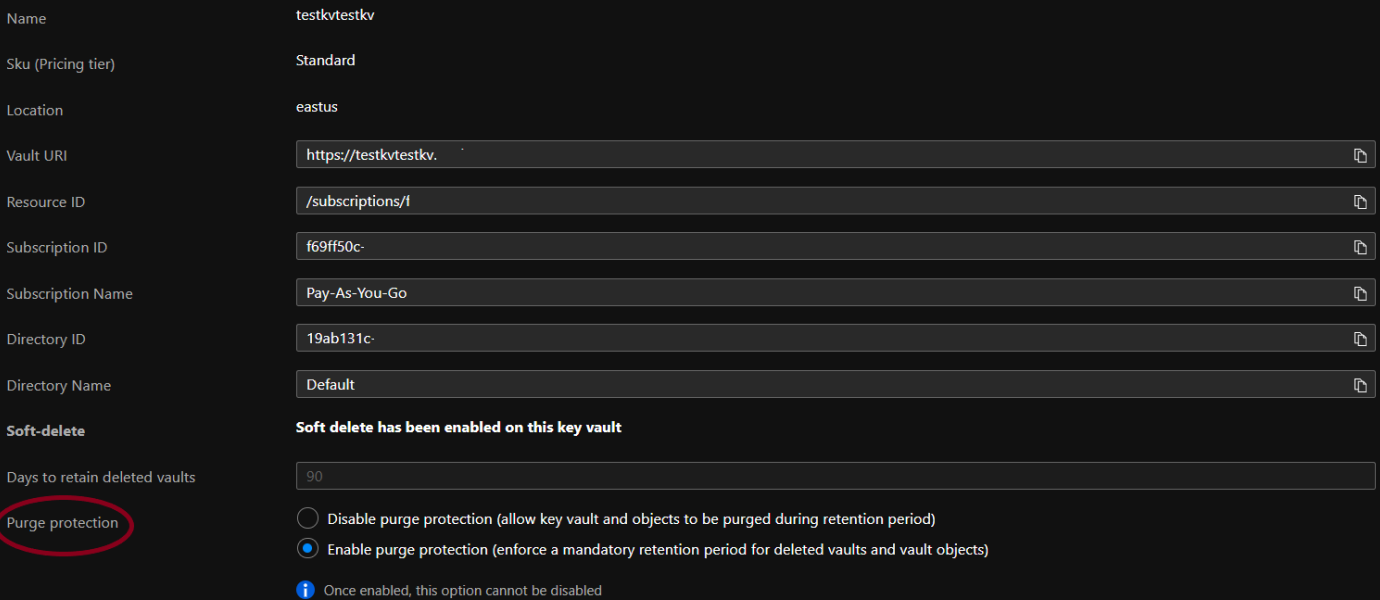
- Repeat for other vaults as well.
Please feel free to reach out to support@pingsafe.com with any questions that you may have.
Thanks
PingSafe Support
