Risk Level: Medium
Description
This module guarantees that your Google Cloud HTTPS/SSL Proxy load balancers are utilizing secure and consistent Secure Socket Layer (SSL) arrangements. Secure Sockets Layer (SSL) strategies figure out which Transport Layer Security (TLS) highlights customers are allowed to utilize when associating with outside Google Cloud load balancers.
About the Service
Google Cloud Load Balancing:
According to Google services, the Google Cloud offers server-side load balancing so you can distribute incoming traffic across multiple virtual machine (VM) instances. Detect and automatically remove unhealthy VM instances using health checks. Instances that become healthy again are automatically re-added. Google's global load balancer knows where the clients are located and directs packets to the closest web service, providing low latency to users while using a single virtual IP (VIP). Using a single VIP means we can increase the time to live (TTL) of our DNS records, which further reduces latency. To know more about GCP Cloud Load Balancing click here.
Impact
To follow customers that are utilizing obsolete conventions, outer burden balancers can be arranged to allow shaky code suites. This choice can permit GCP clients to arrange their load balancers without realizing that they are allowing censured figure suites. Utilizing obsolete and uncertain codes for the SSL arrangements related to your HTTPS/SSL Proxy load balancers could make the SSL association among customers and burden balancers defenceless against taking advantage of. Checking the Secure Socket Layer (SSL) strategies related to your HTTPS and SSL Proxy load balancers for any code suites that exhibit weaknesses or have been viewed as uncertain by late endeavours. Secure Sockets Layer (SSL) approaches to figure out which Transport Layer Security (TLS) highlights customers are allowed to utilize when associating with outer Google Cloud load balancers. To forestall utilization of unreliable or expostulated TLS highlights, SSL approaches should utilize one of the accompanying setups:
- SSL strategy designed with TLS 1.2 and the MODERN Google-oversaw profile.
- SSL strategy designed with the RESTRICTED oversaw profile. This setup expects customers to utilize TLS 1.2 paying little heed to the picked least TLS adaptation.
- SSL strategy designed with the CUSTOM profile and none of the accompanying code suites:
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_3DES_EDE_CBC_SHA
Steps to Reproduce
Using GCP Console-
In order to ensure or determine, if your Google Cloud Platform (GCP) service Load Balancer Secure Socket Layer (SSL) are using insecure ciphers, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find the Networking section.
- Click on the Network Services subsection under Networking.
- Under the Network Services navigation panel, you may find Load Balancing as shown in the figure below.
- Click on the Load Balancing navigation link and a Cloud Load Balancing Page will appear on the screen. Click to open directly from here.
- On the Load Balancing Page, click on the Load Balancers nav link, present at the top of the navigation bar. This is to access the list of all the load balancers present within the Google Cloud Load Balancers in your GCP Project.
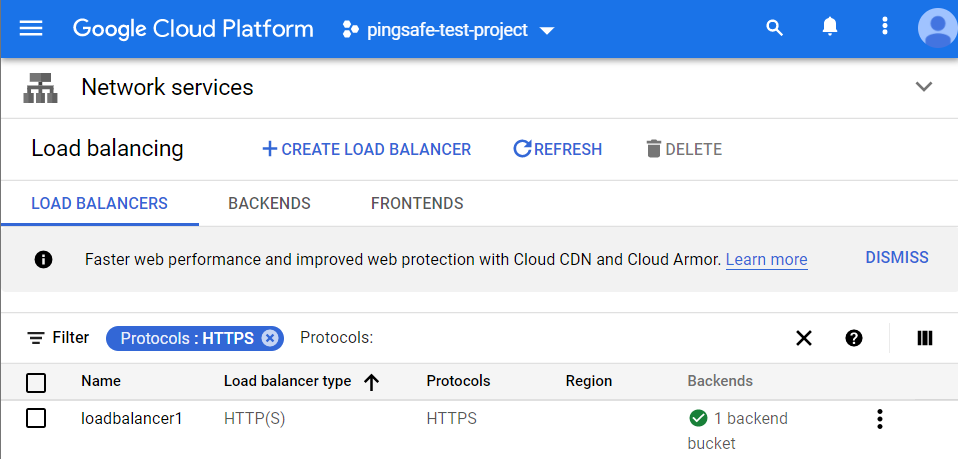
- The list of all the load balancers will be displayed. Under the Filter option in the Load balancer Panel, choose the Protocols option and set it to HTTPS/SSL. This will display only HTTPS and SSL Proxy load balancers in your project.
- Choose the name of Load Balancer you want to examine for. A new page with all the details of that load balancer will be opened up.
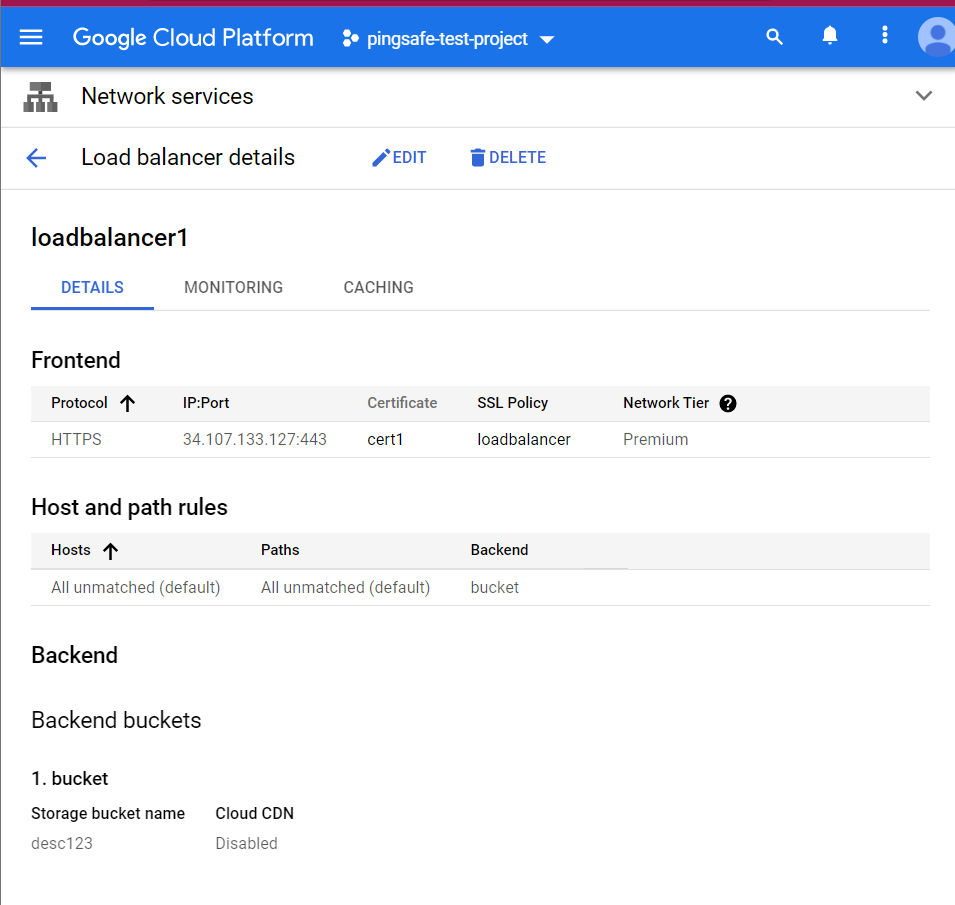
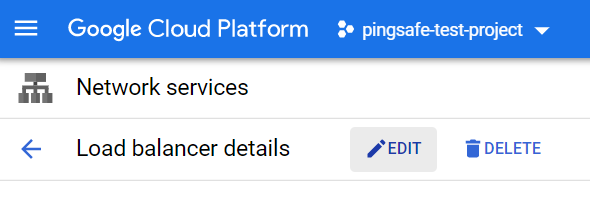
- Click on the Edit button available on the top navigation bar.
- On the Edit HTTPS load balancer page, select the Frontend Configuration Tab present at the left panel.
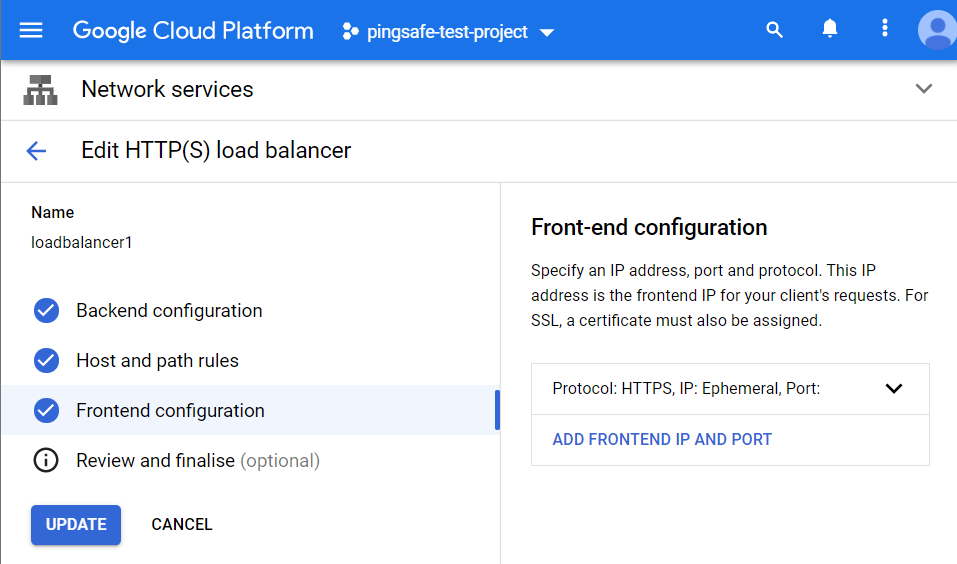
- Under the Frontend Configuration, select the toggle option to open up the details of the frontend IP configuration. Check for the SSL Policy option in it.

- If the SSL Policy value is set to GCP default, that means the selected HTTPS load balancer is configured with the default one and is using weak cipher suites. This is configured with a “Compatible” profile with the “TLS 1.0” TLS version. This is weak as it allows a broad set of clients and supports the same out-of-date SSL features.
- You may repeat steps 9-12 for other load balancers in your GCP Project.
- You may repeat the above-mentioned steps to check for the other GCP projects/folders in your organization.
Steps for Remediation
Using GCP Console-
In order to ensure that your Google Cloud HTTPS/SSL Proxy load balancers are using secure and compliant SSL policies, you need to create new security policies to replace the default ones and reconfigure the insecure policies that have weak or deprecated cipher suites, to apply this follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find the Networking section.
- Click on the Network Services subsection under Networking.

- Under the Network Services navigation panel, you may find Load Balancing as shown in the figure below.

- Click on the Load Balancing navigation link and a Cloud Load Balancing Page will appear on the screen. Click to open directly from here.
- On the Load Balancing Page, click on the Load Balancers nav link, present at the top of the navigation bar. This is to access the list of all the load balancers present within the Google Cloud Load Balancers in your GCP Project.

- The list of all the load balancers will be displayed. Under the Filter option in the Load balancer Panel, choose the Protocols option and set it to HTTPS/SSL. This will display only HTTPS and SSL Proxy load balancers in your project.

- Choose the name of Load Balancer you want to examine for. A new page with all the details of that load balancer will be opened up.

- Click on the Edit button available on the top navigation bar. On the Edit HTTPS load balancer page, select the Frontend Configuration Tab present at the left panel.

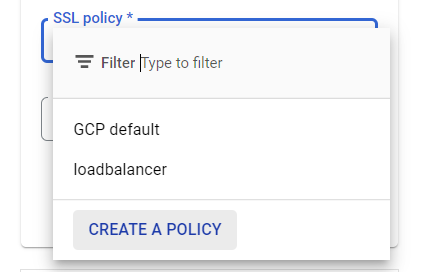
- Under the Frontend Configuration, select the toggle option to open up the details of the frontend IP configuration. Check for the SSL Policy option in it, and open the dropdown to choose Create A Policy button.
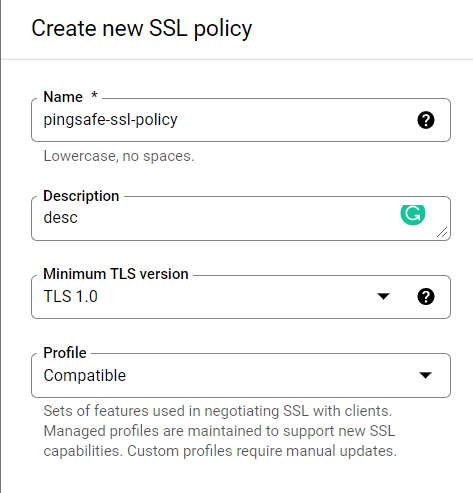
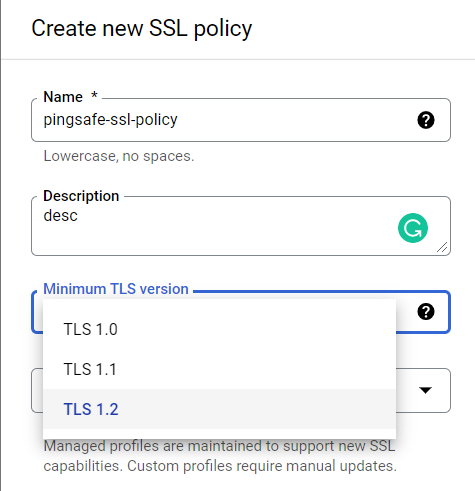
- On the Create New Policy page, enter the asked details. Fill up the name and description of your new SSL policy. Now, open up the dropdown menu of the Minimum TLS version and select TLS 1.2 from it.
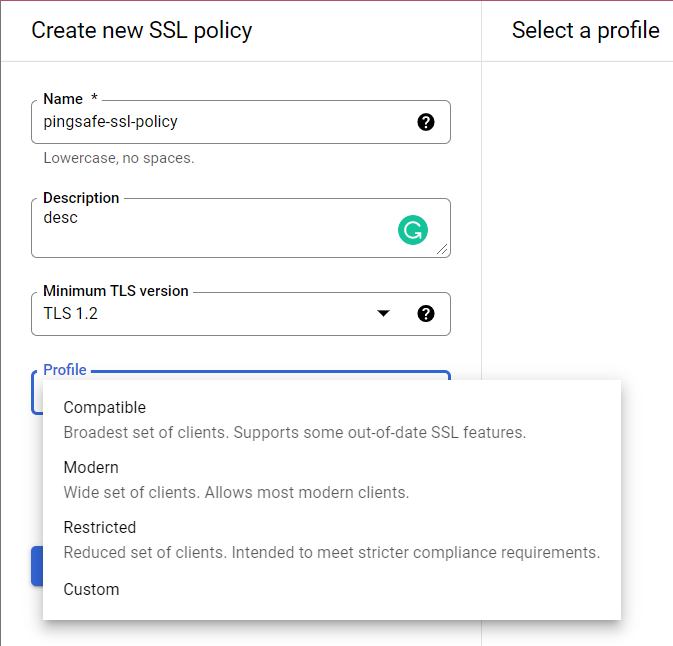
- Now, to fulfill the security and compliance requirements, go under the Profile option. Remember not to go for the Compatible option, instead choose one among the given options:
- Modern: Wide set of clients. Allows most modern clients.
- Restricted: Reduced set of clients. Intended to meet stricter compliance requirements.
- Custom: In case, you need a custom set of cipher suites. Select the ciphers that you want to use for your custom policy from the Features list. Do not include knowledge-base/components/the following cipher suites as these ciphers are considered weak and insecure, which are as follows:
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_GCM_SHA384 TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA TLS_RSA_WITH_3DES_EDE_CBC_SHA
- Click on the Save option to create the new SSL Policy.
- Now, go back to the Edit page and click on the Update button to reconfigure the settings.
- You may repeat steps 9-15 for other load balancers in your GCP Project.
- You may repeat the above-mentioned steps to check for the other GCP projects/folders in your organization.
