Risk Level: Low
Description
This plugin guarantees that Cloud Logs Router information is encrypted with Customer-Managed Keys (CMKs) to have full command over your information encryption and decoding interaction and assist with meeting consistent prerequisites.
About the Service
Google Cloud Logging:
Cloud Logging is a fully managed service that allows you to store, search, analyze, monitor, and alert on logging data and events from Google Cloud and Amazon Web Services. Logging lets you read and write log entries, query your logs, and control how you route and use your logs. Log-based metrics are based on the content of log entries. For example, the metrics can record the number of log entries containing particular messages, or they can extract latency information reported in log entries. You can use log-based metrics in Cloud Monitoring charts and alerting policies. To know more about GCP Cloud Load Balancing click here.
Impact
CMEK for the Log Router is configured at the Google Cloud organization level. It applies to all Cloud projects and folders contained by the Google Cloud organization. This plugin ensures that Cloud Logs Router data is encrypted with Customer-Managed Keys (CMKs) in order to have full control over your data encryption and decryption process and help meet compliance requirements. Thus, the recommended action for this is to enable encryption with Cloud KMS Customer-Managed Keys (CMKs) for your Logs Router data at the GCP organization level
Steps to Reproduce
In order to determine, if GCP Logs Router data is encrypted with Customer Managed Keys (CMKs), follow the steps given below:
Note: This can’t be done using GCP Console.
- Firstly, run the organizations' list command (Windows/macOS/Linux) utilizing custom query channels to list the identifiers (IDs) of the multitude of associations accessible inside your Google Cloud Platform (GCP) account:
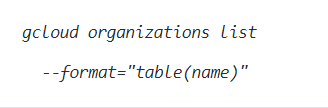
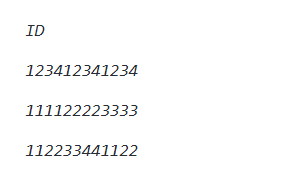
- Now, the command output must return the requested GCP organization identifiers.
- Now, run Logging cmek-settings describe command using the ID of your GCP organization as custom query filters and identifier parameter.
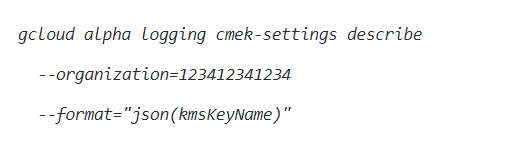
- Now, the command output must return the resource ID of the CMK which is used to encrypt the Logs Router data.

- Now, If the logging cmek-settings portray order yield returns invalid, as displayed in the model over, the information oversaw by Google Cloud Logs Router inside the chose GCP association isn't scrambled with a Customer-Managed Key (CMK).
- You may repeat the above-mentioned steps to check for the other GCP projects/folders in your organization.
Steps for Remediation
In order to enable encryption with Cloud KMS Customer-Managed Keys (CMKs) for your Logs Router data at the GCP organization level, follow the steps mentioned below:
Note: This can’t be done using GCP Console.
- Firstly, you just need to create a Key Ring. A Cloud KMS keyring is a grouping of cryptographic keys made available for organizational purposes in a specific Google Cloud location. Run kms keyrings create command (Windows/macOS/Linux) to create a new Cloud KMS keyring in the specified location.
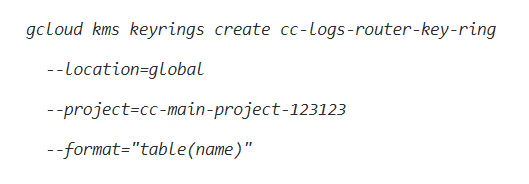
- Now, the command output must return the identifier of the newly created key ring.
- Now, you need to run kms keys create command to create a new Cloud KMS Customer-Managed Key (CMK) within the KMS key ring created at the previous steps.
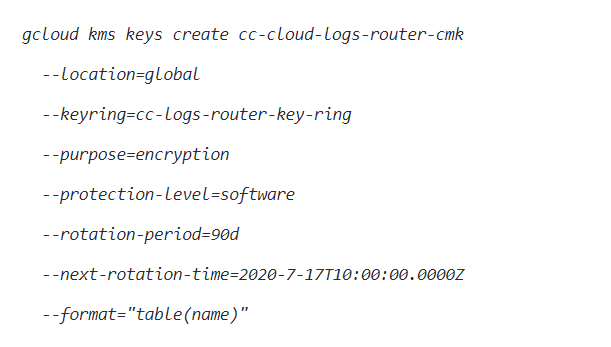
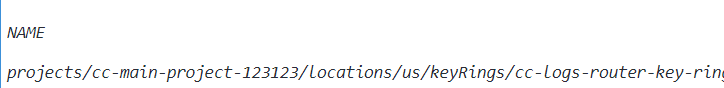
- Now, the command output must return the name of the new Customer-Managed Key (CMK).
NAME
projects/cc-main-project-123123/locations/global/keyRings/cc-logs-router-key-ring/cryptoKeys/cc-cloud-logs-router-cmk - Now, you may run kms keys add-iam-policy-binding command to add a policy binding to the IAM policy of the newly created Customer-Managed Key in order to assign the Cloud KMS "CryptoKey Encrypter/Decrypter" role to the service account.
gcloud kms keys add-iam-policy-binding cc-cloud-logs-router-cmk
--keyring=cc-logs-router-key-ring
--location=global --member=serviceAccount:o123412341234-112233@gcp-sa-logging.iam.gserviceaccount.com
--role roles/cloudkms.cryptoKeyEncrypterDecrypter - Now, the command output must return the updated IAM policy (YAML format).
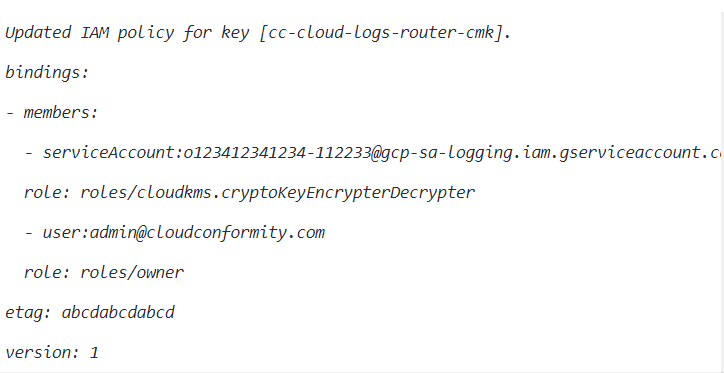
- Customer-Managed Keys (CMKs) for Google Cloud Logs Router can only be configured for GCP organizations. Once configured, it applies to all projects and folders within the specified organization
- Now, you need to run logging cmek-settings update command using the ID of the GCP organization that you want to reconfigure as identifier parameter, to update the Cloud Logging settings for the selected organization in order to encrypt the Logs Router data with the Customer-Managed Key (CMK) created at step no. 3.
gcloud alpha logging cmek-settings update
--organization=123412341234
--kms-key-name=projects/cc-main-project-123123/locations/global/keyRings/cc-logs-router-key-ring/cryptoKeys/cc-cloud-logs-router-cmk - You may repeat the above-mentioned steps to check for the other GCP projects/folders in your organization.
