Risk Level: Low
Description:
This plugin guarantees that the Log Profile in all active locations is set to export 'Write', 'Delete', and 'Action' activities from the control and management planes. In the event of a security incident, exporting log activity for control-plane activity enables audited access to the Azure account with event data.
Recommended Action: Ensure that all activity is logged to the Event Hub or storage account for archiving.
About the Service :
Azure Monitor can help you improve the availability and performance of your apps and services. It provides a complete solution for gathering, evaluating, and responding to telemetry from the cloud and on-premises settings. This data enables you to better understand how your apps are doing and to detect concerns that may harm them or the resources they rely on in the future.
Impact:
If this feature is disabled on your Microsoft Azure Subscription then you won’t be able to audit the accessed event data in case of a security incident.
Steps to Reproduce( Using Azure CLI ) :
- Sign in to Azure CLI.
- Run the command: “ az monitor log-profiles list ”.
- In the output check if categories has all these: "categories": ["Write","Delete","Action" ].
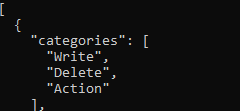
- If any one of these three is missing, the vulnerability exists.
- Repeat steps for other subscriptions in your Microsoft Azure accounts.
Steps for Remediation( Using Azure CLI ) :
- Sign in to Azure Management Console.
- Firstly, delete the misconfigured log profile : az monitor log-profiles delete --name <log profile name>.
- Create a new log profile with the same name using the following code :
-
az monitor log-profiles create --name <name> --categories "Delete" "Write" "Action" --enabled true --days <days> --service-bus-rule-id "/subscriptions/<YOUR SUBSCRIPTION ID>/resourceGroups/<RESOURCE GROUP NAME>/providers/Microsoft.EventHub/namespaces/<Event Hub NAME SPACE>/authorizationrules/RootManageSharedAccessKey".
- Confirm it by running the command: az monitor log-profiles list.

- Repeat steps for other misconfigured log profiles.
