Risk Level
Medium
Description
This plugin ensures that Virtual Private Cloud (VPC) firewall logging is not configured to include logging metadata in order to reduce the size of the log files and optimize cloud storage costs
About the Service:
Google Cloud VPC:
According to Google definitions, VPC which stands for a Virtual Private Network is a virtual version of a physical layer, implemented inside of Google’s Production Network, using Andromeda. The Virtual Private Network offers various features including, connectivity for your Compute Engine Virtual Machine (VM) instances, Google Kubernetes Engine (GKE) clusters, etc. It helps to load balancing and proxy systems for internal system affairs. It even allows assistance in the traffic from Google Cloud external load to backends. User can have the advantage of containing multiple VPC Networks over a single GCP Project. Various default features are already enabled with VPC Networks, for an instance logging metadata is incorporated into your Virtual Private Cloud (VPC) firewall log files. Click here to read more about Google Cloud VPC Networks.
Impact:
Virtual Private Cloud (VPC) firewall logging permits the user of Google Cloud Platform services to confirm, examine, and review the impacts of your firewall rules on your cloud assets including various GCP Projects. Evidently, metadata, which is a set of data that gives information about other present data, is added inside the firewall rule log records of your GCP VPC Project. This in turn cut down the size of log files. Fortunately, you can essentially diminish the log scrapes size and cut down on capacity costs by excluding this extra information. This plugin guarantees that Virtual Private Cloud (VPC) firewall logging isn't arranged to remember logging metadata for requests to diminish the size of the log documents and advance distributed storage costs.
Steps to Reproduce:
Using GCP Console-
In order to ensure if your logging metadata is incorporated into your Virtual Private Cloud (VPC) firewall log files, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find Networking section.
- Click on the VPC Network subsection under Networking.
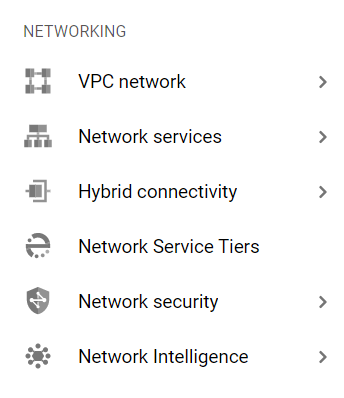
- Under the VPC Network navigation panel, you may find Firewall as shown in the figure below.
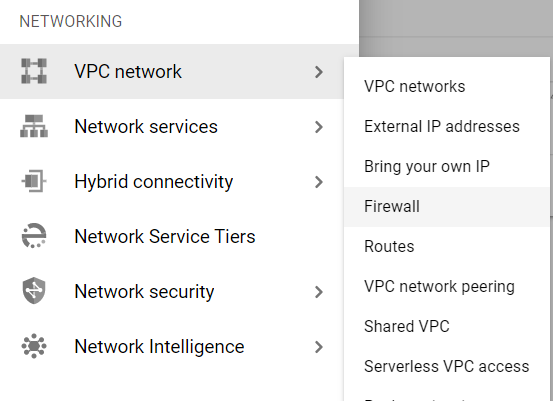
- Click on the Firewall navigation link and a VPC Network Firewall dashboard will appear on the screen. Click to open directly from here.
- On the Firewall dashboard, reach the Filter option in the table and click on it.
- Set the values of properties in the Filter option as:
- Disabled: False
- Logs: On
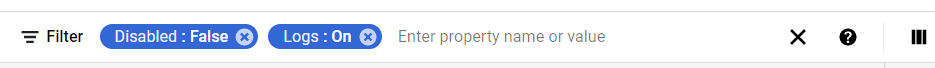
- Under Step 8.a, by setting Disabled property to False, it will list down all the egress and ingress rules enabled in your selected GCP Project for all the resources.
- Under Step 8.b, by setting the Logs property to On, it will list down all the egress and ingress firewall rules with the functionality of logging enabled in them.
- Among the filtered list of firewall rules, click and open the firewall rule, you want to examine.
- Once you click a page will open for your selected firewall rule. Click on the Logs section available on the top. Click on Show Log Details and check out the configuration settings for Include Metadata.
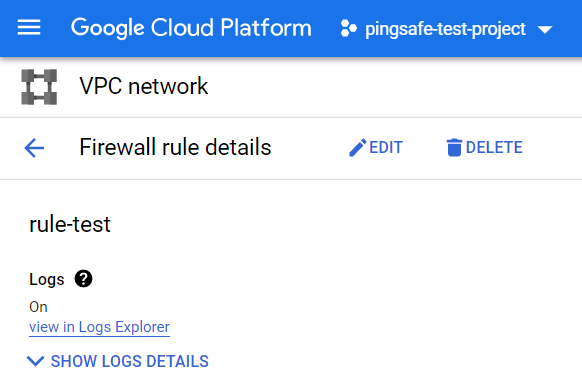
- In case, the Include Metadata configuration settings are enabled, then the logging metadata is incorporated in log files of your selected GCP Project.
- This way you can check out if your logging metadata is incorporated into your Virtual Private Cloud (VPC) firewall log files.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.
Steps for Remediation:
Using GCP Console
In order to impair or disable the addition of logging metadata to firewall rule logs in your GCP Virtual Private Cloud (VPC) network, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find the Networking section.
- Click on the VPC Network subsection under Networking.

- Under the VPC Network navigation panel, you may find Firewall as shown in the figure below.

- Click on Firewall navigation link and a VPC Network Firewall dashboard will appear on the screen. Click to open directly from here.
- On the Firewall dashboard, reach to the Filter option in the table and click on it.
- Set the values of properties in the Filter option as:
- Disabled: False
- Logs: On

- Under Step 8.a, by setting Disabled property to False, it will list down all the egress and ingress rules enabled in your selected GCP Project for all the resources.
- Under Step 8..b, by setting the Logs property to On, it will list down all the egress and ingress firewall rules with the functionality of logging enabled in them.
- Among the filtered list of firewall rules, click and open the firewall rule, you want to examine.
- Once you click a page will open for your selected firewall rule. Click on the Logs section available on the top. There you will have the options to Edit, Delete, Show Logs Details, etc.

- Click on the Edit button with a pencil icon. Click on Show Logs Details and uncheck the checkbox of Include Metadata available under the Additional Fields option.
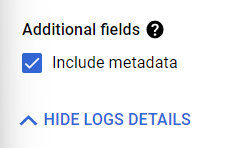
- This will eventually diminish or reduce the size of log files generated for the selected firewall rule under your selected GCP VPC Network project.
- After ensuring your edited options, click on SAVE Button to apply changes and go back to the previous page.
- You may repeat the above steps for other GCP Projects under your organization.
