Risk Level: Medium
Description:
This plugin guarantees that the root account is protected by a hardware multi-factor authentication device. For enhanced protection, the root account should utilize a hardware MFA device rather than a virtual device, which might be more easily hacked.
PingSafe strongly recommends enabling a hardware MFA device for the root account and disabling any virtual devices.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
Not having an MFA-protected root account makes AWS resources and services vulnerable to attacks. An MFA device signature adds an extra layer of protection on top of existing root credentials making AWS root account virtually impossible to penetrate without the MFA-generated passcode.
Steps to reproduce :
- Sign-in to AWS management console.
https://ap-south-1.console.aws.amazon.com/console/ - Click on the “Account Name” and select “My Security Credentials”.
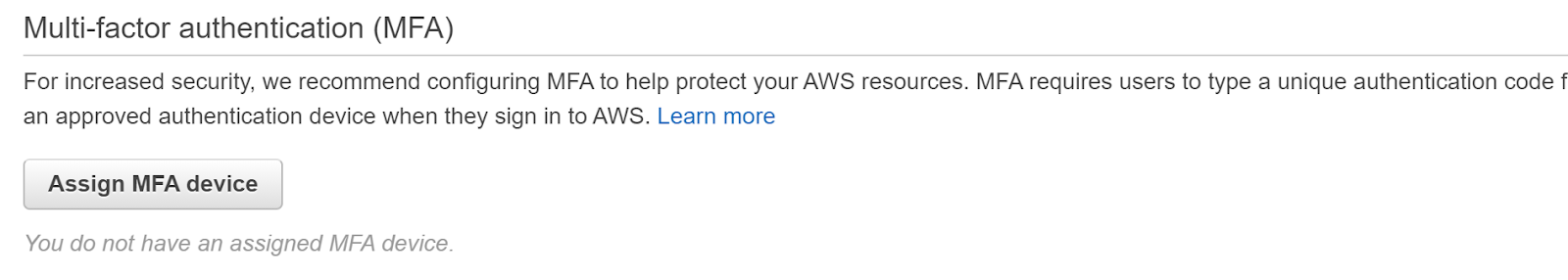
- Check the “MFA management” section. If there is no MFA device listed that means that the root account is not MFA protected. Since we are looking if hardware MFA is enabled we will check the Device type attribute of the enabled MFA. If the MFA device listed here does not have the Device Type set to "Hardware MFA", your AWS root account is not protected using a hardware-based MFA device.
- Repeat the steps for other root accounts too.
Steps for remediation :
- Sign-in to AWS management console.
https://ap-south-1.console.aws.amazon.com/console/ - Click on the “Account Name” and select “My Security Credentials”.

- Check the “MFA management” section. If there is no MFA device listed that means that the root account is not MFA protected. Since we are looking if hardware MFA is enabled we will check the Device type attribute of the enabled MFA. If the MFA device listed here does not have the Device Type set to "Hardware MFA", your AWS root account is not protected using a hardware-based MFA device.

- Click on “Assign MFA device” to set up a hardware MFA device for the root account.
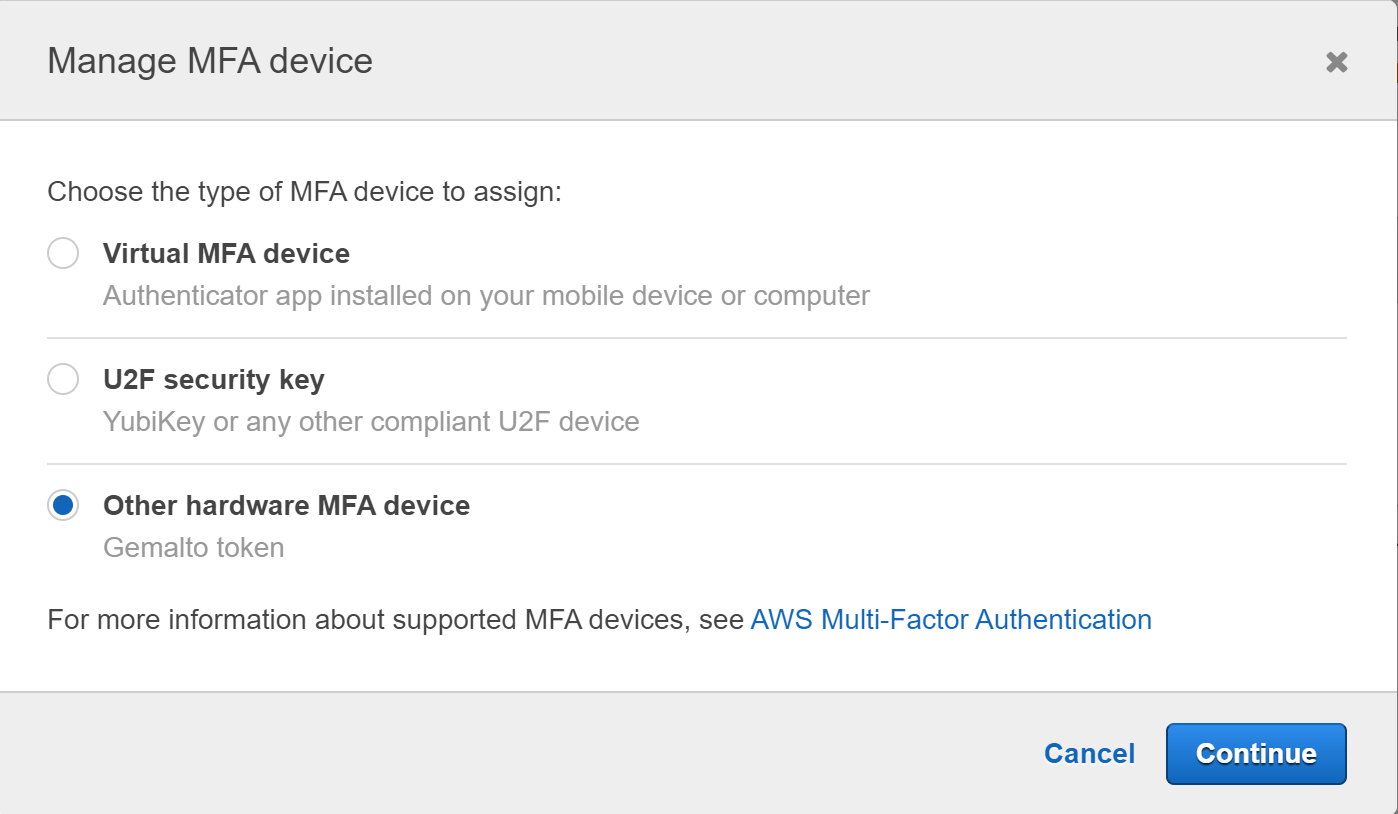
- Select “Other hardware MFA device” and click “Continue” in the Manage MFA Device dialog box.
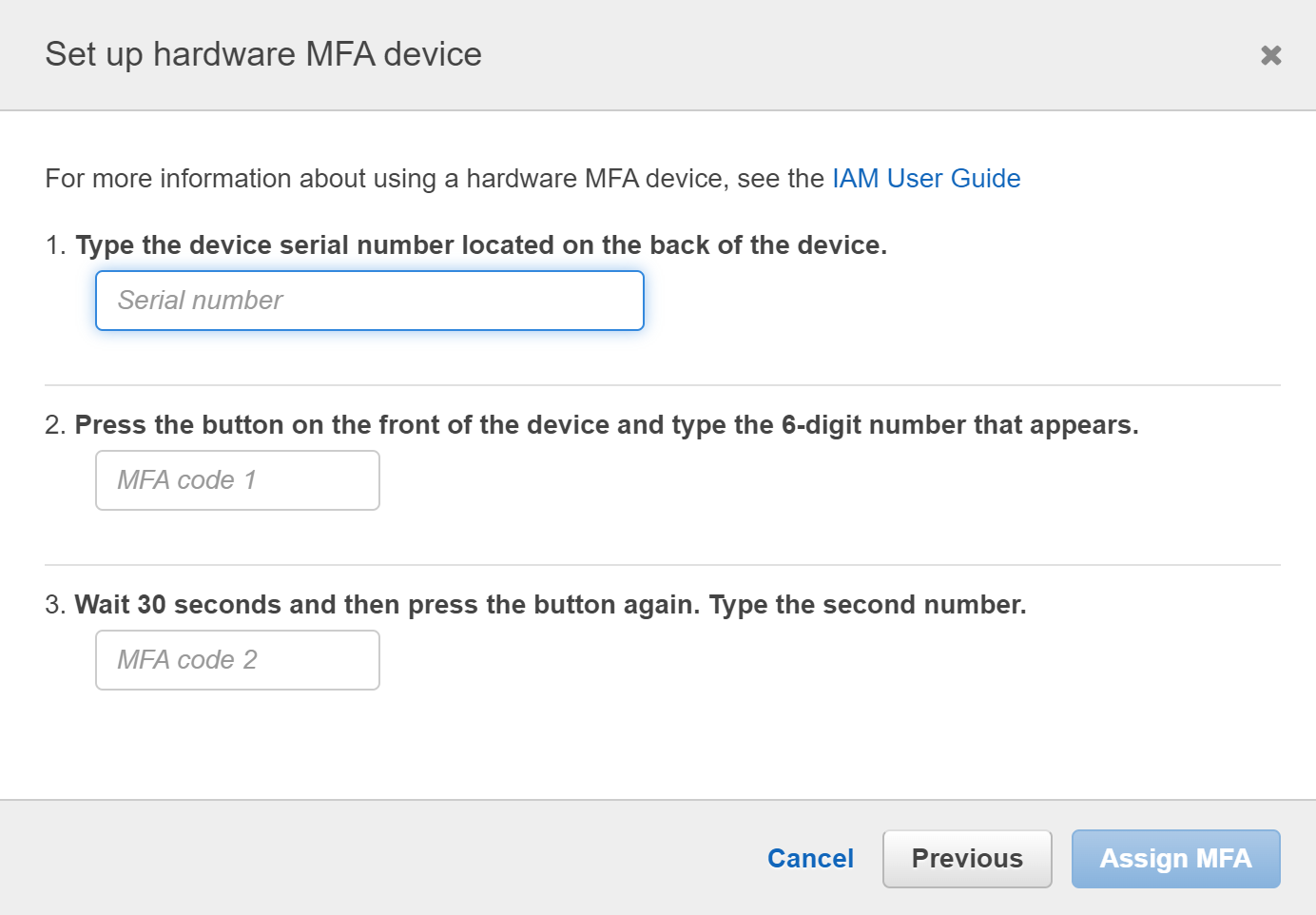
- Type the required fields to set up the hardware MFA in the Setup hardware MFA device tab and then click on Assign MFA to complete the procedure.
- Repeat the steps for other root accounts too.
References:
