RISK LEVEL
High
DESCRIPTION
This plugin determines if TCP port 7001 for Cassandra is open to the public. Also, it consists of valid steps or measures to be taken to avoid unhealthy vulnerability to all IP addresses ranges i.e. 0.0.0.0/0. While some ports such as HTTP and HTTPS are required to be open to the public to function properly, more sensitive services such as Cassandra should be restricted to known IP addresses.
ABOUT THE SERVICE
Google Cloud VPC:
According to Google definitions, VPC which stands for a Virtual Private Network is a virtual version of a physical layer, implemented inside of Google’s Production Network, using Andromeda. The Virtual Private Network offers various features including, connectivity for your Compute Engine Virtual Machine (VM) instances, Google Kubernetes Engine (GKE) clusters, etc. It helps to load balancing and proxy systems for internal system affairs. It even allows assistance in the traffic from Google Cloud external load to backends. Users can have the advantage of containing multiple VPC Networks over a single GCP Project. Various default features are already enabled with VPC Networks, for instance, logging metadata is incorporated into your Virtual Private Cloud (VPC) firewall log files. Click here to read more about Google Cloud VPC Networks.
IMPACT
Cassandra for GCP gives clients and ventures a straightforward organization interaction to rapidly introduce a Cassandra bunch on GCP in a solitary locale across various zones. Each group additionally incorporates a VM that gives a total arrangement of improvement assets including code models, docs, and information joining instruments. Alternatively, DataStax Luna additionally gives membership-based help to open-source Cassandra on GCP. DataStax Luna endorsers get the advantages of open-source programming, with direct admittance to driving Cassandra contributors. This module decides or in similar terms to be said that, this plugin guarantees whether TCP port 7001 for Cassandra is available to people in general. Additionally, it comprises of substantial advances or measures to be taken to stay away from undesirable weakness to all IP tends to ranges for example 0.0.0.0/0. While a few ports, for example, HTTP and HTTPS are needed to be available to general society to work appropriately, more delicate administrations, for example, Cassandra ought to be confined to realized IP addresses.
STEPS TO REPRODUCE
Using GCP Console-
In order to determine if your Google Cloud Virtual Private Cloud Firewall Rules permits access without restrictions on TCP port 7001, follow the steps mentioned below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate.
- From the Navigation Menu on the left, you may find the Networking section.
- Click on the VPC Network subsection under Networking.
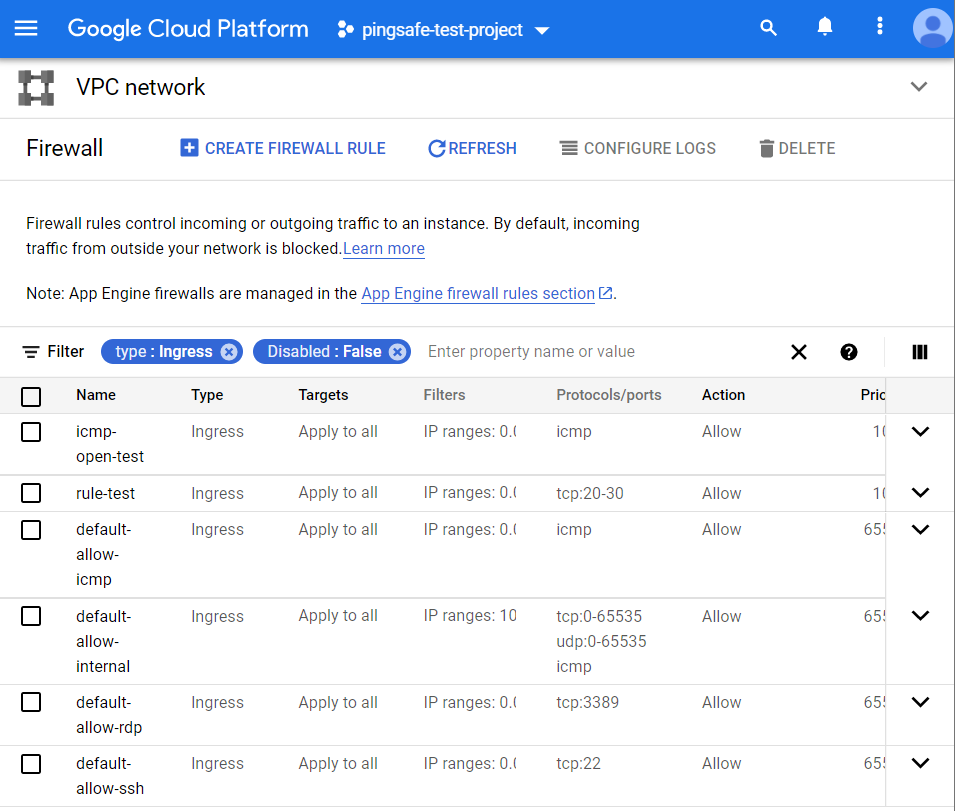
- Under the VPC Network navigation panel, you may find Firewall as shown in the figure below.
- Click on the Firewall navigation link and a VPC Network Firewall dashboard will appear on the screen. Click to open directly from here.
- On the Firewall dashboard, reach the Filter option in the table and click on it.
- Set the values of properties in the Filter option as:
- Disabled: False
- Type: Ingress
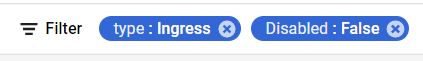
- Under Step 8.a, by setting Disabled property to False, it will list down all the egress and ingress rules enabled in your selected GCP Project for all the resources.
- Under Step 8.b, by setting Type property to Ingress, it will list down all the ingress rules enabled in your selected GCP Project for all the resources.
- Among the filtered list of firewall rules, check for the inbound rules with Protocols or Ports attribute equal to tcp:7001 or tcp:0-65535.
- Now check for other attributes, if Action is set to Allow and Filters is set to IP ranges: 0.0.0.0/0.
- If there exist rules which are fit this criterion, that means there are VPC Network firewall rules that allow unrestricted access on TCP port: 7001. Hence, the Cassandra access to that associated GCP VM instance is unsecured.
- This way you can check out if the Cassandra access is unsecured or secured for the Virtual Private Cloud Network firewall rules.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.
STEPS FOR REMEDIATION
Using GCP Console-
In order to update or reestablish your VPC network firewall rules configuration to restrict Cassandra access for trusted authorized IP addresses or IP ranges only, follow the steps given below:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find the Networking section.
- Click on the VPC Network subsection under Networking.

- Under the VPC Network navigation panel, you may find Firewall as shown in the figure below.

- Click on the Firewall navigation link and a VPC Network Firewall dashboard will appear on the screen. Click to open directly from here.
- On the Firewall dashboard, reach the Filter option in the table and click on it.
- Set the values of properties in the Filter option as:
- Disabled: False
- Type: Ingress

- Under Step 8.a, by setting Disabled property to False, it will list down all the egress and ingress rules enabled in your selected GCP Project for all the resources.
- Under Step 8.b, by setting Type property to Ingress, it will list down all the ingress rules enabled in your selected GCP Project for all the resources.
- Among the filtered list of firewall rules, check for the inbound rules with Protocols or Ports attribute equal to tcp:7001.
- Now check for other attributes, if Action is set to Allow and Filters is set to IP ranges: 0.0.0.0/0.
- Click on the name of the rule that fits the steps 11, 12 criteria to reconfigure the settings. A new page of that firewall network rule will be opened.
- Now, click on the Edit button present at the top of the dashboard page.
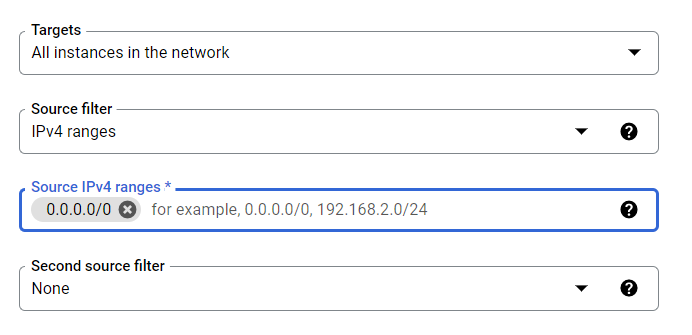
- Remove the non-compliant or non-biddable 0.0.0.0/0 IP address range under the Source IP ranges configuration section. This is done to deny public inbound access on port:7001 of TCP in Cassandra.
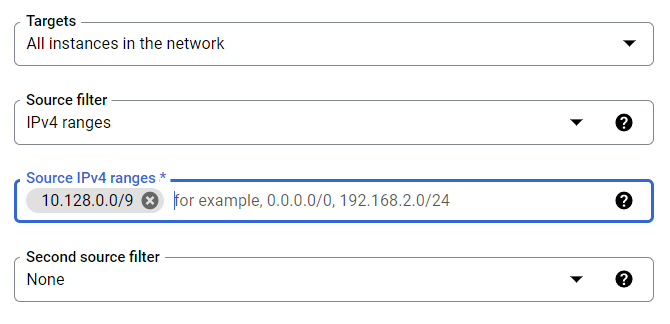
- Now, type the IP address ranges into the Source IP ranges configuration section. The entered IP address range must be in desired CIDR format like 10.128.0.0/9. The IP range can have address included in your VPC network and even outside of your network.
- After ensuring your edited options, click on SAVE Button to apply changes and go back to the previous page.
- You may repeat steps 11-16 for other firewall rules with TCP port: 7001 in your GCP Project.
- You may repeat the above steps for other GCP Projects under your organization.
