Ensures that the TCP port 3389 for RDP is not publicly accessible.
Risk Level: High
Description
This plugin ensures that the TCP port 3389 for RDP in firewalls is not open to the public. While some ports such as HTTP and HTTPS are required to be open to the public to function properly, more sensitive services such as RDP should be restricted only to known IP addresses. Thus, the sources for inbound rules should not include “All IPv4” and “All IPv6” to ensure optimal security.
About the Service
DigitalOcean Firewall:
DigitalOcean Cloud Firewalls are an organization-based, stateful firewall administration for Droplets given at no extra expense. Cloud firewalls block all traffic that isn't explicitly allowed by a standard. Firewalls place an obstruction between your servers and different machines in the organization to safeguard them from outer assaults. Firewalls can behave based, which are designed on a for every waiter premise utilizing administrations like IPTables or UFW. Others, such as DigitalOcean Cloud Firewalls, are network-based and stop traffic at the organization layer before it arrives at the server.
Impact
RDP (Remote Desktop Protocol) is a Microsoft-developed protocol that allows a user to connect to another computer via a network connection using a graphical interface. By default, it accepts requests through port 3389. If this port is accessible to the public, it may increase the danger of attack on the droplets associated with these rules since anyone on the internet can try to get in through the network firewall. As a result, the security and privacy of the data present in the application are at risk.
Steps to Reproduce
- Sign In to your DigitalOcean Console.
- Select the project you want to investigate under the PROJECTS section.
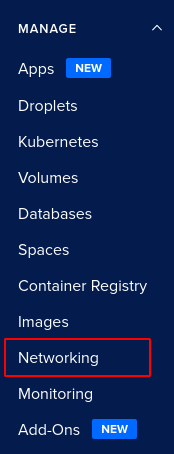
- From the navigation panel on the left side of the console, go to Networking under the MANAGE section and select Firewalls. You can use this link (https://cloud.digitalocean.com/networking/firewalls) to navigate directly if you’re already logged in.
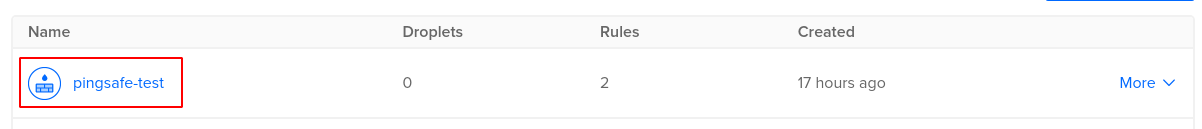
- In the list of firewalls available, select the firewall you wish to investigate.
- In the Inbound Rules list, check if any of the rules have the configuration shown below:
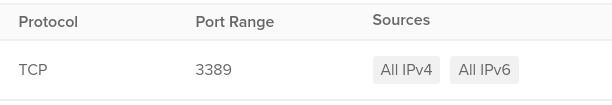
If it exists, then there are firewall rules that allow unrestricted access on TCP port: 3389. Hence, the RDP access to that associated DigitalOcean Droplet is not secure. - Repeat step 5 for all the firewalls you want to investigate in the selected project.
- If you have multiple projects that you want to investigate, repeat steps 2-6 for each project in your DigitalOcean console.
Steps for Remediation
Determine whether or not you truly require RDP access to be open publicly. If not, make the necessary changes using the steps below.
- Sign In to your DigitalOcean Console.
- Select the project you want to investigate under the PROJECTS section.

- From the navigation panel on the left side of the console, go to Networking under the MANAGE section and select Firewalls. You can use this link (https://cloud.digitalocean.com/networking/firewalls) to navigate directly if you’re already logged in.


- In the list of firewalls available, select the firewall you wish to reconfigure.

- In the Inbound Rules list, click on More and then click on the Edit rule for the rule you wish to reconfigure. (In case you aren’t sure which firewall rule needs to be configured, follow the steps to reproduce listed above to determine which to choose.)
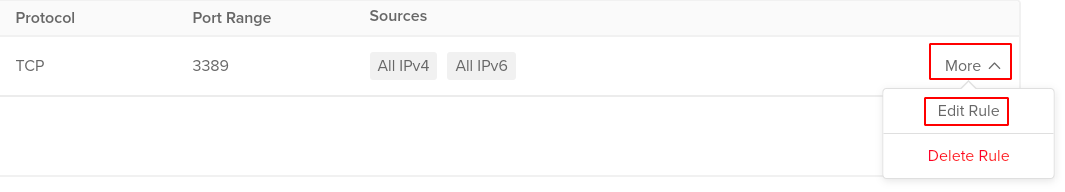
- Click on the X icon next to All IPv4 and All IPv6 options under Sources to restrict public access and add then add your desired authorized source IP address.
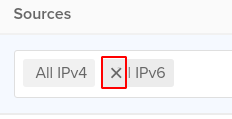
- Click Save to apply all the changes.
- Repeat steps 4 to 7 for all the firewalls you wish to reconfigure in the selected project.
- If you have multiple projects that you want to configure, repeat steps 2 to 8 for each project in your DigitalOcean console.
