Risk Level: Low
Description
This plugin detects EC2 instances with multiple security groups that share the same rules. Overlapping inbound rules make managing EC2 instance access much more difficult. If a rule is removed or modified from one security group, the previous version might still remain in another, resulting in inadvertent access to the instance.
About the Service
Amazon EC2: Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the Amazon Web Services (AWS) Cloud. With the EC2 instance, you can launch as many virtual servers as you need, configure security and networking, and manage storage without worrying about the hardware needs of the process. Security Groups act as a firewall for an EC2 instance to control the incoming and outgoing traffic. You can read more about security groups here.
Impact
Security Groups act as a firewall for an EC2 instance to control the incoming and outgoing traffic with certain rules. A single EC2 instance can have multiple security groups to control traffic. In such a case, the instance will use a combination of all the rules mentions in the security groups.
If there are duplicate rules, modifying a rule in one group might remain in the previous state in another group. Since the EC2 instance will merge all the rules, it will result in unwanted traffic for the instance. As a good security measure, it is advised to use a single rule of a port and protocol combination for an instance.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the EC2 Management Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- From the left navigation pane, migrate to the Instances section and select Instances.
- This will display a list of EC2 instances currently running. Select the one you want to investigate by clicking on its Instance ID.
- Click on the Security tab from the menu below.
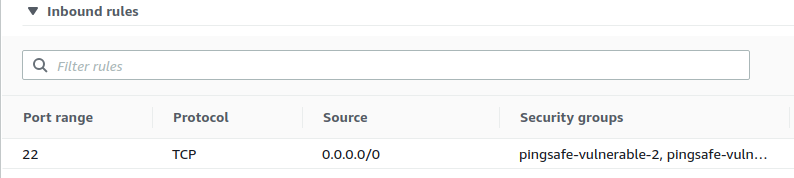
- Examine the Inbound rules. If for a single rule, there is more than one security group associated, it can make managing access much difficult. It is advised to have only one security group associated with a single rule.
- Repeat steps 4 to 6 for all the EC2 instances you want to investigate.
Steps for Remediation
Structure security groups to provide a single category of access and do not duplicate rules across groups used by the same instances.
- Log In to your AWS Console.
- Open the EC2 Management Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- From the left navigation pane, migrate to the Instances section and select Instances.

- This will display a list of EC2 instances currently running. Select the vulnerable security group by clicking on its Instance ID.
- Click on the Security tab from the menu below.

- Examine the Inbound rules and note down the names of security groups with duplicate rules.

- From the left navigation pane, migrate to the Network and Security section and select Security Groups.

- Select the security group whose duplicate rule you want to delete by clicking on its Security Group ID.
- Click on Edit Inbound Rules.
- Click on the Delete button beside the duplicate rule you wish to delete.
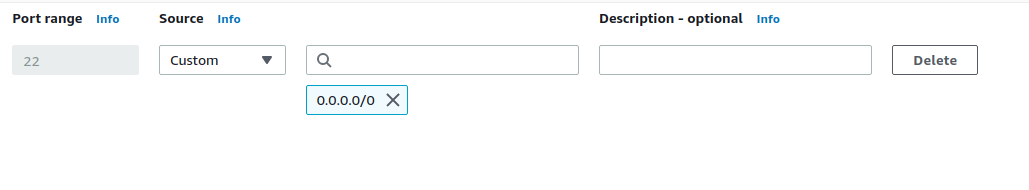
- You can now save the changes by clicking on the Save button.
- Repeat steps 4 to 11 for all the vulnerable EC2 instances.
Note: Make sure to retain one of the duplicate rules or else all the control will be deleted.
