RISK LEVEL
High
DESCRIPTION
This plugin of GCP Identity and Access Management (IAM) ensures that no users are using their personal accounts for accessing GCP. Personal accounts are personally created and are not controlled by organizations. Fully managed accounts are recommended for increased visibility, auditing, and control over access to resources. This is needed to be ensured due to the fact that, your account will be vulnerable for personal use and can’t be handled by associations.
ABOUT THE SERVICE
Google Cloud IAM:
IAM, which is an acronym for Identity and Access Management, is the Google Cloud policy. This policy is responsible for specifying access controls for Google Cloud resources. Basically, IAM allows heads to approve who can make a move on explicit assets, giving you full control and permeability to oversee Google Cloud assets halfway. For undertakings with complex hierarchical designs, many workgroups, and many activities, IAM gives a bound together view into security strategy across your whole association, with worked in evaluating to ease consistency processes. For more information, click here.
IMPACT
When an IAM Account is created with a personal Email Id, your account will be vulnerable for personal use and can’t be handled by associations. This way the best security practices for cloud security are restricted to under-functioning. This module guarantees that no clients are utilizing their own records for getting to GCP. Using corporate credentials for accessing GCP helps in two-way binding, which includes an extra security layer along with expansion in reach. The same organization credentials can be utilized under guided authority.
STEPS TO REPRODUCE
Using GCP Console-
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.
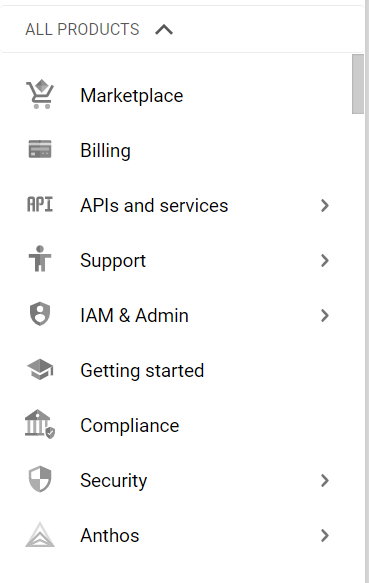
- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.
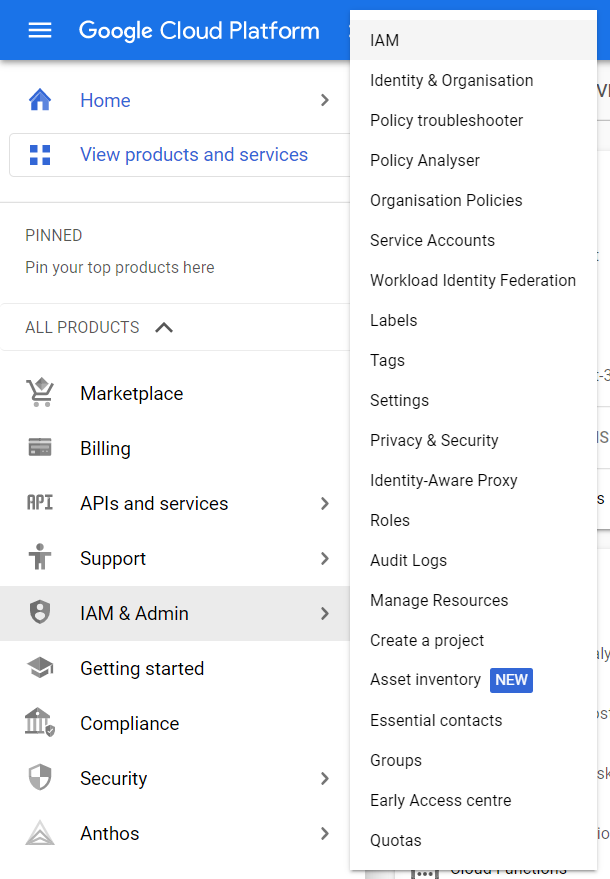
- Under IAM & Admin section, click on the IAM button. Thence, a new IAM Page will appear.
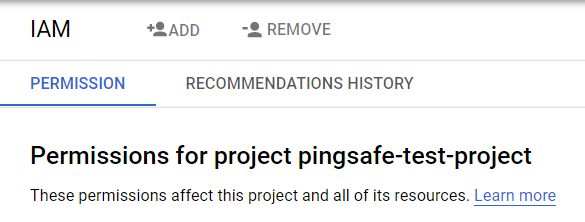
- After selecting the IAM button, click on the Permissions Tab available on the IAM Page.
- On the MEMBERS board, check for any record individuals that utilization email addresses outside the association's space, for example, Gmail addresses.
- In the event that at least one part of the accounts are Gmail accounts, the admittance to the chose Google Cloud Platform (GCP) association can be made with both individual record certifications and corporate login accreditations, subsequently the entrance setup isn't agreeable.
- This way you can check out the members using personal or organization gmail accounts.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organization deployed within your record.
STEPS FOR REMEDIATION
Using GCP Console
Firstly, ensure that other email accounts which do not lie in your organization, should not be encouraged to have Identity & Access Management (IAM) permissions to GCP console projects. This can be done by following the steps below:
- Use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.

- Under IAM & Admin section, click on the Organization Policies button. Thence, a new Organization Policy Page will appear.
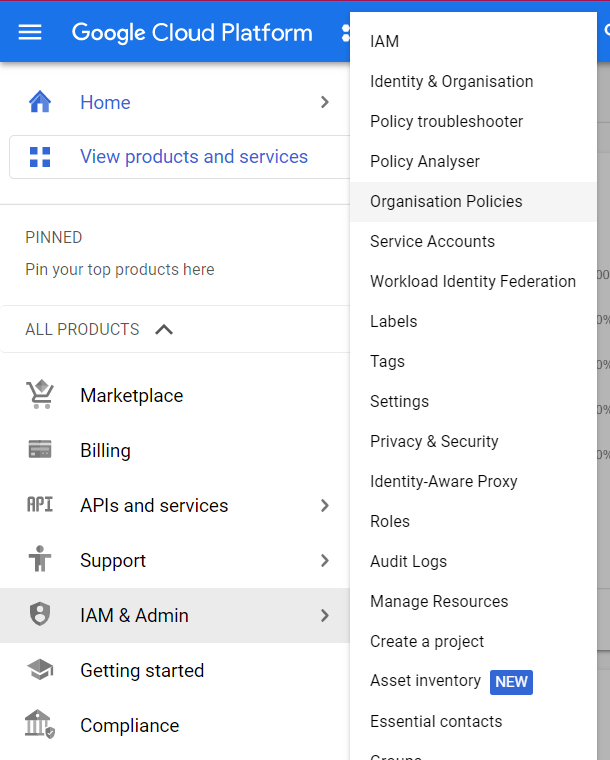
- Under the Organization Policies Page, there is search box having a placeholder with value, ‘Filter by policy name or ID’.
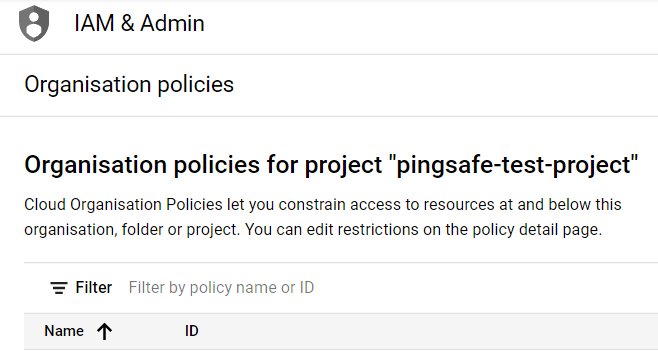
- Use that search box to find Domain Restricted Sharing by typing in it. Then click on it.
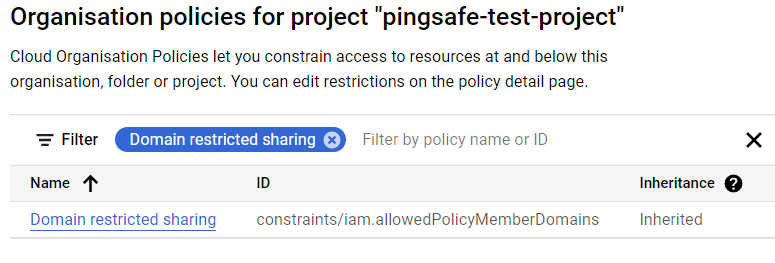
- On the Domain Restricted Sharing policy page, under APPLIES TO section, select Customize option. Ensure that Merge With Parent option is enabled under Policy Enforcement section.
- Under the Policy Values dropdown menu, pick Custom and select Allow from Policy Type list.
- The NEW POLICY VALUE type box is present under Custom values, enter the G-Suite Customer ID asked under NEW POLICY VALUE type box.
- After ensuring the correct entered details click on the SAVE button.
- You may repeat the above steps for other GCP Projects under your organization.
- After the successful completion of the above-mentioned steps, create fresh new Google Organization/Corporate Login Accounts rather than personal accounts. Follow the steps mentioned below:
- Sign in to Google Admin Console with your GCP authorized organizational credentials. Visit https://admin.google.com/ for more information.
- Select USERS under the ADMIN CONSOLE page.
- Select ADD A NEW USER for creating a new user under your organization.
- Specify the asked information, and change the settings to ask for PASSWORD CHANGE OPTION in the next sign-in.
- Click ADD NEW USER and select DONE. Now, you may now access your GCP resources/folders/projects with new user credentials specified by you.
