This plugin detects Route53 records linking to S3 buckets from public hosted zones where the relevant bucket does not exist.
Risk Level: High
Description:
This plugin detects Route53 records linking to S3 buckets from public hosted zones where the relevant bucket does not exist.
About the Service :
Amazon Route 53 is a cloud Domain Name System (DNS) web service that is highly accessible and scalable. It is intended to provide developers and businesses with a highly dependable and cost-effective method of routing end users to Internet applications.
Amazon Route 53 connects user requests to AWS infrastructure such as Amazon EC2 instances, Elastic Load Balancing load balancers, and Amazon S3 buckets, as well as equipment outside of AWS.
Impact:
A domain takeover can occur if a malicious user creates an instance with the same DNS name in another AWS account and uploads content.
The attacker can then disguise the hijacked domain as an internal employee site and force employees to submit sensitive information.
Steps to reproduce :
- Login to AWS Management Console.
- Navigate to Route 53 dashboard. (https://console.aws.amazon.com/route53/ )
- Next, move to the “Hosted Zone” in the left navigation panel under Route 53.
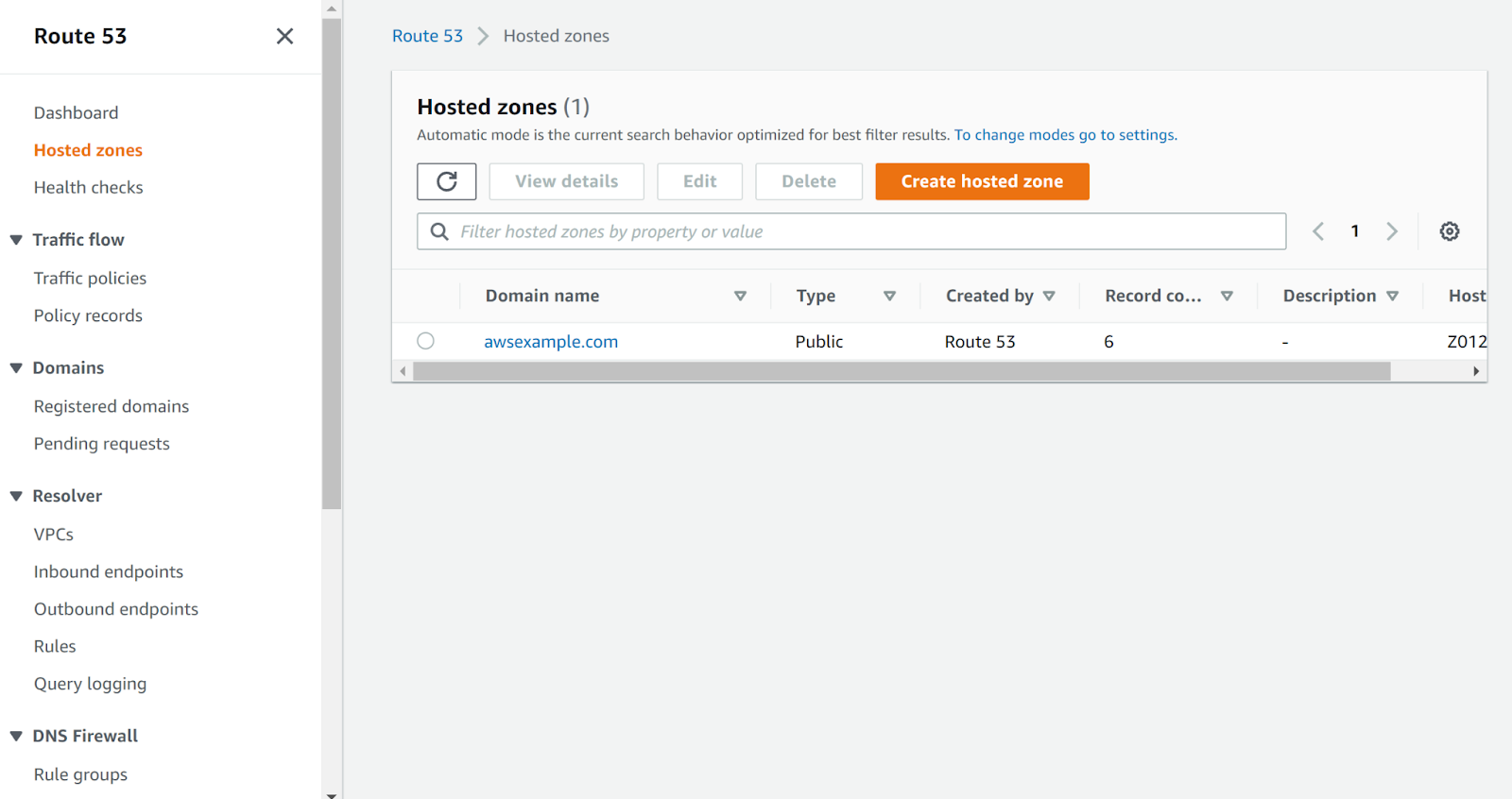
- Select the hosted zone to examine.
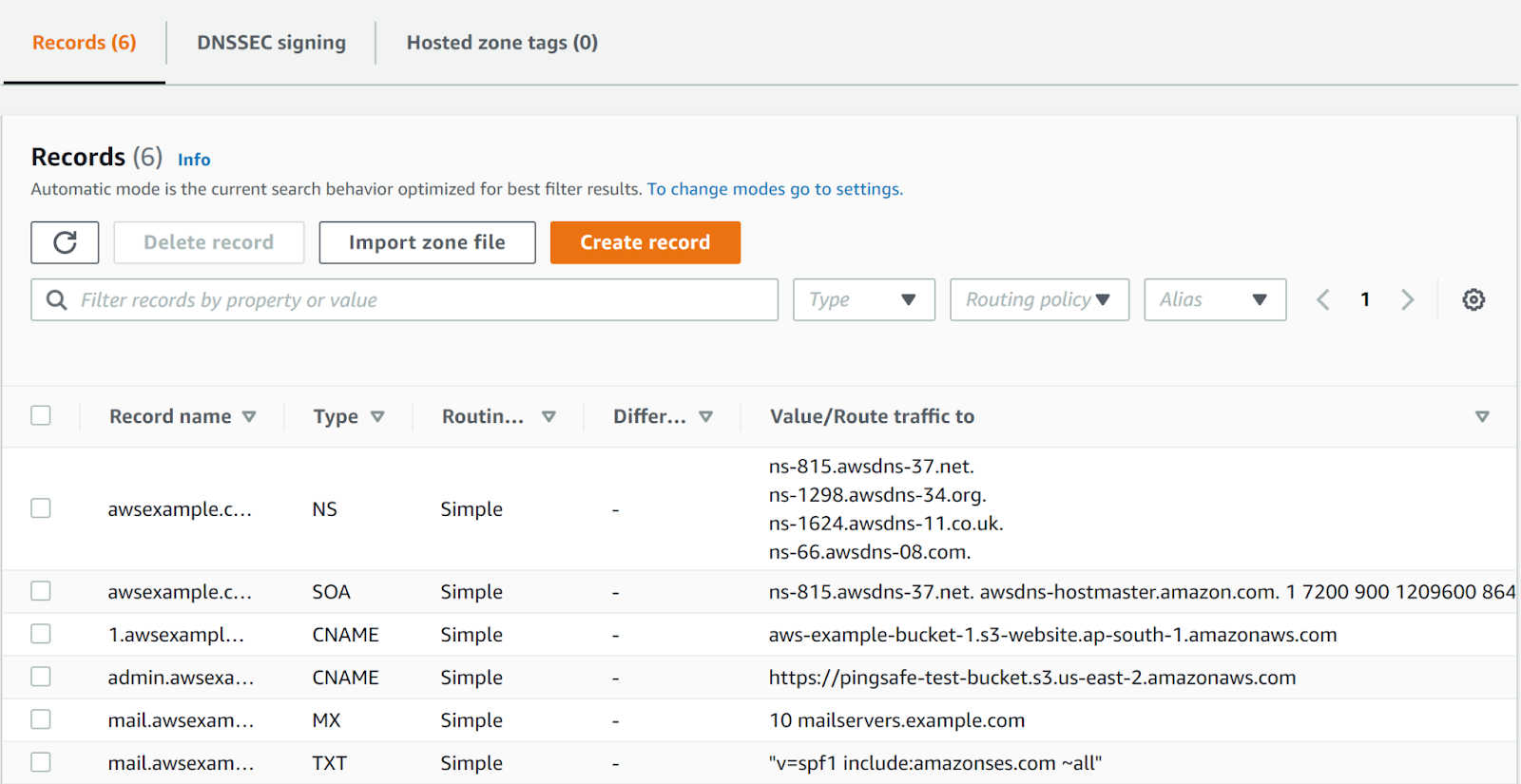
- Next, check the admin.awsexample.com if the Type is CNAME or AAAA. This suggests that it is routing it’s value to the S3 bucket.
- Copy the link of the S3 bucket and navigate to the S3 Management Console.
- Search for the S3 bucket in the S3 Console.
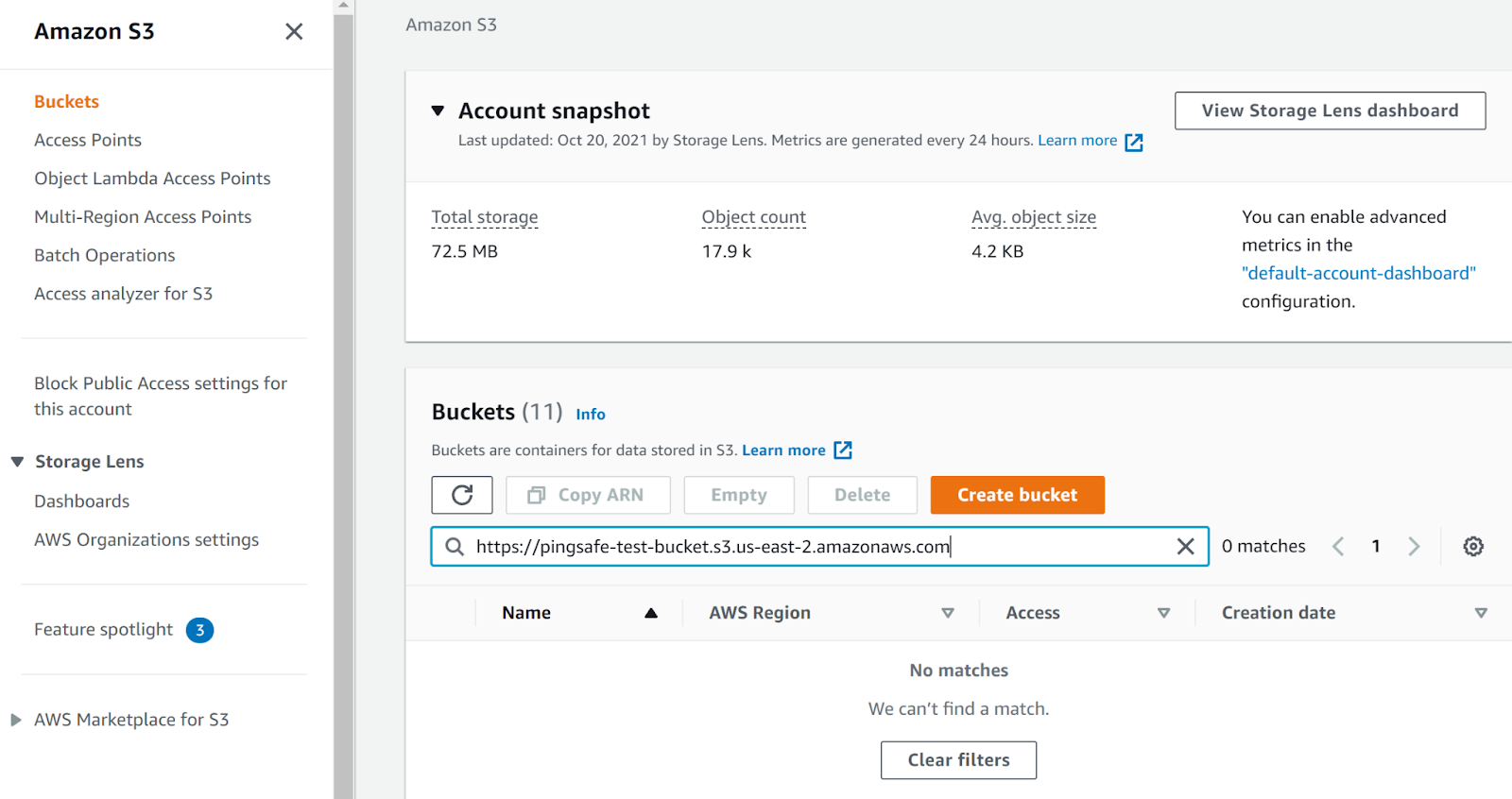
- It is clearly visible that the s3 bucket is missing. This suggests that this is vulnerable to subdomain takeover.
- Repeat steps for other hosted zones.
Steps for remediation :
Ensure that all such Route53 records are removed.
- Login to AWS Management Console.
- Navigate to Route 53 dashboard. (https://console.aws.amazon.com/route53/ )

- Next, move to the “Hosted Zone” in the left navigation panel under Route 53.

- Select the hosted zone to examine.

- Next, check admin.awsexample.com if the Type is CNAME or AAAA. This suggests that it is routing its value to the S3 bucket.
- Copy the link of the S3 bucket and navigate to the S3 Management Console.
- Search for the S3 bucket in the S3 Console.

- It is clearly visible that the s3 bucket is missing. This suggests that this is vulnerable to subdomain takeover.
- Delete the record that was routing its value to the missing S3 bucket.
- Repeat steps for other hosted zones.
References:
