Risk Level: MEDIUM
Description:
This plugin encrypts RDS instances while they are in transit. To have complete control over data encryption and decryption, RDS instances should be encrypted with Customer Master Keys.
Recommended Action: RDS does not currently allow modifications to encryption after the instance has been launched, so a new instance will need to be created with KMS CMK encryption enabled.
About the Service :
Amazon RDS (Amazon Relational Database Service) makes it simple to set up, run, and scale a relational database in the cloud. It offers scalable capacity at a low cost while automating time-consuming administrative activities including hardware provisioning, database setup, patching, and backups.
Impact:
When dealing with production databases that hold sensitive and critical data, not implementing encryption in order to protect your data can lead to unauthorized access.
Steps to reproduce :
- Sign in to your AWS management console.
- Navigate to the RDS dashboard at: https://console.aws.amazon.com/rds/
- On the left navigation panel, under RDS Dashboard, select Databases.
- Select the RDS instance that you want to examine.
- Under the Configuration panel, check the status of Storage Encryption.
- If the current status is set to Disabled, data-at-rest encryption is not enabled for the selected RDS database instance.
- Repeat steps no. 4 – 6 for each RDS instance provisioned in the current region as well as in other AWS regions.
Steps for remediation :
- Sign in to your AWS management console.
- Navigate to the RDS dashboard at: https://console.aws.amazon.com/rds/
- On the left navigation panel, under RDS Dashboard, select Databases.
- Select the RDS instance that you want to examine.
- Click the Actions button from the dashboard top menu and select Take Snapshot.
- On the Take DB Snapshot page that appears, enter the Snapshot name and click on Take Snapshot.
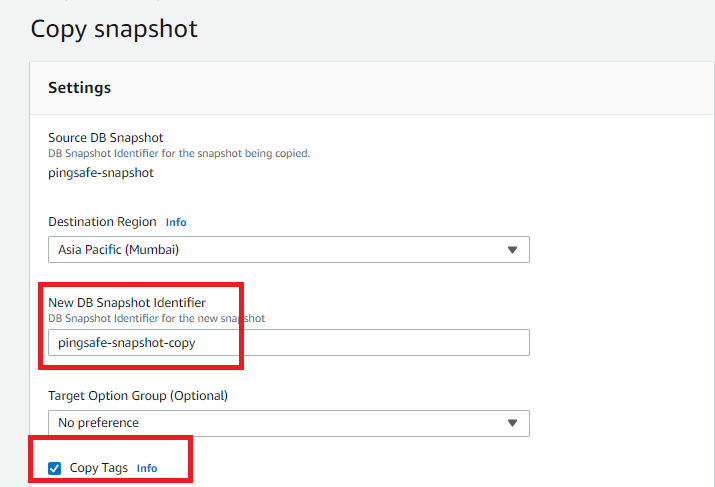
- Open the newly created snapshot, click on Actions, and select Copy Snapshot.
- Make Copy of DB Snapshot page appears, perform the following actions:
- In the New DB Snapshot Identifier field, enter a name for the new snapshot (copy).
- Select the Copy Tags so the new snapshot can have the same tags as the source snapshot.
- Select the Enable Encryption option and select an encryption key for it from the Master Key dropdown list.
- Click Copy Snapshot to create an encrypted copy of the selected instance snapshot.
- Open the new copy screenshot, click on Actions, and select Restore Snapshot.
- This will restore the encrypted snapshot to a new database instance.
- On the Restore Snapshot page that appears, enter a unique name in the DB Instance Identifier field.
- Review the instance configuration details and click Restore DB Instance.
- As soon as the new instance provisioning process is completed (its status becomes available), you can update your application configuration to refer to the endpoint of the new (encrypted) database instance. Once the database endpoint is changed at your application level, you can remove the unencrypted instance.
- Repeat steps no. 4 – 15 for each unencrypted RDS instance provisioned in the current region as well as in other AWS regions.
References:
