Risk Level: Medium
Description
This plugin ensures at-rest encryption is set up for Redshift clusters. Encryption is an important property from the security aspect. It is recommended to have encryption enabled, to protect data present in the cluster.
About the Service
Amazon RedShift: Amazon RedShift is a data warehouse with fast and secure data analyzing features. It is a powerful and robust service powered by Amazon to run SQL queries and even deploy ML (Machine Learning) models on the data. For additional monitoring benefits, it also provides access to real time operational analytics.
Impact
It is highly recommended to encrypt your Amazon RedShift data.
It is highly recommended to properly encrypt Redshift clusters with customer-managed KMS keys. In the absence of a proper AWS KMS key for encryption, the data will remain unaffected. This can provide complete readability to hackers in the case of data exposure.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon RedShift Console. You can use this link (https://console.aws.amazon.com/redshiftv2/) to navigate directly if already logged in.
- From the left navigation pane, click on Clusters.
- A list of clusters will be displayed. Select the cluster you want to examine by clicking on it’s Cluster Name.
- Move to the Properties tab.
- Check if the Encryption is “Enabled”. If not, the vulnerability exists.
- Repeat steps for all the clusters you wish to examine.
Steps for Remediation
Create a new cluster with encryption enabled.
- Log In to your AWS Console.
- Open the Amazon RedShift Console. You can use this link (https://console.aws.amazon.com/redshiftv2/) to navigate directly if already logged in.
- From the left navigation pane, click on Clusters.
- A list of clusters will be displayed. Select the vulnerable cluster by clicking on it’s Cluster Name.
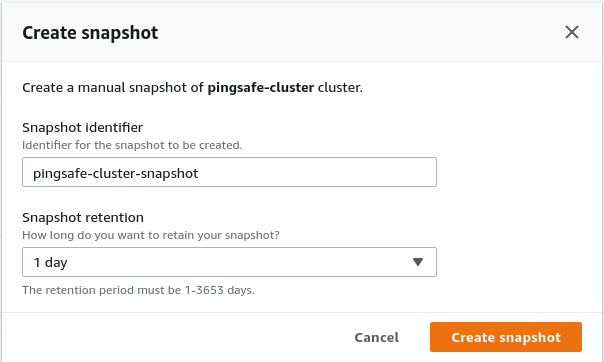
- From the Actions menu, click on Create Snapshot to make a backup.

- Specify a new name and retention period. Click on Create Snapshot.
- After the snapshot is created, you can safely delete the vulnerable cluster. Click on Actions and choose Delete. Uncheck the create final snapshot option as we have already created a snapshot for the same.
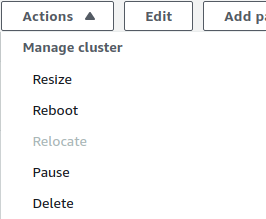
- Now, create a new cluster with the snapshot saved. Move to the Snapshots section from the Left navigation pane.
- Select the snapshot created by clicking on its Name.
- Click on Restore from snapshot from the top right corner.
- Change the Node Type from the dropdown-list. Finally, click on Restore Cluster from snapshot to create the cluster.
- In the Additional Configurations, disable the Default settings and expand the Database Configuration section.
- In the Encryption section, select Encryption with KMS keys.
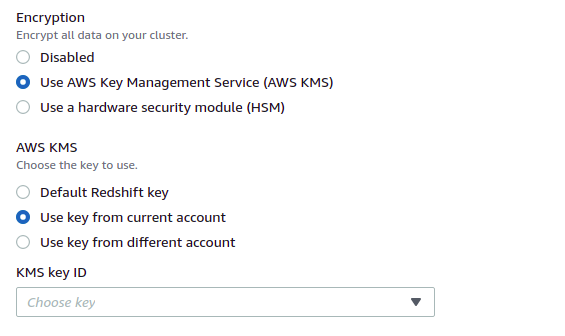
- Repeat steps for all the vulnerable clusters.
