Risk Level: Low
Description
This plugin guarantees that policy is configured to audit that deployed resource locations match their resource group locations. Utilizing Azure Policy to monitor resource location compliance advantages to ensure that new resources are not launched into locations that do not match their resource group
About the Service
Azure Policy:
Azure Policy is a service in Azure that allows you to create policies that enforce and control the properties of a resource. When these policies are used they enforce different rules and effects over your resources, so those resources stay compliant with your IT governance standards. A security policy defines the set of controls that are recommended for resources within the specified subscription. In Azure Security Center, you define policies for your Azure subscriptions according to your company's security requirements and the type of applications or sensitivity of the data in each subscription. For more information, click here.
Impact
No assignment for the resource location matches the resource group location policy. This guarantees an arrangement is designed to review that conveyed asset areas match their asset bunch areas. Utilizing Azure Policy to screen asset area consistency guarantees that new assets are not sent off into areas that don't match their asset bunch. The action to be performed is enabling the built-in Azure Policy definition: Audit resource location matches resource group location
Steps to Reproduce
In order to determine if there is no assignment for the resource location that matches resource group location policy, follow the steps given below:
Using Azure Console-
- Firstly, sign in to the Azure Management Console with your registered organization email address.
- Under Azure Services, choose Subscriptions.
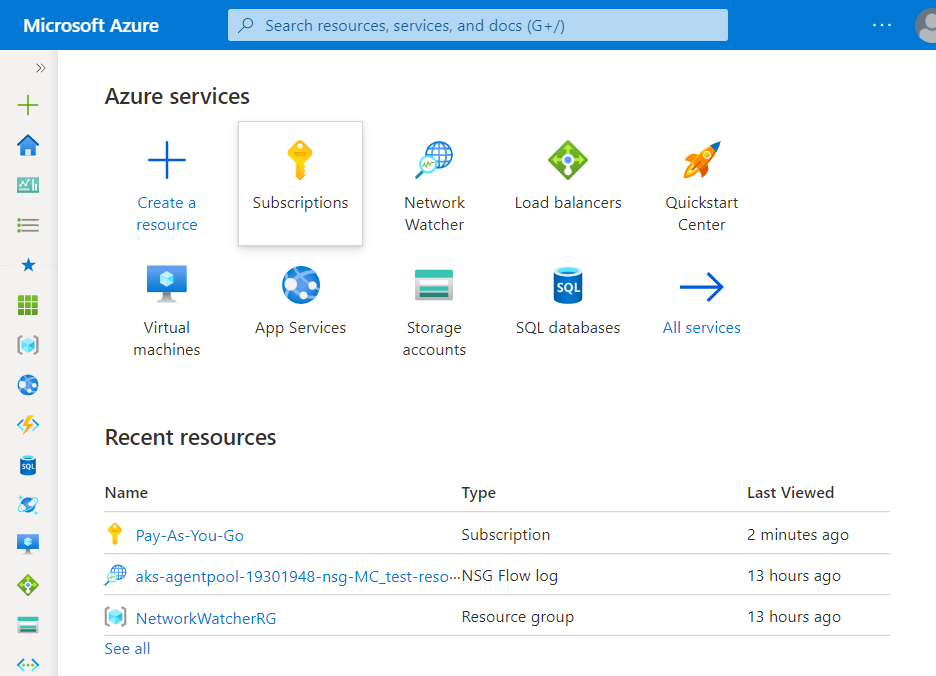
- A new Subscription page will be opened up. Choose the subscription for which the issue has to be examined.
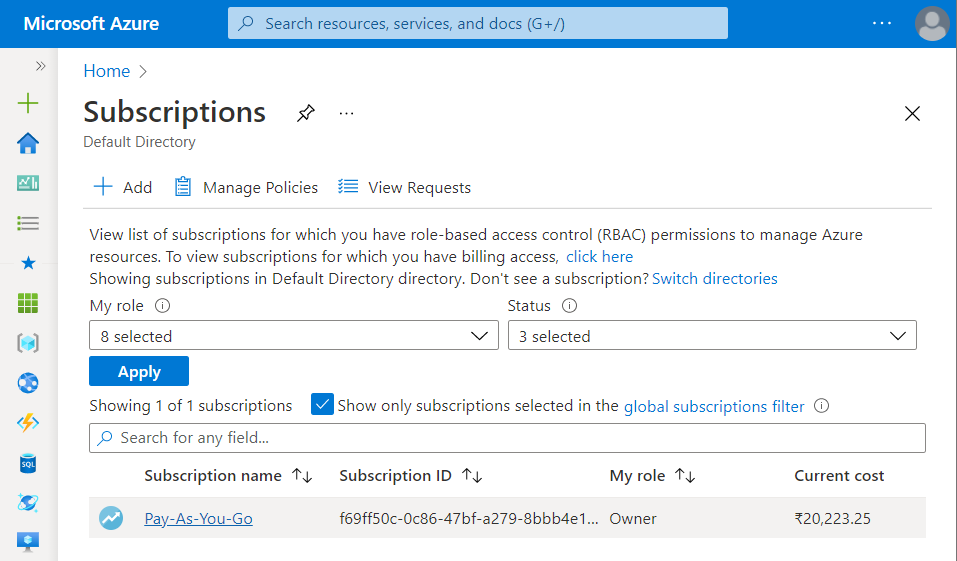
- Now, in the Filter Type Box under the All Services, search for Policy.
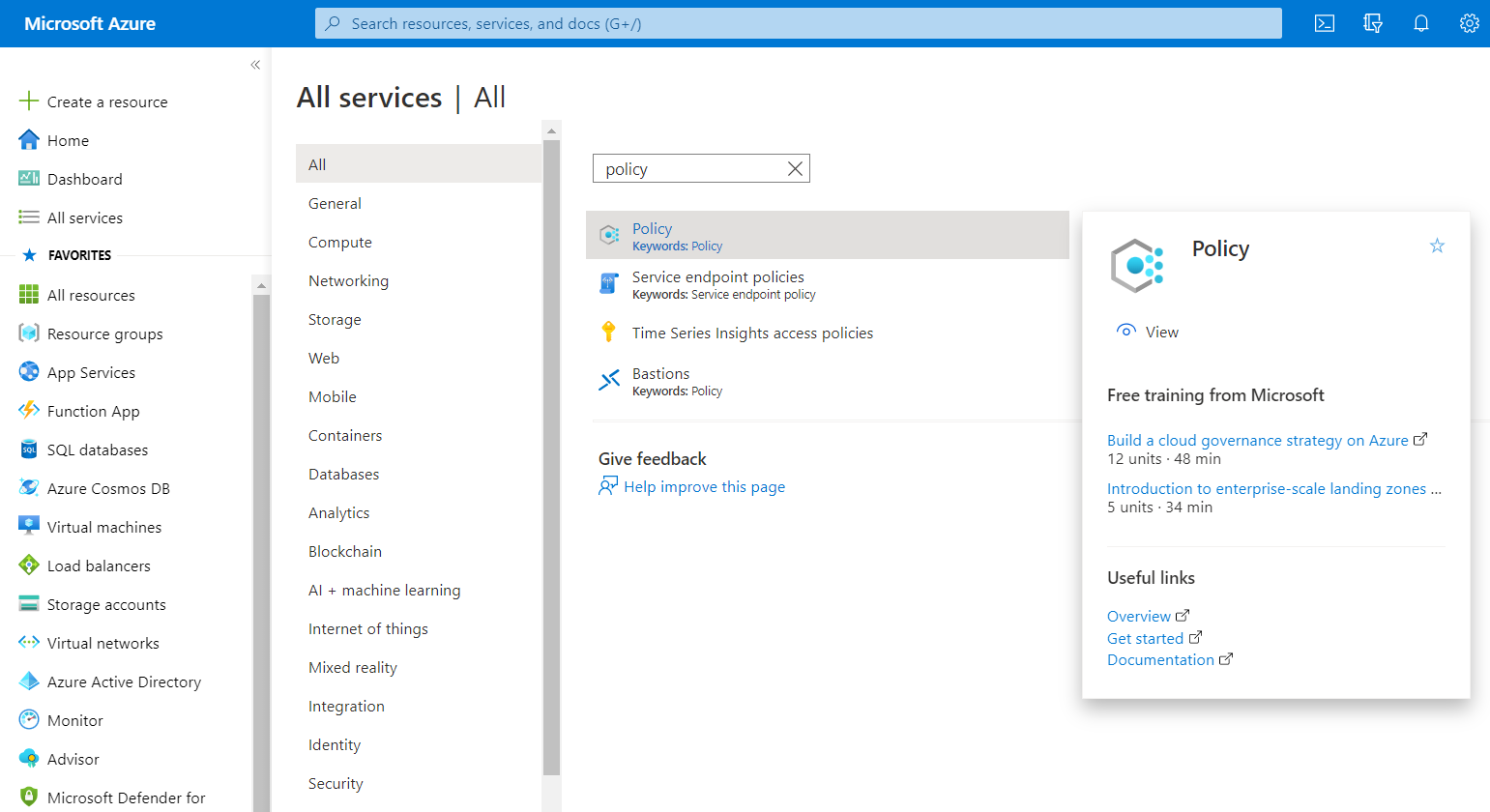
- Click on the Policy nav link. A policy page in your selected subscription will be displayed on the screen.
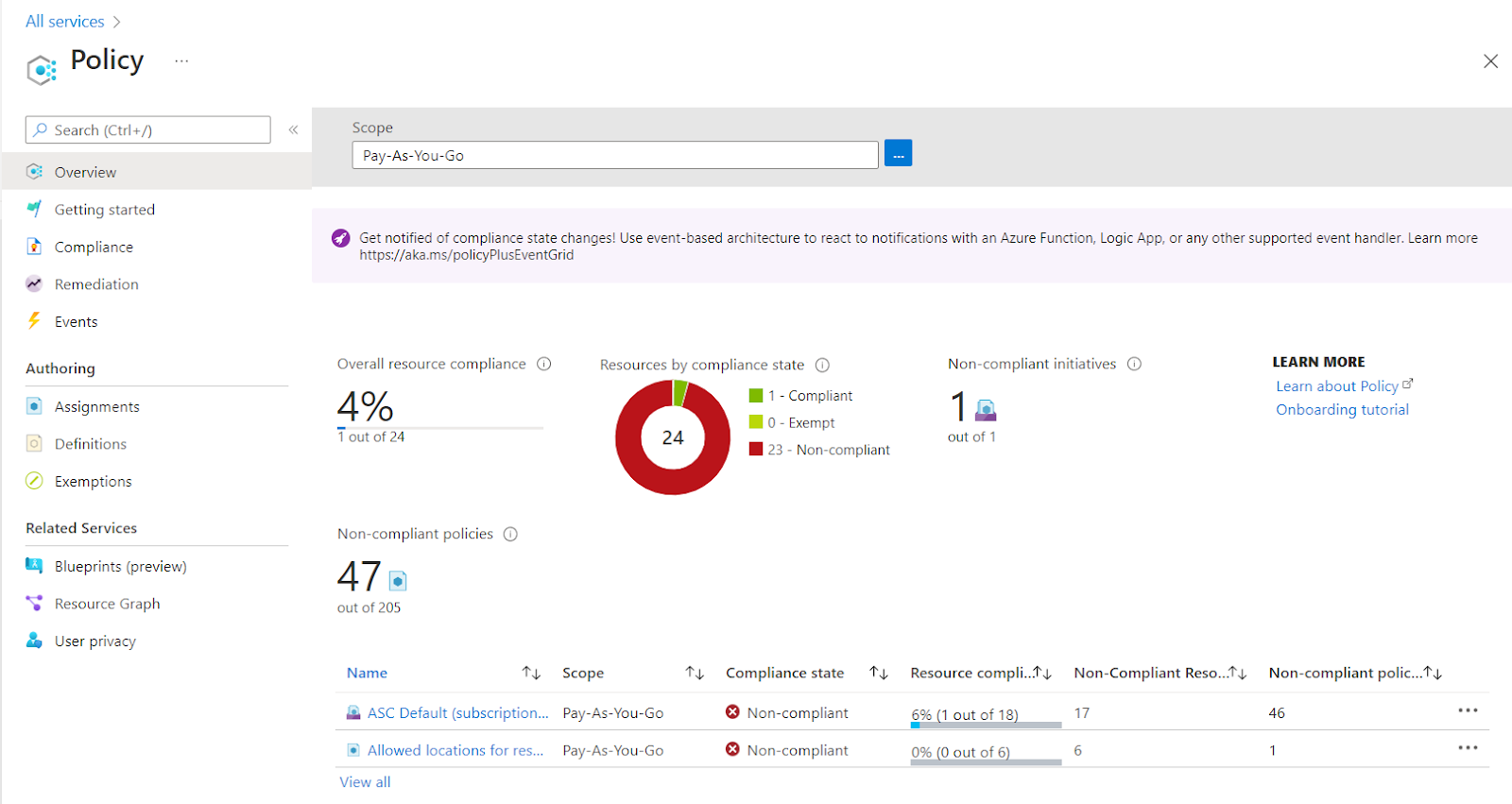
- In the left navigation panel, under the Authorising section click on the Assignments Blade.
- A new page with the list of all the Assignments under Azure Policy will appear on the screen.
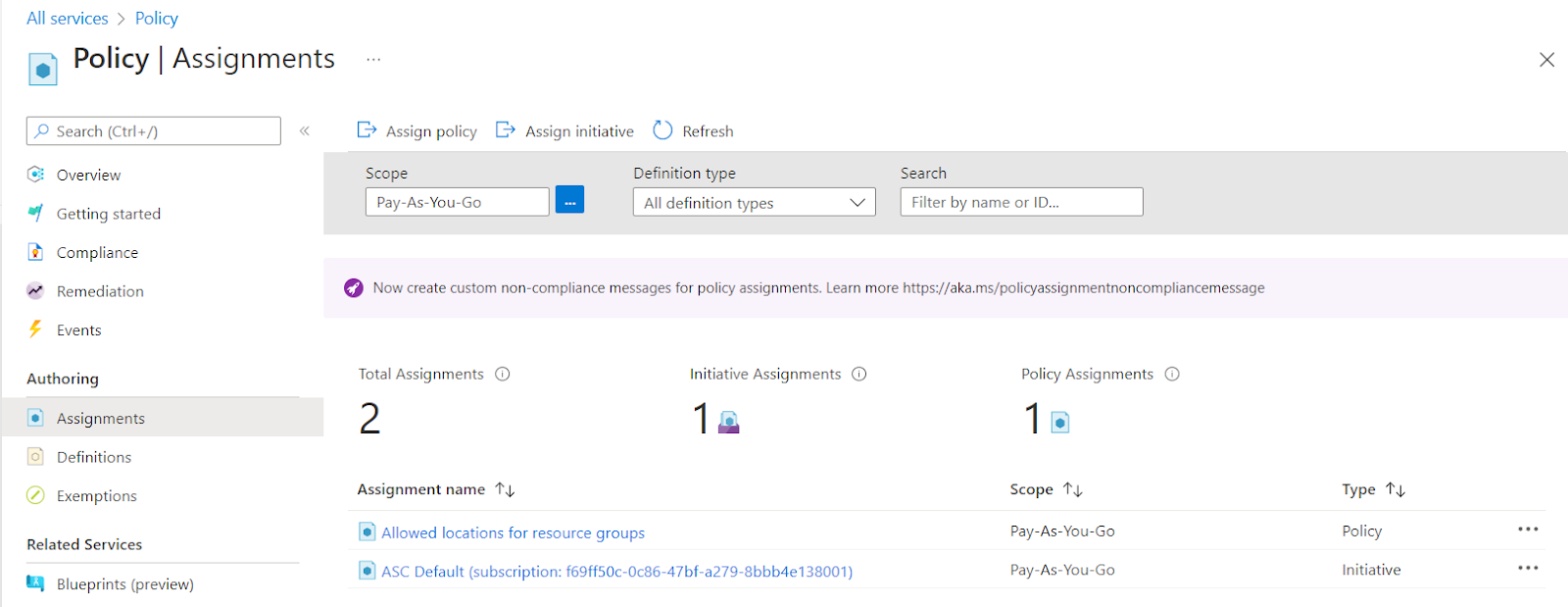
- Click on the Assignment Name, for which you want to examine. A new page with all the details about that assignment will be displayed.
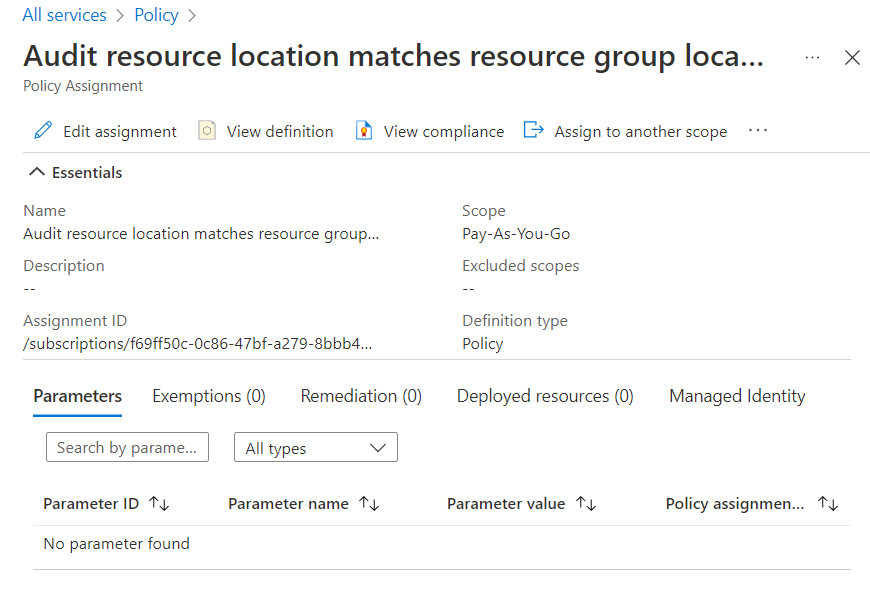
- Click on the View Definition nav link available at the top navbar.
- A new page about the Policy Definition will be displayed. Check the name of the definition. If the definition title is “Resource Location Matches Resource Group” for any one of the assignments, then the vulnerability does not exist.
- Follow the steps above, for other Azure Policy Assignment in the current subscription as well as in other subscriptions in your Azure Cloud.
Steps for Remediation
In order to configure the built-in Azure Policy definition i.e. Audit resource location matches resource group location in your Azure cloud account, follow the steps given below:
Using Azure Console-
- Firstly, sign in to the Azure Management Console with your registered organization email address.
- Under Azure Services, choose Subscriptions.

- A new Subscription page will be opened up. Choose the subscription for which the issue has to be examined.

- Now, in the Filter Type Box under the All Services, search for Policy.

- Click on the Policy nav link. A policy page in your selected subscription will be displayed on the screen.

- In the left navigation panel, under the Authorising section click on the Assignments Blade.

- A new page with the list of all the Assignments under Azure Policy will appear on the screen.

- Now, click on the Assign Policy nav link available at the top navigation bar.
- A new Assign Policy page will be displayed. Click on the Basics tab under Assign Policy.
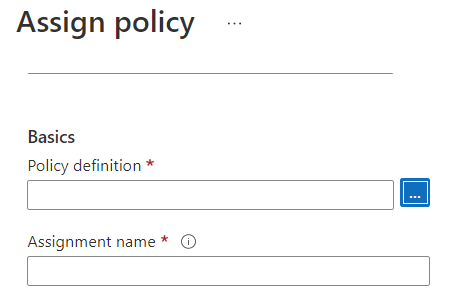
- In the Policy Definition, click on the three dots to view the available definitions.
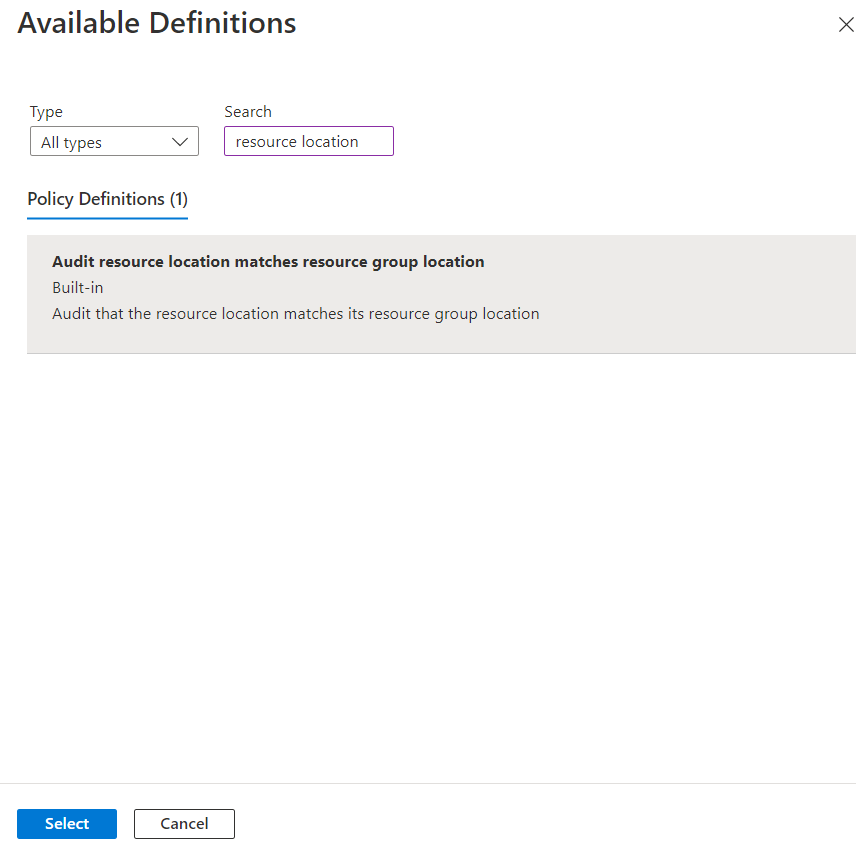
- In the Available Definitions page, search for “Audit Resource location matches resource group location” and select it. Now, click on the Select button available at the bottom.
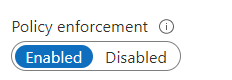
- Assignment Name will automatically be filled with the definition title. However, you may change it according to your preference.
- Click on the Enable option in the policy enforcement. Now, click on the Next button available at the bottom.
- Finally, click on the Review + Create button to create the Assignment Policy. The allowed locations policy is successfully configured for the resource groups
- Follow the steps above, for other Azure Policy Assignment in the current subscription as well as in other subscriptions in your Azure Cloud.
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support
