This plugin guarantees that the root account does not use access keys.
Risk Level: High
Description
This plugin guarantees that the root account does not use access keys. Root account use access keys should be avoided. Since the root account has complete rights throughout the account, adding access keys simply raises the likelihood of penetration. Create predefined roles for IAM users instead.
PingSafe strongly recommends removing access keys for the root account and setup IAM users with limited permissions instead.
Note:
AWS updates the Credential Report every 4 hours, it'll get updated soon please check back later. https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html
About the Service
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact
If anybody obtains root access keys, all services including payment information may be provided unlimitedly in your AWS environment. With the removal of these credentials, the danger of unwanted access to your AWS resources will be reduced substantially.
Steps to reproduce
- Sign-in to AWS IAM management console.
- Click on the “Account Name” and select “My Security Credentials”.
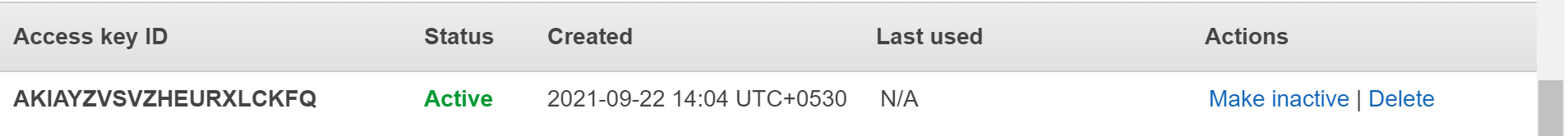
- Look for the “Access Keys” and then under the status column check for keys with “Active” status. If the table displays one or more active keys, the AWS root account is not following the IAM security best practices regarding the protection against unauthorized access.
- Repeat steps for each root account that you want to examine.
Steps for remediation
- Sign-in to AWS management console.
- Click on the “Account Name” and select “My Security Credentials”.
-

- Look for the “Access Keys” and then under the status column check for keys with “Active” status. If the table displays one or more active keys, the AWS root account is not following the IAM security best practices regarding the protection against unauthorized access.

- Remove them by clicking the Delete link available in the Actions column
- Repeat steps for each root account that you want to secure by removing access keys..
