This plugin ensures that S3 buckets have lifecycle configuration enabled to automatically transition S3 bucket objects.
Risk Level: Low
Description
This plugin ensures that S3 buckets have lifecycle configuration enabled to automatically transition S3 bucket objects. S3 bucket should have lifecycle configuration enabled to automatically downgrade the storage class for your objects.
About the Service
Amazon S3: Amazon Simple Storage Service, popularly known as Amazon S3, is a storage space available on the cloud. Using Amazon S3, you can store and retrieve any amount of data. The S3 versioning process maintains versions of an S3 bucket whenever any action is carried out.
Impact
Lifecycle configurations are applied to S3 bucket objects to enable cost-effective storage. The configurations automatically handle the transition and deletion of objects among various tiers of Amazon S3. As a good security practice, it is required to have at least one lifecycle configuration for S3 objects.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon S3 Management Console. You can use this link (https://console.aws.amazon.com/s3) to navigate directly if already logged in.
- A list of S3 buckets will be displayed. Select the bucket you wish to examine by clicking on its name.
- Move to the Management section.

- In the Lifecycle rules section, check if there are any rules present. In case there are no “Enabled” rules present, the vulnerability exists.
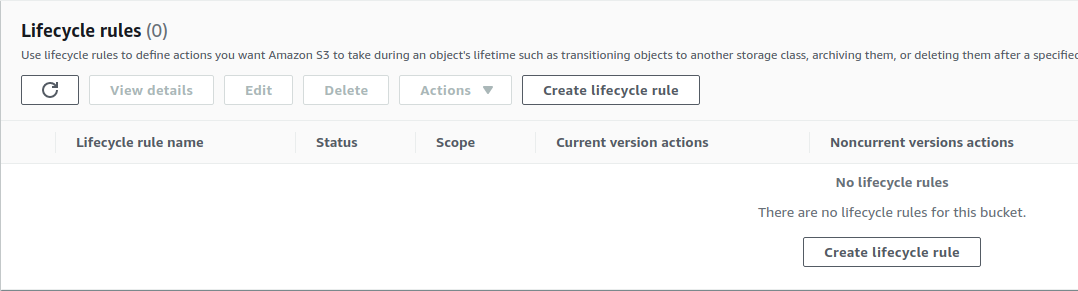
- Repeat steps for all the S3 buckets you want to investigate.
Steps for Remediation
Update S3 bucket and create a lifecycle rule configuration with Enabled status.
Using AWS Console:
- Log In to your AWS Console.
- Open the Amazon S3 Management Console. You can use this link (https://console.aws.amazon.com/s3) to navigate directly if already logged in.
- A list of S3 buckets will be displayed. Select the vulnerable bucket by clicking on its name.
- Move to the Management section.

- In the Lifecycle rules section, click on Create lifecycle rule.

- Give a name to the Lifecycle rule and specify the details. Once completed, click on Create Rule.
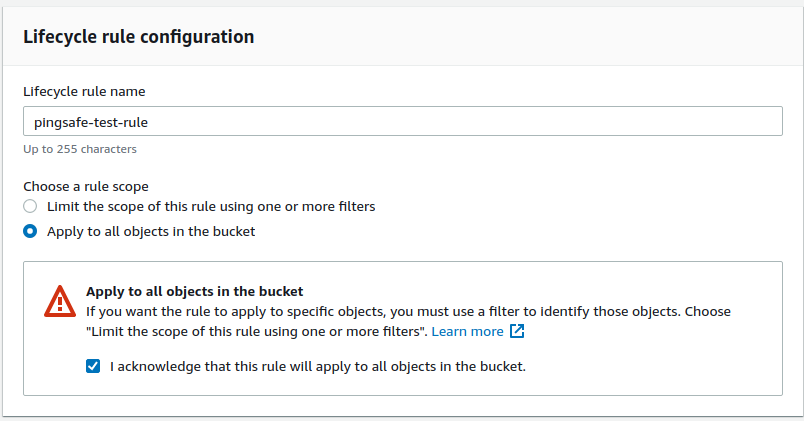
- Repeat these steps for all the vulnerable S3 buckets.
