This plugin ensures that your Amazon S3 buckets are using Multi-Factor Authentication (MFA).
Risk Level: Low
Description
This plugin ensures that your Amazon S3 buckets are using Multi-Factor Authentication (MFA). To prevent the accidental deletion of important S3 objects(files), it is essential to enable MFA for all S3 buckets.
About the Service
Amazon S3: Amazon Simple Storage Service, popularly known as Amazon S3, is a storage space available on the cloud. Using Amazon S3, you can store and retrieve any amount of data. The S3 versioning process maintains versions of an S3 bucket whenever any action is carried out. Please note that the previous versions are not deleted and the extra data stored will incur charges. You can read more about it here.
Impact
In the absence of Multi-Factor Authentication(MFA), an attacker can demand ransom by deleting important S3 files from the S3 bucket in case it is compromised. As a good security measure, it is essential to enable MFA for all S3 accounts.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the Amazon S3 Management Console. You can use this link (https://console.aws.amazon.com/s3) to navigate directly if already logged in.
- A list of S3 buckets will be displayed. Select the bucket you wish to examine by clicking on its name.
- Move to the Properties section.
- In the Bucket Versioning section, check the value Multi-factor authentication (MFA) delete option. If it is set to Disabled, the vulnerability exists.
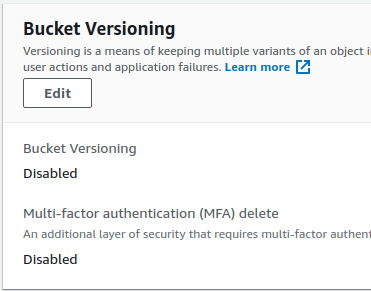
- Repeat steps for all the S3 buckets you want to investigate.
Steps for Remediation
Ensure that your AWS S3 buckets are using Multi-Factor Authentication (MFA) Delete feature.
Note: AWS S3 can only be enabled by the IAM root user account and only on buckets where S3 versioning is enabled.
- Using AWS CLI:
- Configure the AWS CLI.
- Type the following command to enable both versioning and MFA Delete options for the vulnerable bucket.
– aws s3api put-bucket-versioning
–bucket <Bucket_Name>
-versioning-configuration ‘{“MFADelete”:”Enabled”,”Status”:”Enabled”}’
–mfa ‘arn:aws:iam::<aws_account_id>:mfa/root-account-mfa-device <passcode>
Repeat these steps for all the vulnerable S3 buckets.
