Ensure that no Amazon S3 buckets access permissions have been open to the public via ACLs.
Risk Level: High
Description
This plugin identifies the Amazon S3 buckets (Amazon Simple Storage Service) whose access permissions have been open to the public or any AWS Authenticated user. Providing such permissions enables an anonymous user to list (READ), upload, or delete (WRITE) records in S3 buckets. PingSafe strongly recommends not to allow such access to “Everyone” or “AWS Authenticated Users” using ACLs.
About the Service
Amazon S3: Amazon Simple Storage Service, popularly known as Amazon S3, is a storage space available on the cloud. Using Amazon S3, you can store and retrieve any amount of data. Amazon S3 provides easy-to-use management tools to avoid unauthorized access to your data. To know more, read here.
Impact
Exposing an S3 bucket can lead to data leaks, data loss, or unexpected S3 service charges. Hackers can also upload malicious files to the bucket. There have been numerous data breaches in the recent past because of providing “Public” access to S3 buckets. Nearly all such cases were reported due to human error.
Leaky S3 buckets have exposed data of top-notch companies like Netflix and TD Bank. Proper measures must be taken to avoid such errors and secure the Amazon S3 bucket.
Is it part of any compliance?
PCI: PCI requires that cardholder data can only be accessed by those with a legitimate business need. If PCI-restricted data is stored in S3, those buckets should not enable global user access. If the access is set for “Everyone” or “AWS Authenticated Users”, the data will be publicly available and will not fulfill the requirements of PCI.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the S3 Management Console. You can use this link (https://console.aws.amazon.com/s3) to navigate directly if already logged in.
- Select the S3 bucket you wish to investigate and click on the Permissions tab from the top navigation bar.
- Move to the Access Control List (ACL) section in the Permissions Tab and examine the Grantee list present. Here, you will find various user groups.
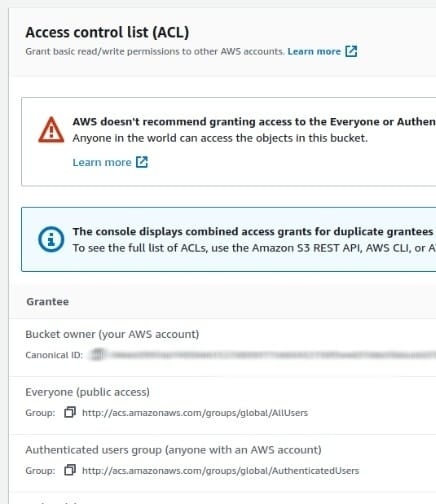
- Look into the “Everyone” group. The permission list for both Objects and Bucket ACL should be empty. If there are List, Read or Write permissions, your S3 bucket can be accessed and modified easily by an anonymous user on the Internet.
- Similarly, examine the “Authenticated users group.” If there is any type of permission granted, the S3 bucket can be accessed by anyone having an AWS account. Any of these configurations is insecure and should be fixed immediately.
- Repeat steps 3 to 6 for all the S3 buckets you want to investigate.
Steps for Remediation
Determine if open access is genuinely needed. If not, update the bucket permissions to restrict access to the owner or specific users.
The steps to restrict access are-
- Log In to your AWS Console.
- Open the S3 Management Console. You can use this link (https://console.aws.amazon.com/s3) to navigate directly if already logged in.
- Select the vulnerable S3 bucket and click on the Permissions tab from the top navigation bar.
- Move to the Access Control List (ACL) section and click on the Edit button at the top right corner.
- Uncheck all the Permissions for the “Everyone” and “Authenticated Users Group” and click on Save Changes to apply for the new permissions.
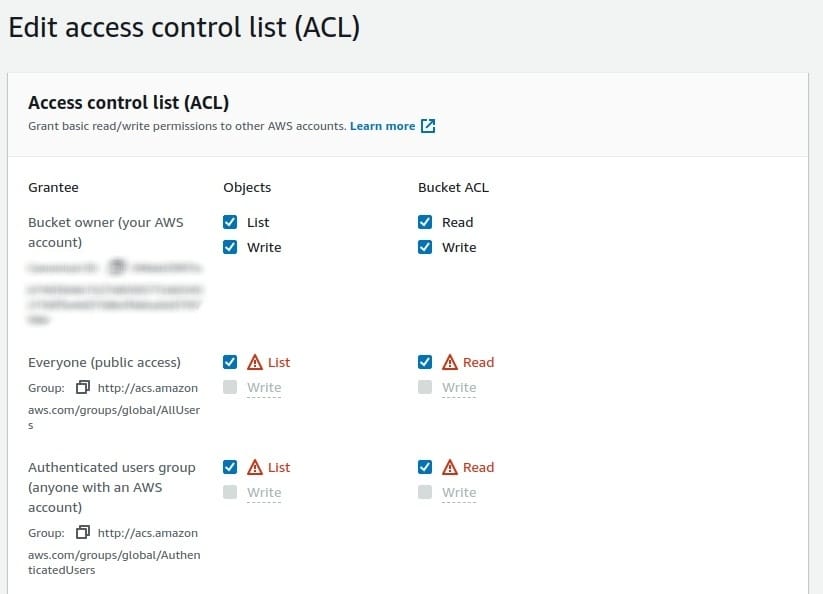
(Uncheck the Permissions for Everyone and Authenticated Users Group) - Repeat the steps from 3 to 5 for all the vulnerable S3 buckets.
References-
https://threatpost.com/leaky-amazon-s3-buckets-expose-data-of-netflix-td-bank/146084/
