RISK LEVEL
Low
DESCRIPTION
This plugin of GCP Identity and Access Management (IAM) ensures that service account keys are rotated within the configured days of creation. Service account keys should be rotated so older keys that might have been lost or compromised cannot be used to access Google services. This is done to guarantee that information can't be gotten to with an old key that may have been lost, compromised, or taken by a third party, which can provide harm eventually.
Configuration Parameters
Key Rotation Interval : This parameter keeps in check that the service account keys are rotated in timely manner to meet security and compliance requirements. An alert is generated if key creation time exceeds this number of days.
By default, value is set to 180 days, so it will generate alert if service account key creation time exceeds 180 days.
ABOUT THE SERVICE
Google Cloud IAM:
IAM, which is an acronym for Identity and Access Management, is the Google Cloud policy. This policy is responsible for specifying access controls for Google Cloud resources. Basically, IAM allows heads to approve who can make a move on explicit assets, giving you full control and permeability to oversee Google Cloud assets halfway. For undertakings with complex hierarchical designs, many workgroups, and many activities, IAM gives a bound together view into security strategy across your whole association, with worked in evaluating to ease consistency processes. For more information, click here.
IMPACT
When an account is created in the Google Cloud Platform (GCP) services, you need to ensure that the user-managed keys are efficiently rotated over a period of the configured number of days or less. Each GCP service account is related with a key pair oversaw by Google and utilized for administration to support validation inside Google Cloud. Google Cloud Platform gives the choice to make at least one client-made due (outer) key set for use outside the cloud account. At the point when another key pair is made, you can download the private key which isn't held by Google, subsequently, you are liable for keeping the hidden key get and dealing with the key revolution. Rotating user-managed administration account keys will essentially diminish the opportunity for an entrance key that is related to a compromised or ended record to be utilized. Google Cloud administration account keys ought to be pivoted to guarantee that information can't be gotten to with an old key that may have been lost, compromised, or taken by a third party, which can provide harm eventually.
STEPS TO REPRODUCE
Using GCP Console-
Ensure that your Google Cloud Platform user-managed service account keys are rotated in a period of the specified days or less, just by following the given simple steps:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.
- Under IAM & Admin section, click on the Service Accounts button. Thence, a new IAM Page will appear.
- The Service Accounts Section will be displayed over the screen where all the service accounts will be listed.
- Select the service account of which you want to examine. Then click on the KEYS option available. Choose the key creation date column under the same.
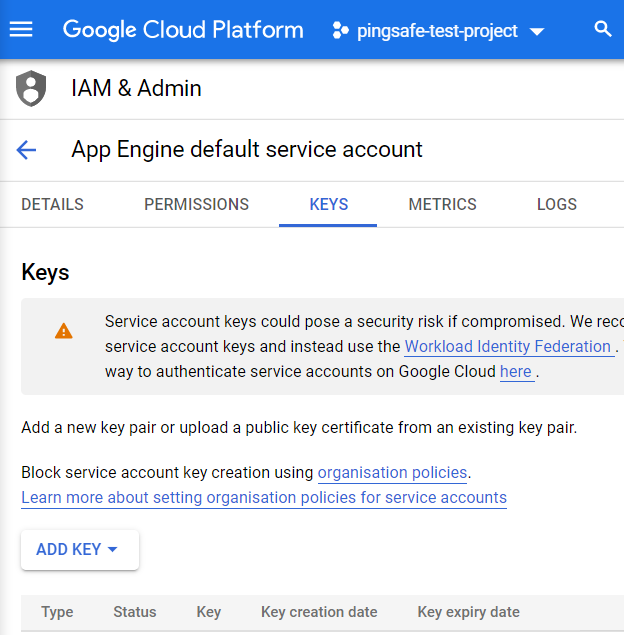
- In case, you find the user-managed keys with a creation date of more than the number of days configured on the PingSafe dashboard, follow the steps for remediation mentioned in the next section. The keys need to be rotated to ensure secured and stable access to the GCP resources of your particular project.
- This way you can check out the user-managed service accounts key rotation period.
- Repeat the steps mentioned above for reviewing accounts in other folders/projects associated with other GCP organizations deployed within your record.
STEPS FOR REMEDIATION
Using GCP Console-
In order to rotate the keys of user-managed service accounts in GCP within a period of the configured days or less, follow the given steps:
- Firstly, use the administrator account for signing up to Google Cloud Platform Console.
- Now, from the top navigation bar, select the GCP Project you want to investigate in.

- From the Navigation Menu on the left, you may find IAM & Admin section under All Products Section, click on it.

- Under IAM & Admin section, click on the Service Accounts button. Thence, a new IAM Page will appear.

- The Service Accounts Section will be displayed over the screen where all the service accounts will be listed.

- Select the service account of which you want to examine. Then click on the KEYS option available. Choose the ADD KEY option under the same, to create a new external key for replacing the old one.

- Choose the CREATE NEW KEY option and proceed.
- Select the key type based on your preference between JSON or P12. Click on create to confirm and save the generated private key.
- Save this key at a safe place in your PC. Click on CLOSE button to go back. Click SAVE button to save your changes.
- Arrange the application(s) to reference the new outside key ID showed in the Keys section and the private key downloaded in earlier steps.
- Once the new outside/client oversaw key is referred to inside your application code, return to the chose administration account configuration page and eliminate the old key.
- Click on the Edit button from the dashboard top menu. Click on the DELETE option close to the earlier user-managed key that you need to erase to eliminate the old key from the chose administration account.
- On the Delete key ID affirmation box, click DELETE to affirm the evacuation activity.
- Now, Click on the SAVE button to save your done changes.
- You may repeat the above steps for other GCP Projects under your organization.
