Ensure that the shielded nodes feature is enabled in your GKE cluster.
Risk Level: Medium
Description
This plugin ensures that the shielded nodes feature is enabled for all Kubernetes clusters. Shielded GKE nodes give a strong cryptographic identity. They aid in the protection of instances against threats, attacks, and privilege escalation.
About the Service
Google Cloud Kubernetes Engine:
The Google Cloud Kubernetes Engine is a Kubernetes-based service that includes a control plane, nodes that house pods, and Google Cloud services. It aids in the modernization of your programs by offering a platform for deploying, managing, and scaling containerized applications. The Google Cloud Console or kubectl can be used to interact with this Google Cloud Kubernetes Engine. To know more, read here.
Impact
If shielded nodes are enabled, even if an attacker has the node credentials, this prohibits attackers from impersonating a node in your GKE cluster. Disabling the shielded nodes feature makes your clusters less secure and increases the risk of attacks.
Steps to Reproduce
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select the GCP project you want to investigate.
- From the navigation panel on the left side of the console, go to Kubernetes Engine and select Clusters. You can use this link here to navigate directly if you’re already logged in.
- Select the cluster you want to investigate from the list of clusters displayed.
- Under the Security section, check the status of Shielded GKE nodes. If it says disabled then the shielded nodes feature is disabled for the selected cluster and Pingsafe strongly recommends you to enable it.
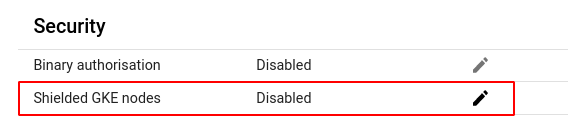
- Repeat steps 4 and 5 for all the clusters you want to investigate in the selected project.
- If you have multiple projects that you want to investigate, repeat steps 2 to 6 for each project in your GCP console.
Steps for Remediation
Determine whether or not you truly require the logging to be disabled. If not, make the necessary changes to enable it using the steps given below.
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select the GCP project you want to investigate.

- From the navigation panel on the left side of the console, go to Kubernetes Engine and select Clusters. You can use this link here to navigate directly if you’re already logged in.

- Select the cluster you want to reconfigure from the list of clusters displayed and go to the DETAILS tab of the selected cluster. (In case you aren’t sure which node pool needs to be configured, follow the steps to reproduce listed above to determine which to choose.)
- Under the Security section, click on the edit icon in the Shielded GKE nodes row to edit its configuration.
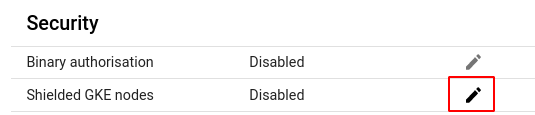
- In the Edit Shielded GKE Nodes pop-up box, check the checkbox for Enable shielded GKE nodes and click on SAVE CHANGES to save the edit. We recommend you to go through the warning message provided before making the changes.
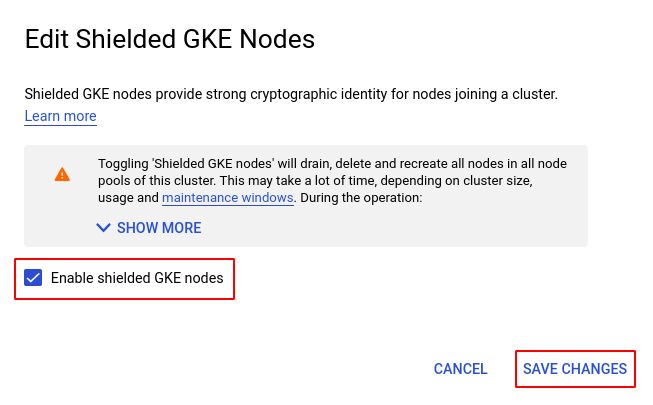
- Repeat steps 4 to 6 for all the clusters you want to reconfigure in the selected project.
- If you have multiple projects, repeat steps 2 to 7 for each project in your GCP console.
