This plugin ensures that cross-account access is prohibited by SNS policies.
Risk Level: MEDIUM
Description:
This plugin ensures that cross-account access is prohibited by SNS policies. To subscribe or send messages, SNS topic policies should be carefully limited. These privileges can be limited using topic policies.
Recommended Action: Update the SNS policy to prevent access from external accounts.
Configuration Parameters
Whitelisted AWS Account Principals: This parameter denotes a comma-separated list of allowed AWS account principals. An issue will be generated if the SNS Policy has Principal other than these specified.
By default, its value is empty. Therefore it will not trust any of the AWS account principals.
Whitelist All AWS Organization Accounts: This parameter implies that all the accounts in the current AWS Organization will be trusted. If set to true, the issue will not be generated if the SNS Policy principal has accounts of the current AWS Organization.
By default, its value is set to false. Therefore, it will not trust any of the AWS organization accounts unless configured under the Whitelisted AWS Account Principals.
About the Service :
Amazon SNS (Amazon Simple Notification Service) is a managed service that delivers messages from publishers to subscribers (also known as producers and consumers). Publishers communicate with subscribers asynchronously by sending messages to a topic, which serves as a logical access point and communication route for subscribers. Clients can subscribe to the SNS topic and receive published messages through any supported endpoint, including Amazon Kinesis Data Firehose, Amazon SQS, AWS Lambda, HTTP, email, mobile push notifications, and mobile text messaging (SMS).
Impact:
Using overly permissive settings that allow unknown cross-account access to your SNS topics might lead to unauthorized behaviours including intercepting and publishing messages, as well as subscribing to the exposed topics. If proper SNS policies are not applied, you risk data leaks and unexpected expenditures on your AWS subscription.
Steps to reproduce :
- Sign in to the AWS Management Console.
- Navigate to the SNS dashboard at: https://console.aws.amazon.com/sns/v2/
- In the left navigation panel, select Topics.
- Select the SNS topic you want to examine.
- Under the Access Policy panel, check out the access policy.
- Check the value of the AWS account ID or the AWS account ARN and verify if it is authentic.
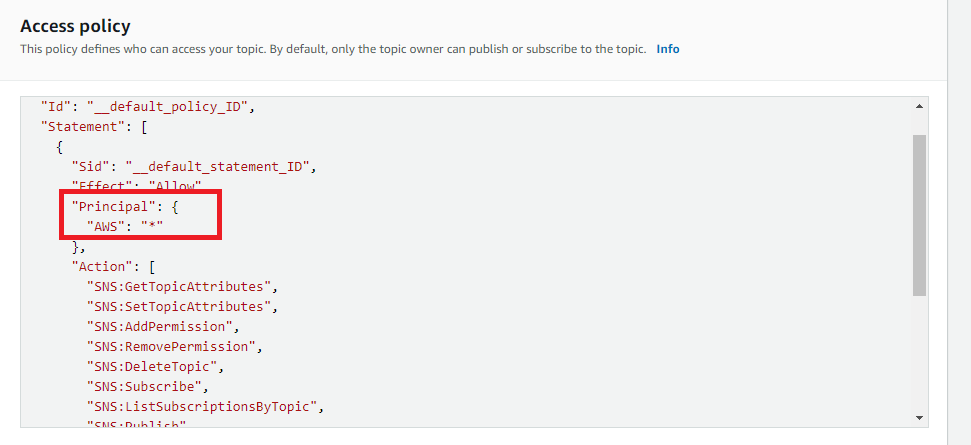
- If not, then the cross-account access to the selected topic is not secured.
- Repeat steps no. 4-7 for other topics in the selected region as well as for other AWS regions
Steps for remediation :
- Sign in to the AWS Management Console.
- Navigate to the SNS dashboard at: https://console.aws.amazon.com/sns/v2/
- In the left navigation panel, select Topics.
- Select the SNS topic you want to examine.
- Under the Access Policy panel, check out the access policy.
- Check the value of the AWS account ID or the AWS account ARN and verify if it is authentic.
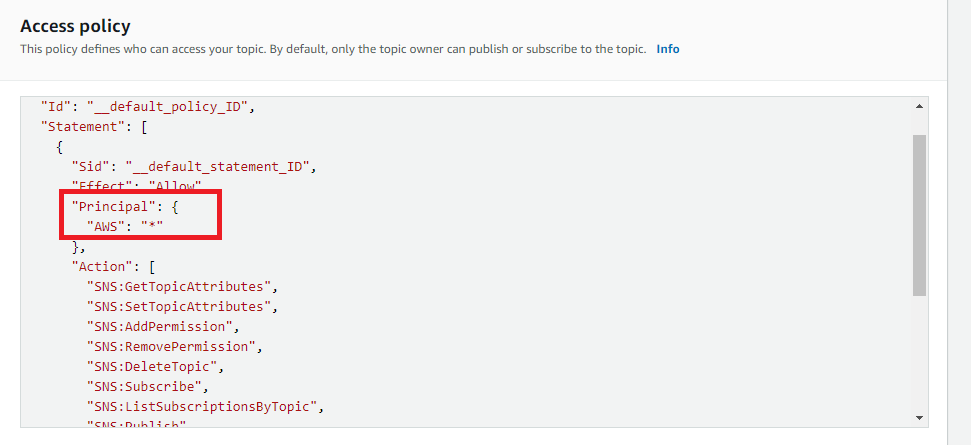
- Replace the ARN value with an authentic value and Click on Save Changes.
- Cross account access is secured for the selected topic.
- Repeat steps no. 4-7 for other topics in the selected region as well as for other AWS regions.
References:
