Risk Level: MEDIUM
Description:
This plugin assures that all TLS certificate versions are not allowed on Microsoft Azure SQL Servers. All TLS connections to the Microsoft Azure SQL server should utilize TLS 1.2 or higher. This option affects all databases connected to the server. TLS encryption for Azure may be configured by administrators. Between clients and Azure systems, Microsoft datacenters can establish a TLS connection.
PingSafe strongly recommends modifying SQL server firewall and virtual network settings to set desired minimum TLS version.
Configuration Parameters
SQL Server Minimum TLS Version: This parameter denotes the minimum desired TLS version for Microsoft Azure SQL Servers. An alert will be generated if it's not configured properly.
By default, the value is set to1.2, so it will show vulnerable if it is other than 1.2.
About the Service :
Azure SQL is a set of managed, secure, and intelligent SQL Server database solutions that run in the Azure cloud. Because Azure SQL is based on the well-known SQL Server engine, applications can be easily transferred while keeping the existing tools, languages, and resources.
Impact :
Clients with Azure Storage accounts can transmit and receive data using the earliest version of TLS, TLS 1.0, and above. You may set up your storage account to require clients to send and receive data using a newer version of TLS to impose tougher security precautions. Any requests performed with an earlier version of TLS will fail if a storage account needs a minimum version of TLS.
Steps to reproduce :
- Sign in to your Azure portal with your Azure account.
https://portal.azure.com/#home
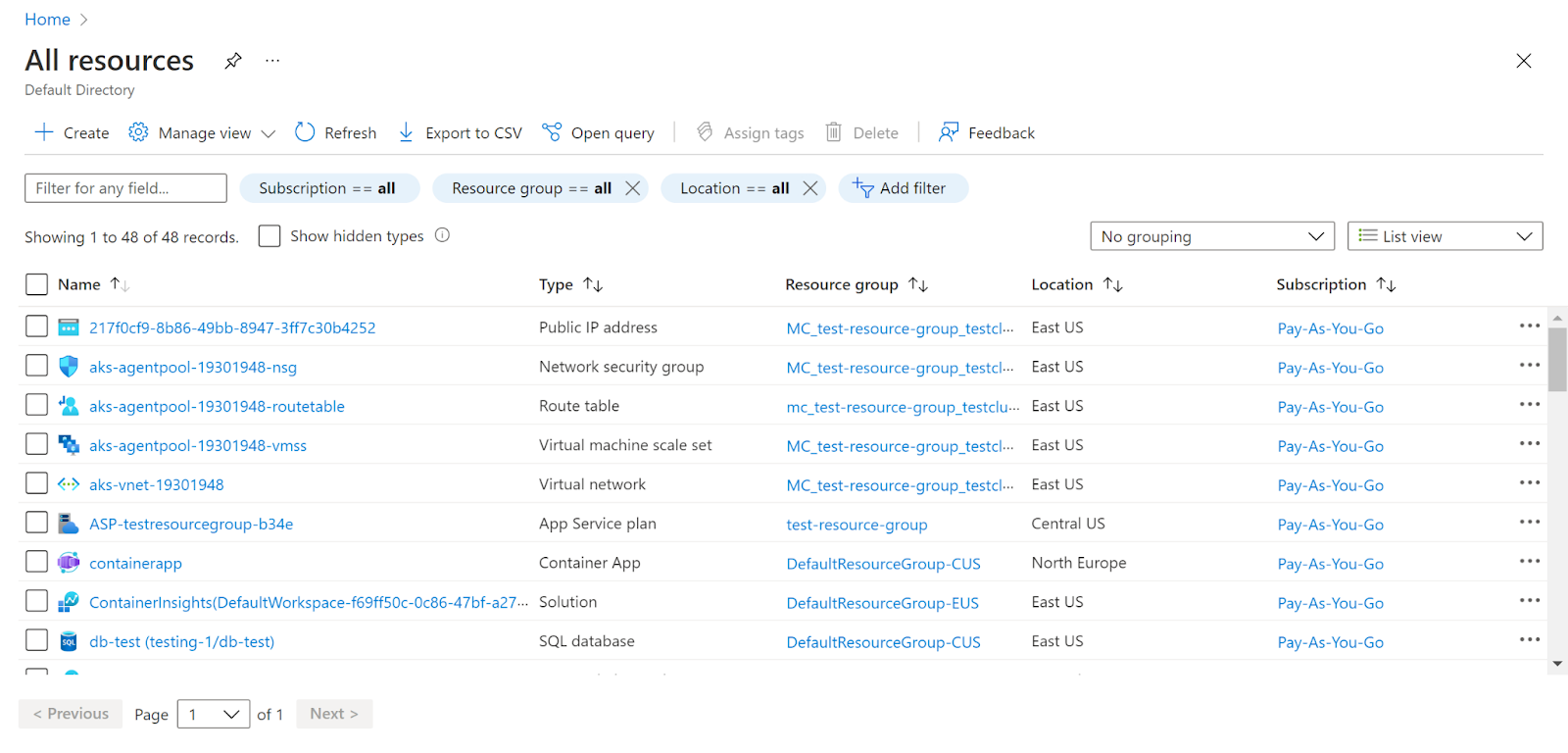
- Navigate to Azure’s All Resources.
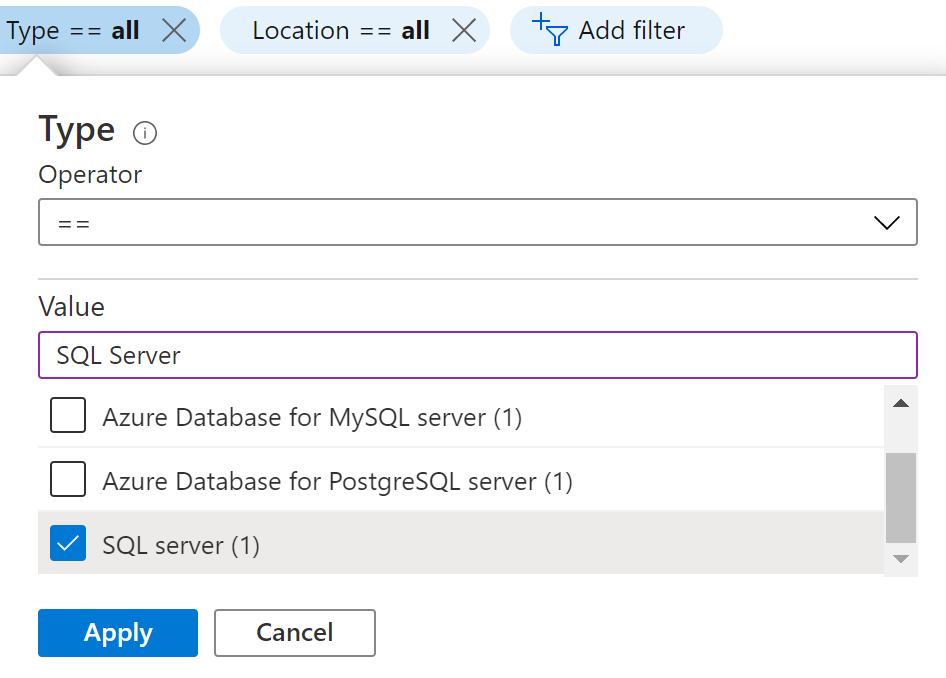
- In the Type filter select the value as SQL Servers and click Apply.
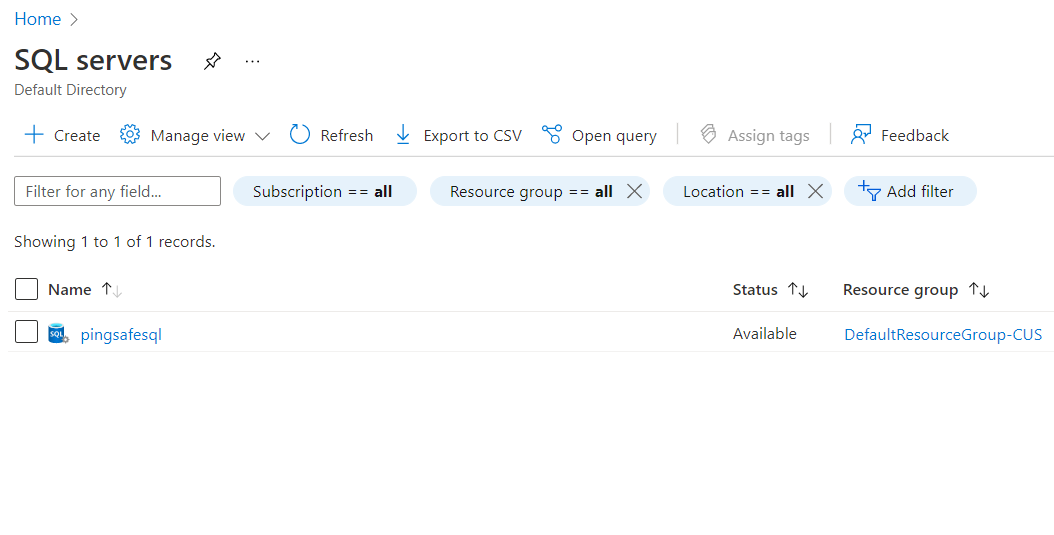
- Next, select the SQL Server that you want to examine.
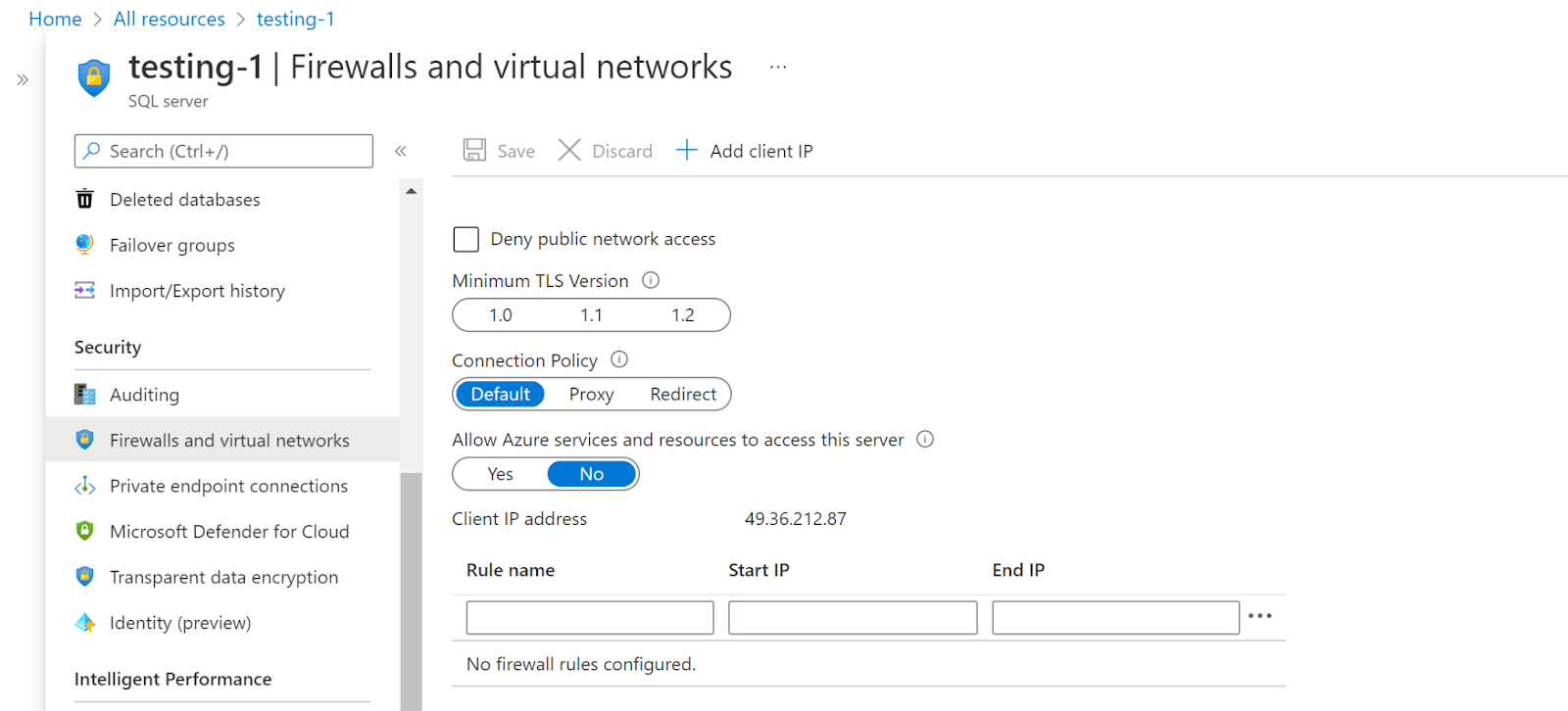
- Click on Firewalls and Virtual Networks under Security in the navigation pane.
- Check if the minimum TLS version is set for the SQL Server or not.
- Repeat the same steps for other servers as well.
Steps for remediation :
- Sign in to your Azure portal with your Azure account.
https://portal.azure.com/#home
- Navigate to Azure’s All Resources.

- In the Type filter select the value as SQL Servers and click Apply.

- Next, select the SQL Server that you want to examine.
- Click on Firewalls and Virtual Networks under Security in the navigation pane.

- Check if the minimum TLS version is set for the SQL Server or not.

- Select the minimum TLS version you want to set for the SQL Server and click Save.
- Repeat the same steps for other servers as well.
References :
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support
