This plugin prevents SQS queues from utilizing default KMS keys for server-side message encryption.
Risk Level: LOW
Description:
This plugin prevents SQS queues from utilizing default KMS keys for server-side message encryption. To have more granular control over the SNS data-at-rest encryption and decryption process, queues should be secured with KMS Customer Master Keys (CMKs) rather than AWS-managed keys.
Recommended Action: Enable encryption using KMS for all SQS queues.
About the Service :
SQS (Amazon Simple Queue Service) is a fully managed message queuing service for decoupling and scaling microservices, distributed systems, and serverless applications. SQS removes the complexity and overhead of managing and operating message-oriented middleware, allowing developers to concentrate on work that is unique. You may send, store, and receive messages across software components using SQS at any volume without losing messages or necessitating the availability of other services.
Impact:
To benefit from more granular control over the queues data encryption/decryption process, make sure your Amazon Simple Queue Service (SQS) queues are utilizing KMS CMK customer-managed keys instead of AWS managed keys (i.e. default keys used when no customer keys are defined).
Steps to reproduce :
- Sign in to your AWS Management Console.
- Navigate to the SQS dashboard at: https://console.aws.amazon.com/sqs/
- Select the SQS queue that you want to examine.
- Choose the Encryption tab from the bottom panel and check for the status of Server Side Encryption.
- First, check if the encryption is disabled. If yes, then the selected SQS service is prone to public visibility.
- If not, check if the key used for encryption is set to "alias/aws/sqs". If yes, then the selected SQS queue data is encrypted using the default master key (AWS-managed key) instead of a KMS CMK customer-managed key.
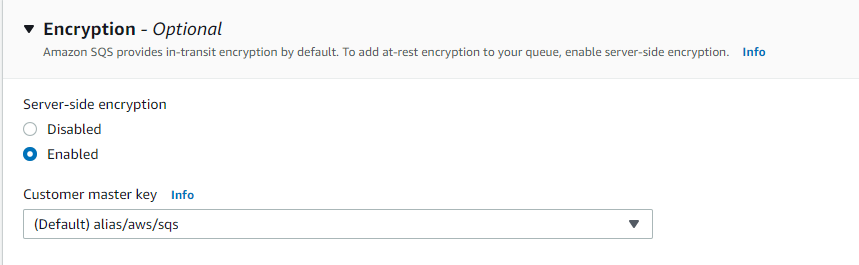
- Repeat steps no. 3-6 for each SQS present in the current region as well as for other regions.
Steps for remediation :
- Sign in to your AWS Management Console.
- Navigate to the SQS dashboard at: https://console.aws.amazon.com/sqs/
- Select the SQS queue that you want to examine.
- Under the Encryption tab, check if server-side encryption is enabled or disabled.
- If disabled, then click on Enabled.
- Now check the value of the Customer Master Key selected from the dropdown menu.
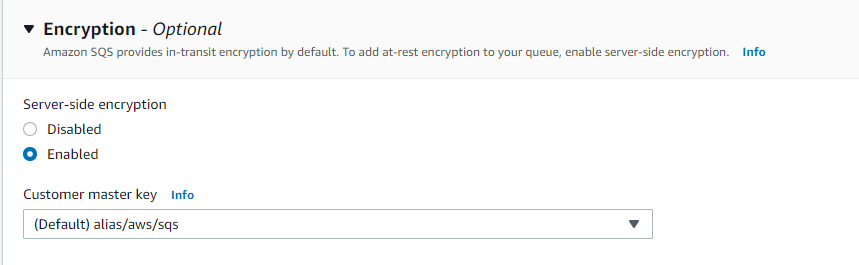
- If the selected key name is “alias/aws/sqs” , then replace it with your Customer Master Key from the dropdown menu.
- Repeat steps no. 3-7 for each SQS present in the current region as well as for other regions.
References:
