Ensures that SSL is enabled on all SQL databases.
Risk Level: Low
Description
This plugin ensures that SQL databases have SSL enabled. The SSL/TLS protocol is the industry standard for encrypting data transferred over the internet. Data in the SQL databases might not be encrypted by default. Thus, SSL must be used to ensure the security of the data during transmission, especially when an SQL instance is using its public IP address.
About the Service
Google Cloud SQL:
Google Cloud SQL is a relational database for MySQL, PostgreSQL, and SQL Server that is fully managed. It automates database provisioning, storage capacity management, replication, and backups while lowering maintenance costs. It can be set up easily using the built-in migration tools and lets you scale your instances effortlessly. To know more about Cloud SQL, read here.
Impact
Without using SSL, the connection will not remain secure and anyone on the internet will be able to watch and intercept your traffic. Since the database is not encrypted without SSL, all the sensitive data will be exposed to the public making it vulnerable to attacks.
Steps to Reproduce
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select the GCP project you want to investigate.
- From the navigation panel on the left side of the console, go to SQL. You can use this link here to navigate directly if you’re already logged in.
- Set Type to SQL Server in the Filter box to only see SQL Server database instances.
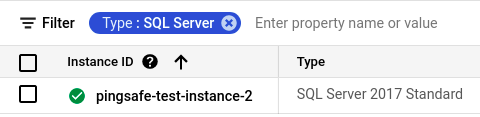
- Select the ID of the SQL instance you want to investigate from the list of instances available and click on the CONNECTIONS tab to check the connectivity configurations of the selected instance.
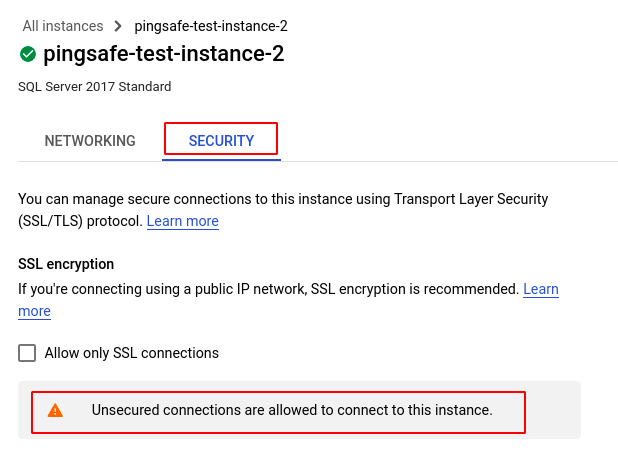
- In the SECURITY tab, under SSL encryption, if it says “Unsecured connections are allowed to connect to this instance.” then SSL is disabled for this SQL Server database.
- Repeat steps 5 and 6 for all the SQL instances you want to investigate in the selected project.
- If you have multiple projects, repeat steps 2 to 7 for each project in your GCP Console.
Steps for Remediation
Determine whether or not you truly require SSL disabled for your SQL instances. If not, make the necessary changes to enable it using the steps below.
Using GCP Console-
- Log In to your GCP Console.
- From the top navigation bar, select the GCP project you want to investigate.

- From the navigation panel on the left side of the console, go to SQL. You can use this link here to navigate directly if you’re already logged in.
- Set Type to SQL Server in the Filter box to only see SQL Server database instances.

- Select the ID of the SQL instance you want to reconfigure in the list of instances available and click on the CONNECTIONS tab. (In case you aren’t sure which SQL instance needs to be configured, follow the steps to reproduce listed above to determine which to choose.)

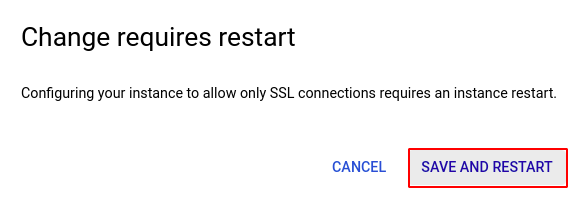
- In the SECURITY tab, under SSL encryption, check the Allow only SSL connections option to enable SSL. Click SAVE AND RESTART in the confirmation box.
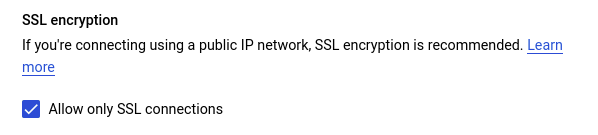
- If the SQL Server instance is using a public IP address, add the IP addresses of your users as authorised networks by clicking on the ADD NETWORK option under Authorised networks.
- Enter your desired name and network in CIDR format and click SAVE to save the changes.
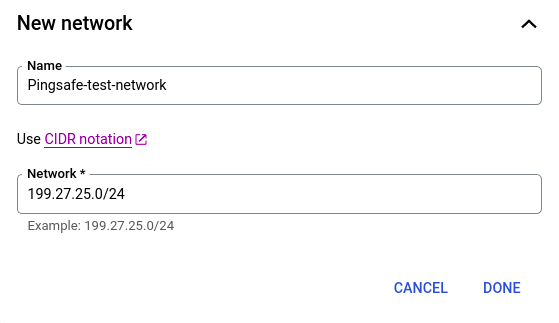
- Repeat steps 5 to 8 for all the SQL instances you want to reconfigure in the selected project.
- If you have multiple projects, repeat steps 2 to 9 for each project in your GCP console.
