Risk Level: LOW
Description:
This plugin uses Customer Managed Keys to encrypt SQL Server TDE Protector. Enabling Customer Managed Key in the TDE Protector gives you more control and transparency over your encryption keys, as well as increased security. With client-managed TDE, the customer is in charge of key lifecycle management (key creation, upload, rotation, and deletion), key use authorization, and auditing of key activities.
PingSafe strongly recommends ensuring that a Customer managed key is set for the Transparent Data Encryption of each SQL Server.
About the Service :
Azure SQL is a set of managed, secure, and intelligent SQL Server database solutions that run in the Azure cloud. Because Azure SQL is based on the well-known SQL Server engine, applications can be easily transferred while keeping the existing tools, languages, and resources.
Impact :
By encrypting data at rest, transparent data encryption (TDE) helps safeguard Azure SQL databases from unauthorized activities. Without needing changes to your database application, it performs real-time encryption and decryption of the database, its related backups, and transaction log files maintained at rest. Using the symmetric key called the database encryption key, the feature encrypts the storage of an entire SQL database.
Steps to reproduce :
- Sign in to your Azure portal with your Azure account.
https://portal.azure.com/#home
- Navigate to Azure’s All Resources.
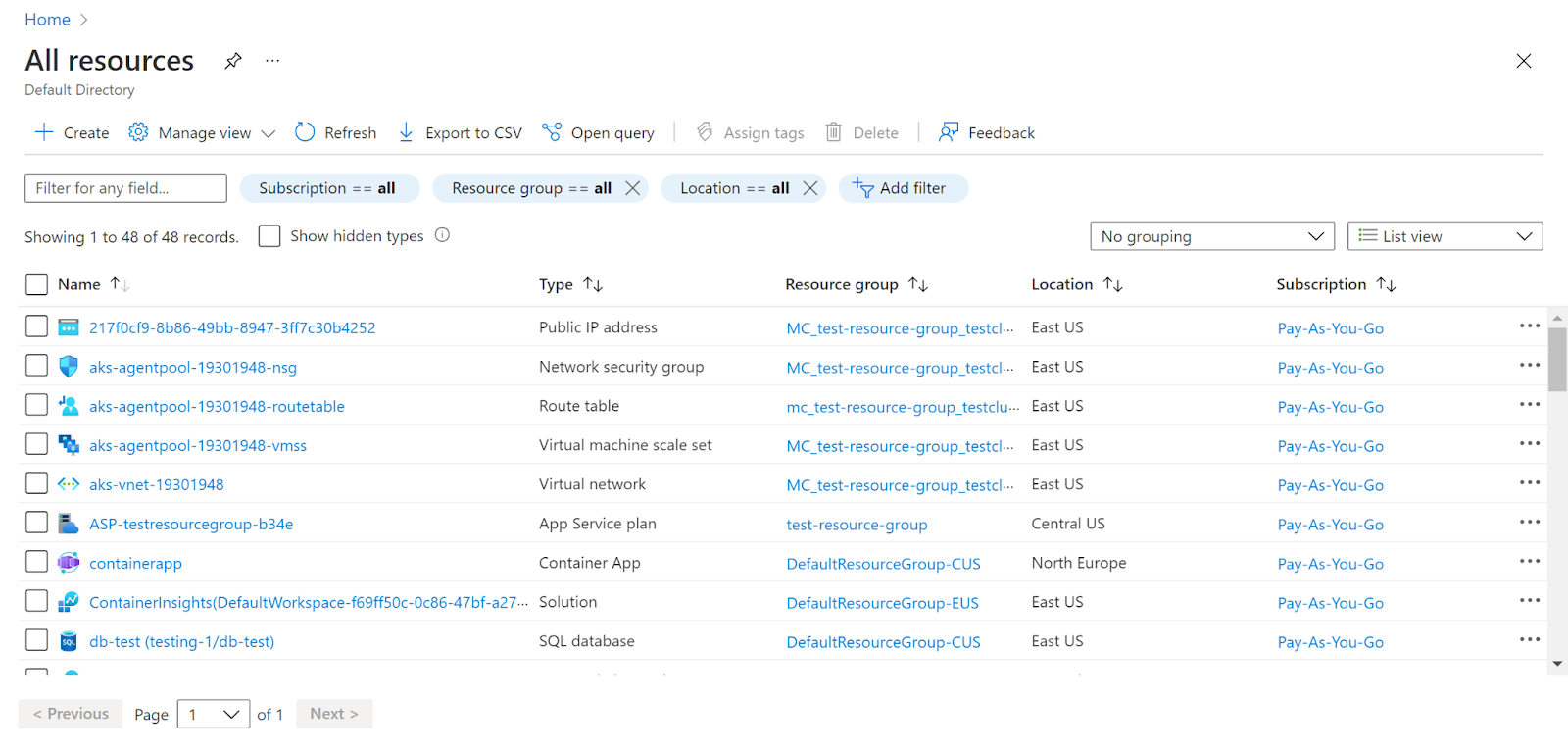
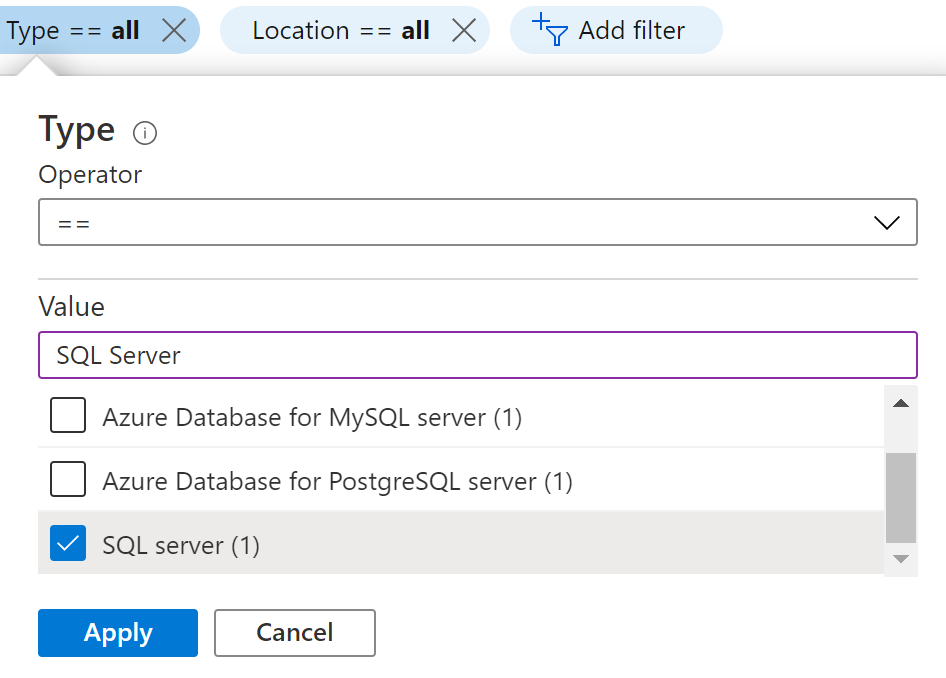
- In the Type filter select the value as SQL Servers and click Apply.
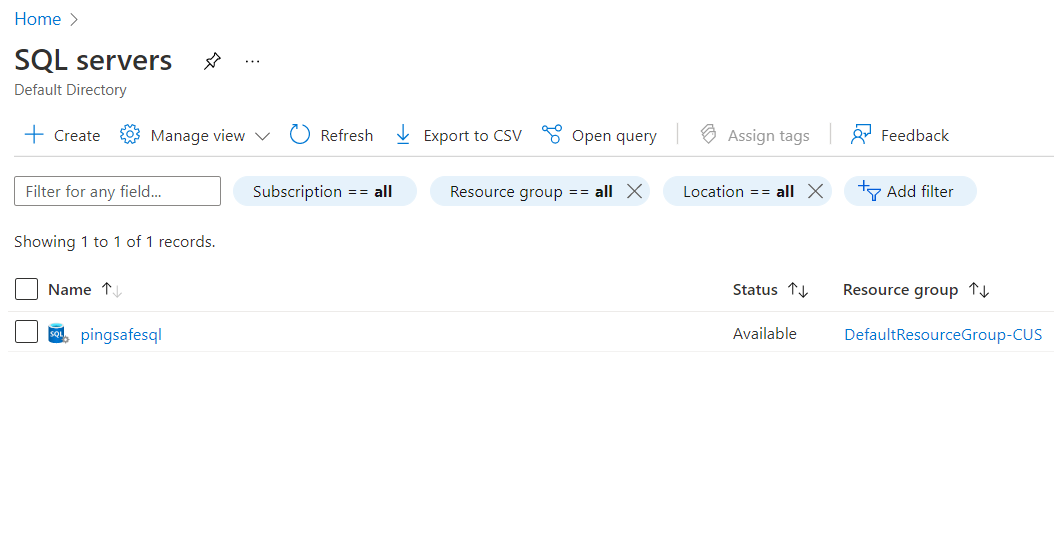
- Next, select the SQL Server that you want to examine.
- Click on Transparent Data Encryption under Security in the navigation pane.
- Check if TDE Protector encryption is enabled or not.
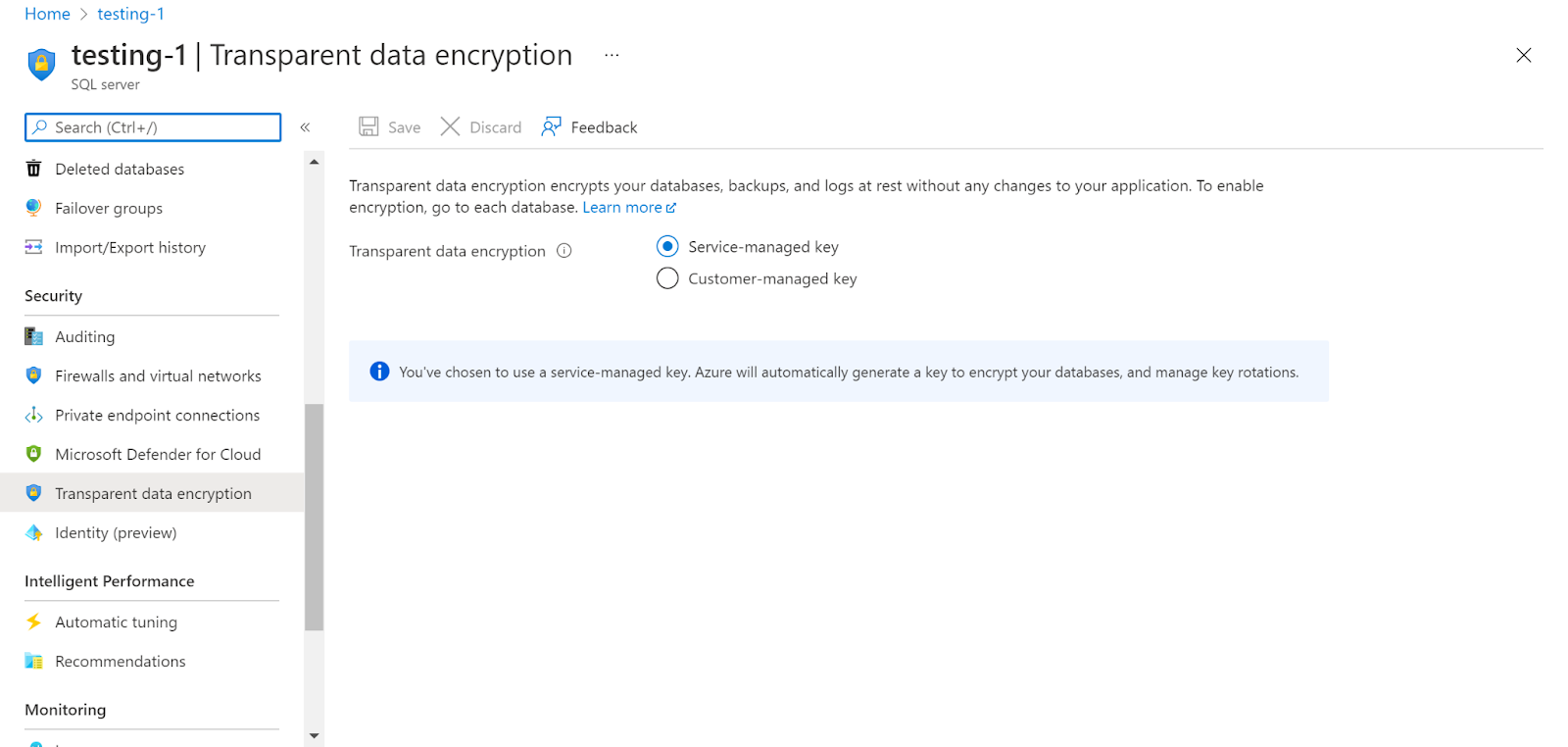
- Repeat the same steps for other servers as well.
Steps for remediation :
- Sign in to your Azure portal with your Azure account.
- https://portal.azure.com/#home
- Navigate to Azure’s All Resources.
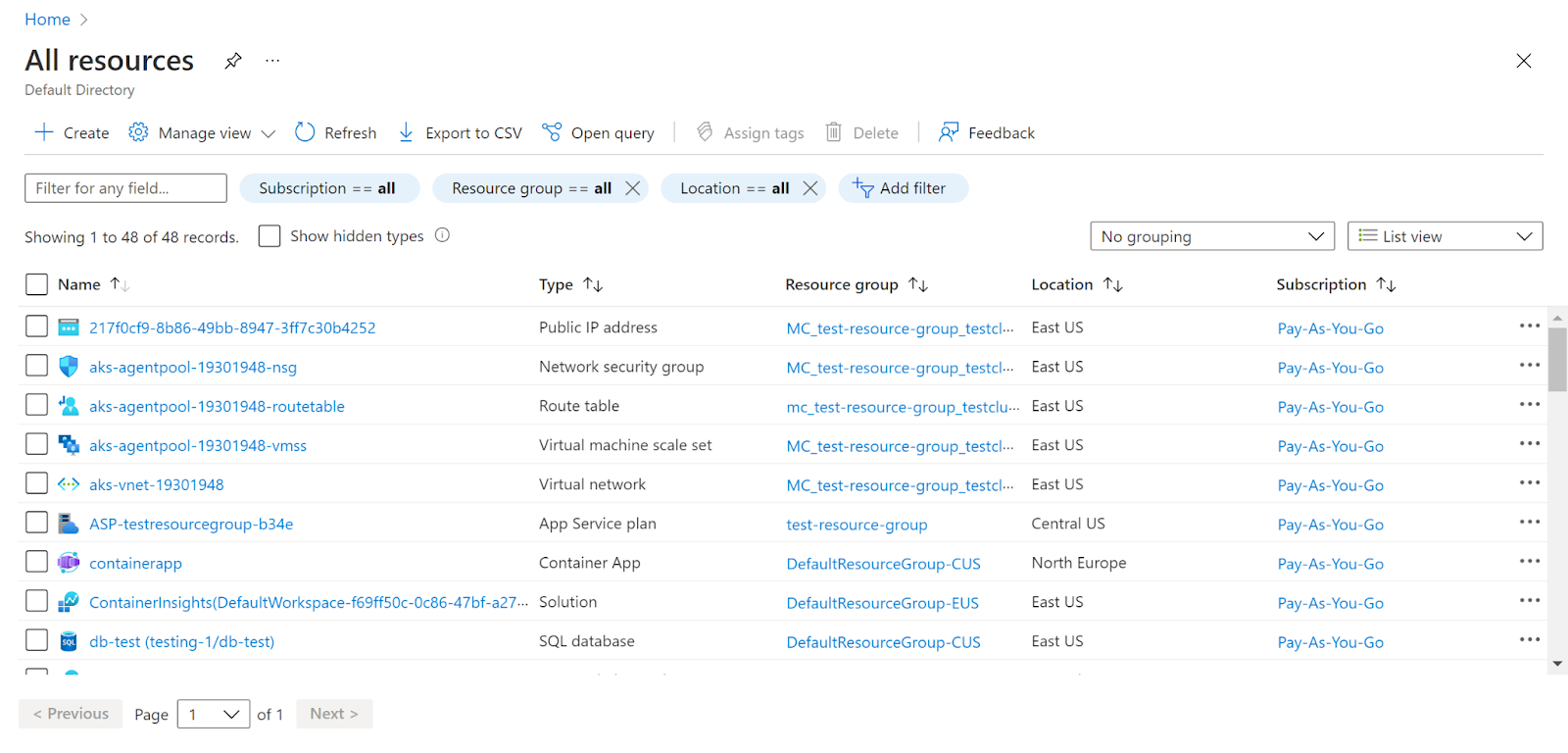
- In the Type filter select the value as SQL Servers and click Apply.
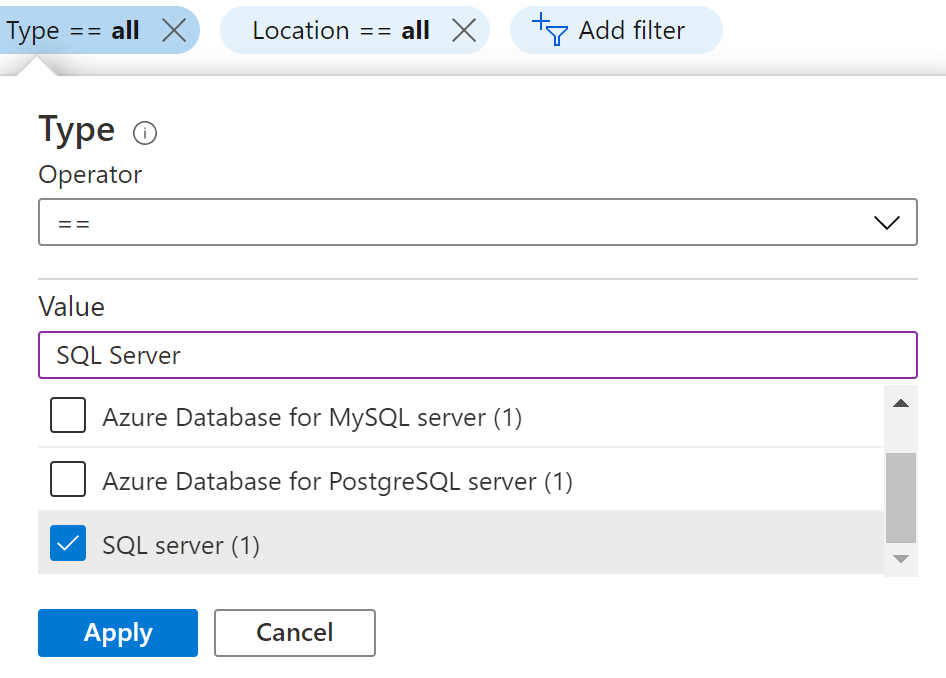
- Next, select the SQL Server that you want to examine.
- Click on Transparent Data Encryption under Security in the navigation pane.
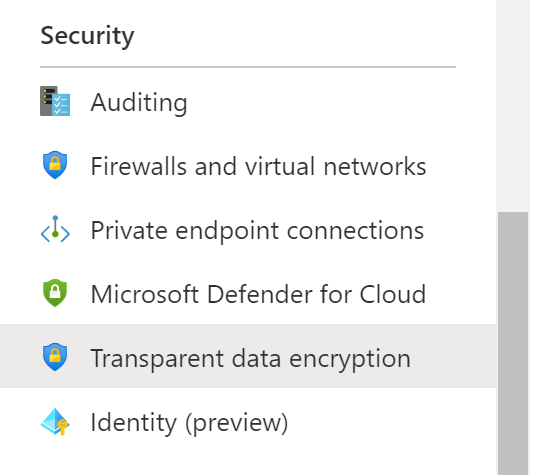
- Check if TDE Protector encryption is enabled or not.
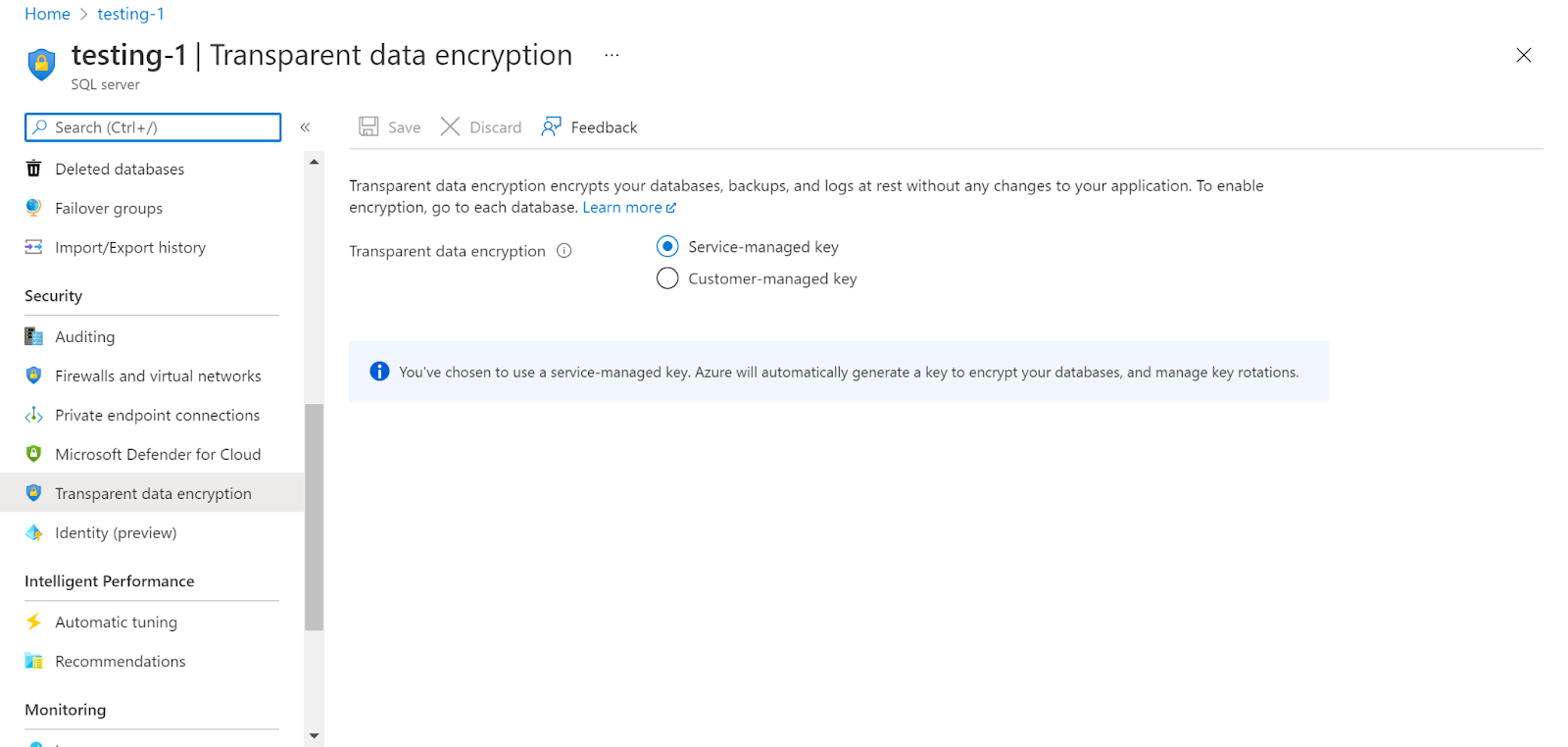
- Click on Customer Managed Key, there will be two options to enable TDE Protector Encryption i.e. Select a key or Enter a key identifier.
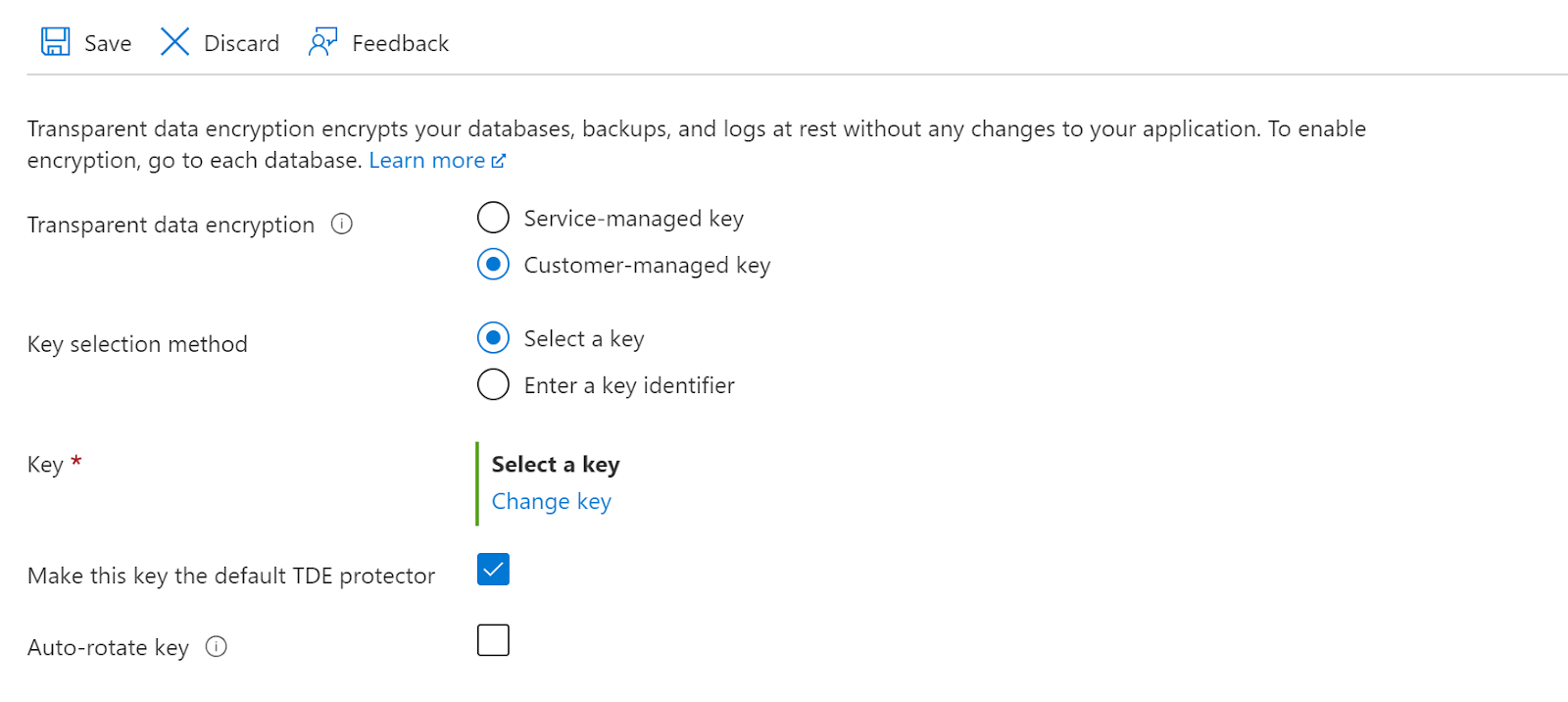
- If we click on Select a key, we need to click on Change key and then fill in the required details of the key from the Key vault in the Select a key page.
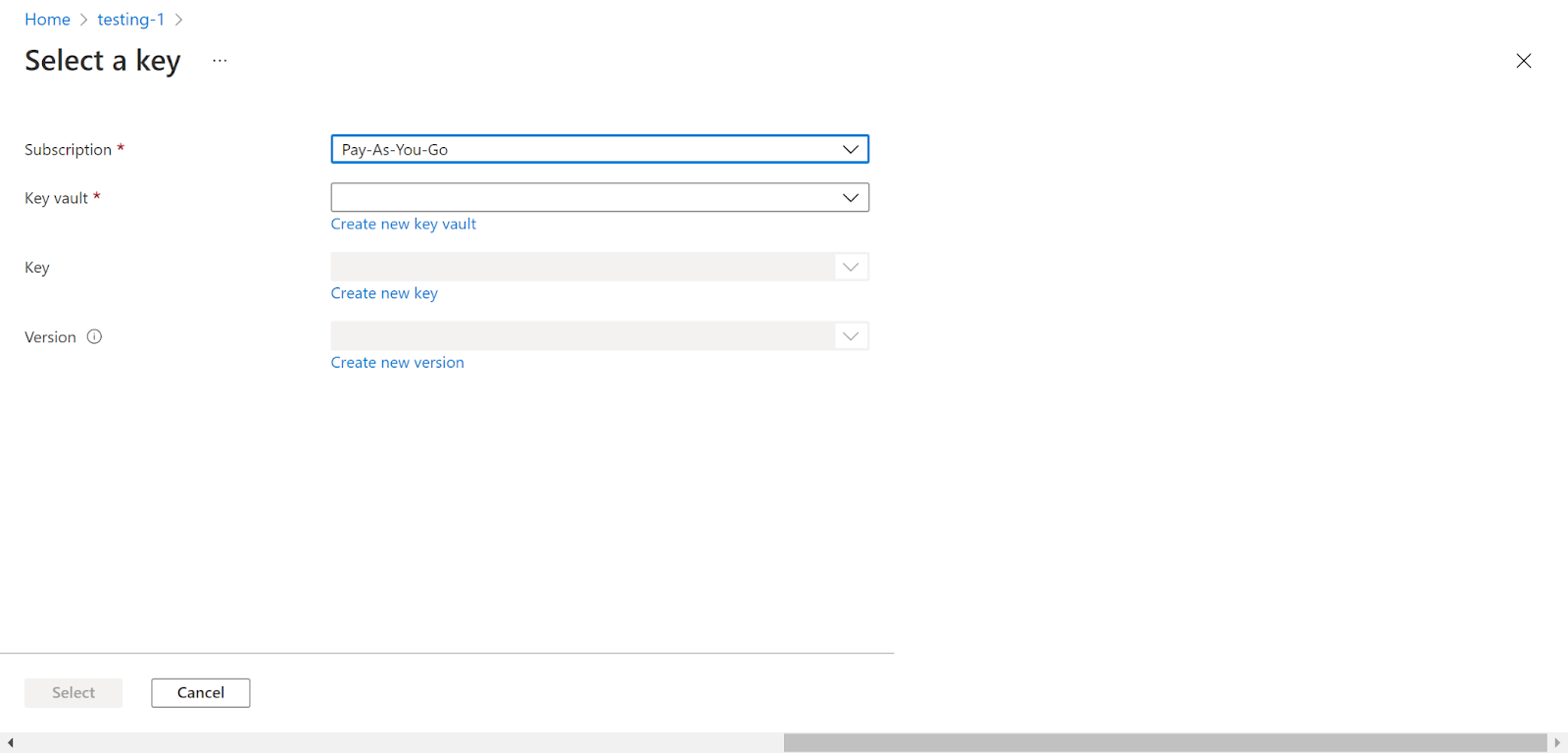
- Next click on the Select button to enable the key.
- The other option is to enter a Key identifier.
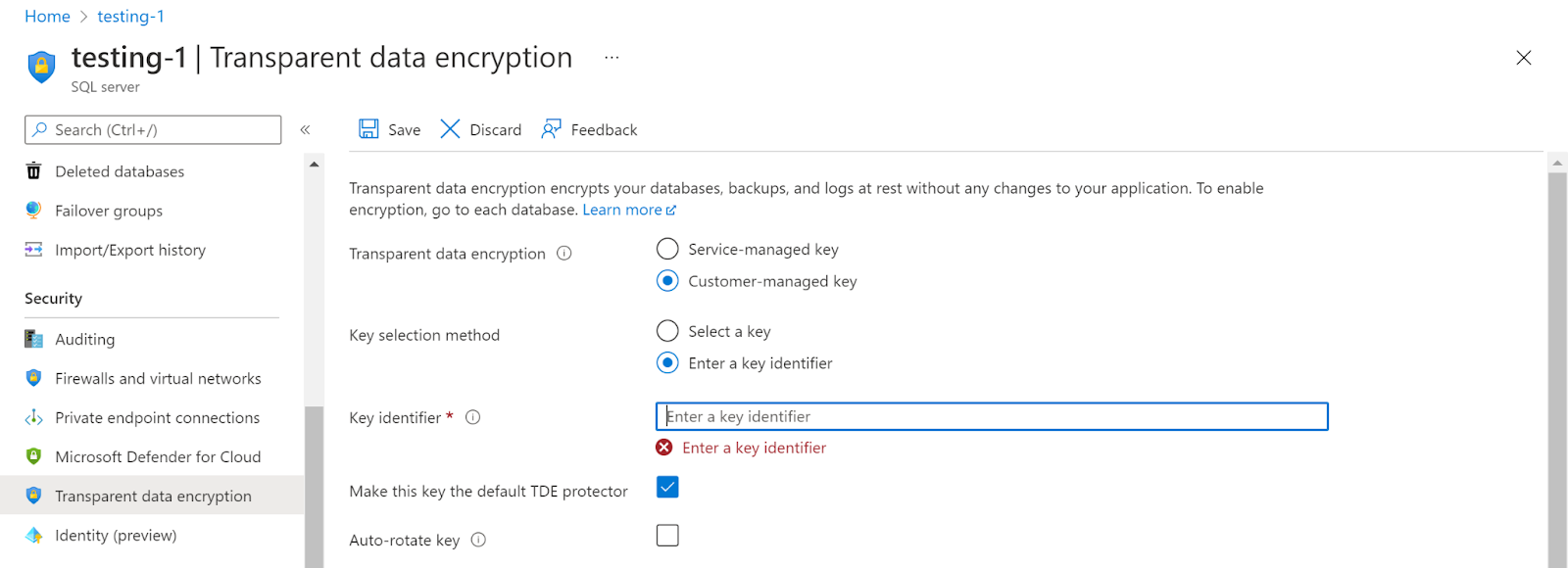
- To enter the key identifier, navigate to the Key vaults and then to the Keys option under Settings and then copy the key identifier and paste it in the Key identifier option and click on the Save button.
- Now, the customer-managed keys are enabled in the TDE.
- Repeat the same steps for other SQL Server as well.
References :
Please feel free to reach out to support@pingsafe.ai with any questions that you may have.
Thanks
PingSafe Support
