Risk Level: Medium
Description:
This plugin ensures AWS Transfer servers have CloudWatch logging enabled. Without a proper IAM service role, AWS Transfer servers cannot log activity of users. PingSafe recommends logging all activities of AWS Transfer for better visibility of infrastructural processes.
About the Service :
AWS Transfer Family is a secure transfer service that enables you to transfer files into and out of AWS storage services AWS Transfer Family supports transferring data from Amazon Simple Storage Service (Amazon S3) storage, Amazon Elastic File System (Amazon EFS) Network File System (NFS) file system, etc..
Impact:
Logs are important for keeping a track of requests made. It is recommended to regularly keep a close eye on the logs for any unusual activity. In the event of data compromise, generated logs will be useful to identify unusual or unauthorized access. It can eventually lead to the attacker's details. Without logs, the security team will not have any information to begin the investigation.
Steps to reproduce :
- Sign in to your AWS Management Console.
- Navigate to the AWS Transfer service dashboard at: https://console.aws.amazon.com/transfer/
- In the navigation panel, choose Servers.
- A list of available servers will be displayed. Select the one you wish to examine by clicking the server ID.
- Scroll down to the Additional Details section, check if there exists a valid role to transfer logs to CloudWatch. If not, the vulnerability exists.
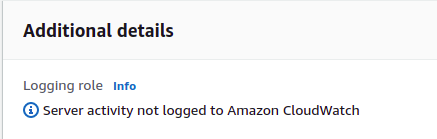
- Repeat steps for other servers you wish to examine as well.
Steps for remediation:
- Sign in to your AWS Management Console.
- Navigate to the AWS Transfer service dashboard at: https://console.aws.amazon.com/transfer/
- In the navigation panel, choose Servers.

- A list of available servers will be displayed. Select the vulnerable server by clicking the server ID.
- Scroll down to the Additional Details section and click on Edit.
- Choose an appropriate role for Amazon Cloudwatch to properly audit logs and finally Save the changes.
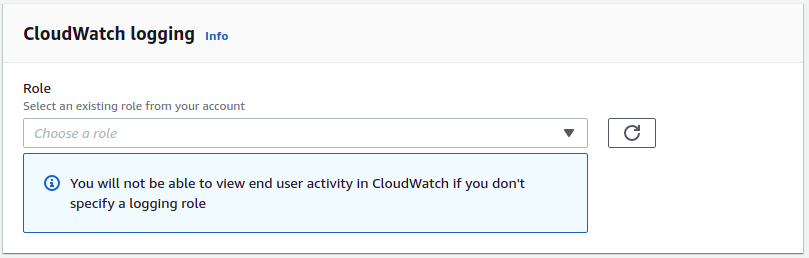
- Repeat steps for other vulnerable servers.
