This plugin ensures Elastic Block Store backed AMIs are configured to use encryption.
Risk Level: Low
Description
This plugin ensures Elastic Block Store backed AMIs are configured to use encryption. AMIs with unencrypted data volumes will launch instances with unencrypted EBS volumes. EBS volumes must be encrypted with an AWS KMS key to ensure that data is not exposed in case of a data breach.
About the Service
Amazon EC2: Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the Amazon Web Services (AWS) Cloud. With the EC2 instance, you can launch as many virtual servers as you need, configure security and networking, and manage storage without worrying about the hardware needs of the process. Security Groups act as a firewall for an EC2 instance to control the incoming and outgoing traffic. You can read more about security groups here.
Impact
EBS snapshots can contain critical information of the running EC2 instances. If exposed to the public, anyone over the Internet can have access to it. Therefore, it must be encrypted before storing data to avoid data readability. AMIs are used to create instances. It is essential to configure AMI to create encrypted EBS volumes attached to it to avoid security risks.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the VPC Management Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- Move to the AMIs in the Images section from the left navigation pane.

- A list of AMIs in the region will appear. Select the AMI you wish to investigate by clicking on the checkbox next to it.
- Under the Details tab, copy the snapshot id present in the Root Device Type value.
- Now, move to the Snapshots section from the left navigation pane.
- Paste the snapshot Id in the filter tab and check the Encryption column. If the value is “Not Encrypted”, the vulnerability exists.
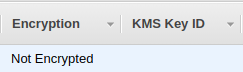
- Repeat steps for all the AMIs you want to investigate.
Steps for Remediation
Ensure all AMIs have encrypted Elastic Block Store volumes:
- Log In to your AWS Console.
- Open the VPC Management Console. You can use this link (https://console.aws.amazon.com/ec2) to navigate directly if already logged in.
- Move to the AMIs in the Images section from the left navigation pane.

- A list of AMIs in the region will appear. Select the vulnerable AMI by clicking on the checkbox next to it.
- From the Actions drop-down menu, select the Copy option.
- Provide an appropriate description and click on the Encryption checkbox to enable encryption.
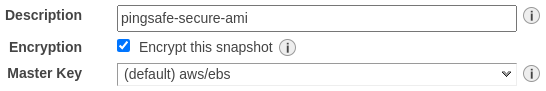
- Click on Copy to create a secure AMI.
- Now, select the previous AMI and from the Actions menu, select Deregister to delete the AMI.
- Repeat steps for all the vulnerable AMIs.
