This plugin detects the access keys that have not been used for a period of time and that should be decommissioned.
Risk Level: High
Description:
This plugin detects the access keys that have not been used for a period of time and that should be decommissioned. Having numerous, unused access keys extends the attack surface. Access keys should be removed if they are no longer being used.
PingSafe strongly recommends logging into the IAM portal and remove the offending access key.
Note:
AWS updates the Credential Report every 4 hours, it'll get updated soon please check back later. https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html
Configuration Parameters
Access Keys Last Used Threshold: The input in the field is an integer and it is the maximum number of days an access key can be left unused. Once, the threshold frequency which by default is of 180 days is reached (i.e. the key has not been used for consecutive 180 days) an alert is issued.
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
In the presence of numerous unused access keys the attack surface increases. Hence, to avoid any such compromise or any such impacts access keys should be monitored and unused access keys should be removed.
Steps to reproduce :
- Sign-in to AWS management console.
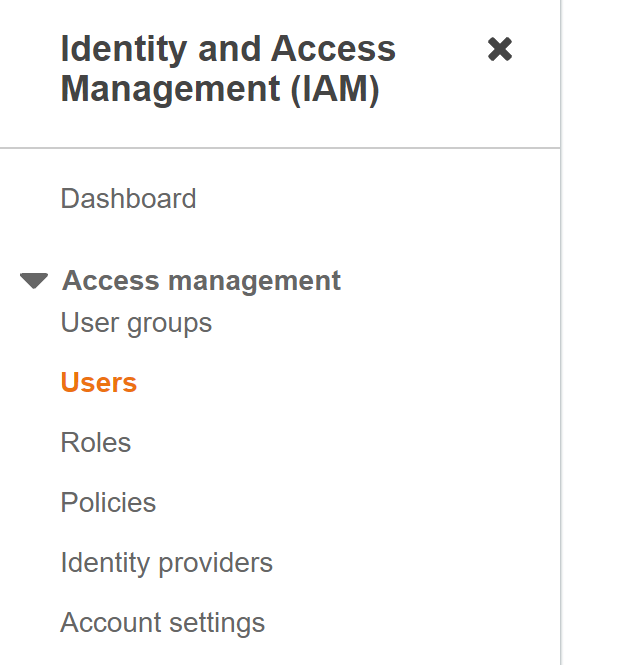
- Navigate to the “IAM” dashboard.
https://console.aws.amazon.com/iamv2/ - Select “Users” in the left navigation panel.
- Click on the User that you want to examine and select “Security Credentials”.
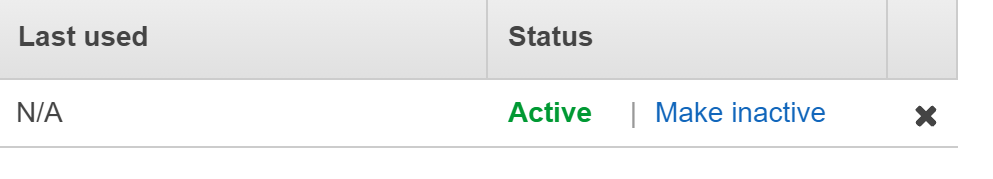
- Check the current status of the user in the “Status” column. If the IAM user has more than one access key activated that suggests that the user configuration does not follow best practices.
Steps for remediation :
- Sign-in to AWS management console.
- Navigate to the “IAM” dashboard. (https://console.aws.amazon.com/iamv2/ )
- Select “Users” in the left navigation panel.

- Click on the User that you want to examine and select “Security Credentials”.
- Check the current status of the user in the ”Status” column. If the IAM user has more than one access key activated that suggests that the user configuration does not follow best practices.
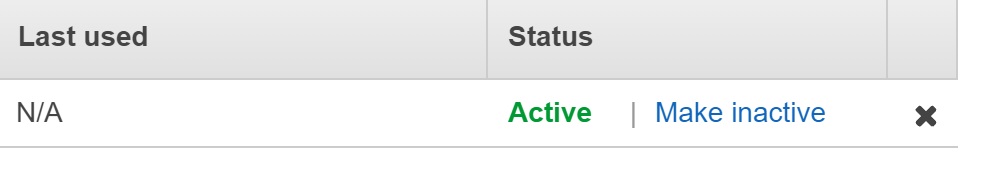
- Deactivate the non-operational access key by clicking on the “Make Inactive” button.
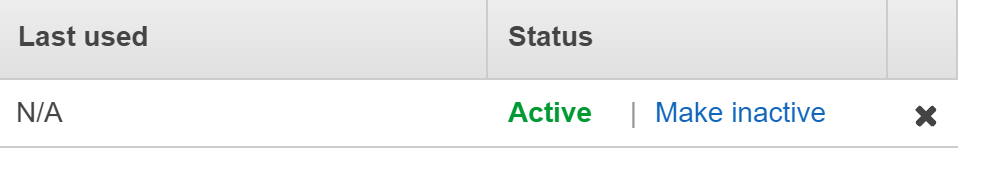
- Click Deactivate to switch off the selected key.
References:
