Risk Level: Medium
Description:
This plugin determines whether or not users that have a console password also utilize access keys. Access keys should only be provided to machine users and should not be utilized for console password-protected accounts.
PingSafe strongly recommends removing access keys from all users with console access.
Note:
AWS updates the Credential Report every 4 hours, it'll get updated soon please check back later. https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html
About the Service :
AWS ID and Access Management (IAM) allows you to securely manage access to AWS services and resources. With IAM, AWS users and groups can be established and managed and permissions used to enable access by AWS resources and prohibit them.
We can discover and adjust the rules so that only the services are accessible. We can thus adhere better to the less privileged principle.
Impact :
Controlling the rights of the IAM users in your account will help you maintain a safe AWS environment. If users who have a console password also use access keys, it's a sign that optimal security procedures aren't being followed.
Steps to reproduce :
- Sign-in to AWS management console.
https://ap-south-1.console.aws.amazon.com/console/ - Click on the “Account Name” and select “My Security Credentials”.
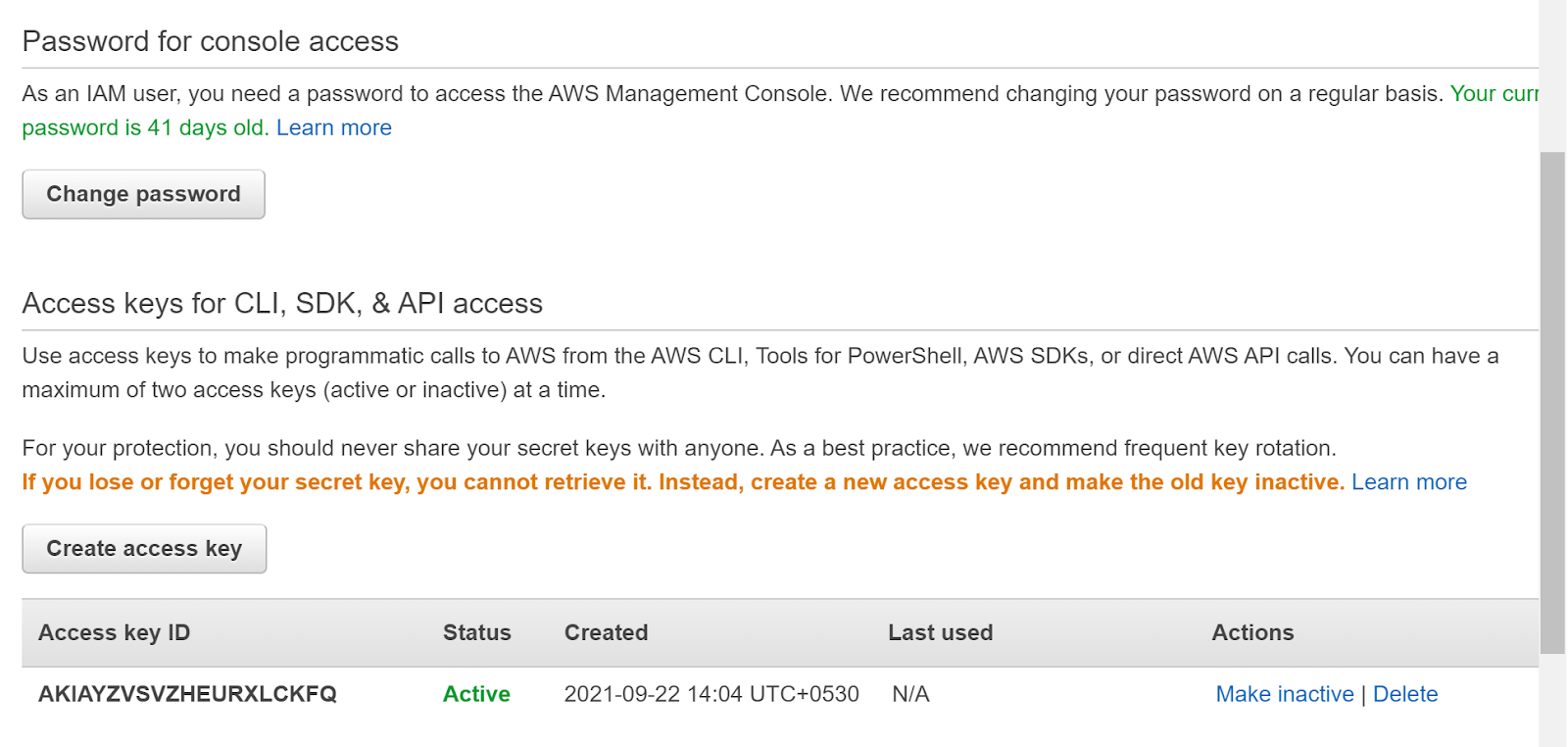
- Check the Access keys for CLI, SDK, & API access tab for the Access keys. If there are one or more access keys and the password is also set active for the account that suggests that the best security practices are not being followed.
- Repeat steps for other users as well.
Steps for remediation :
- Sign-in to AWS management console.
https://ap-south-1.console.aws.amazon.com/console/ - Click on the “Account Name” and select “My Security Credentials”.

- Check the Access keys for CLI, SDK, & API access tab for the Access keys. If there are one or more access keys and the password is also set active for the account that suggests that the best security practices are not being followed.

- Click on Delete to delete the access key and follow the security practices.
- Repeat steps for other users as well.
References:
