This plugin ensures that Amazon VPC endpoints do not allow unknown cross-account access
Risk Level: Medium
Description
This plugin ensures that Amazon VPC endpoints do not allow unknown cross-account access. VPC endpoints are often accessed by various AWS services for the proper functioning of the cloud architecture. To avoid malicious requests made to the services contained in the VPC, it must not be exposed to untrusted accounts.
Configuration Parameters
VPC Trusted Cross Account ARNs: This parameter denotes a comma-separated list of trusted cross-account ARNs i.e. 'arn:aws:iam::000111222333:user/user1,arn:aws:iam::000111222333:user/user2'. An issue will be generated if the VPC endpoints allow access to accounts apart from the specified ARNs.
By default, its value is empty. Therefore, a vulnerability alert will be generated if the VPC endpoint allows access to any other account apart from the owner account.
About the Service
Amazon EC2: Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the Amazon Web Services (AWS) Cloud. With the EC2 instance, you can launch as many virtual servers as you need, configure security and networking, and manage storage without worrying about the hardware needs of the process. Security Groups act as a firewall for an EC2 instance to control the incoming and outgoing traffic. You can read more about security groups here.
Impact
Various services reside in a Virtual Private Cloud (VPC). Exposing VPC endpoints to untrusted accounts can allow unsigned requests to be made to the network interface. This can be a security threat to the services in the VPC as the attacker can exploit the vulnerability of any service inside the VPC.
Steps to Reproduce
Using AWS Console-
- Log In to your AWS Console.
- Open the VPC Management Console. You can use this link (https://console.aws.amazon.com/vpc) to navigate directly if already logged in.
- Move to the Endpoints in the Virtual Private Cloud section from the left navigation pane.
- You will find a list of Endpoints available. If the endpoint type is “gateway”, the vulnerability does not exist. Select the one you wish to examine by clicking on the checkbox next to it.
- Move to the Policy tab.

- If the Effect element is set to “Allow”, examine the Principal element. If the Principal element has an unknown account ARN, the vulnerability exists.
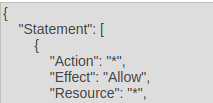
- Repeat steps for all the VPC Endpoints you want to investigate.
Steps for Remediation
Update VPC endpoint access policy in order to remove untrusted cross account access:
- Log In to your AWS Console.
- Open the VPC Management Console. You can use this link (https://console.aws.amazon.com/vpc) to navigate directly if already logged in.
- Move to the Endpoints in the Virtual Private Cloud section from the left navigation pane.

- You will find a list of Endpoints available. Select the vulnerable endpoint by clicking on the checkbox next to it.
- Move to the Policy tab.

- Click on the Edit Policy button. Copy the previous policy.
- Choose the Custom option. Paste the existing policy in the editor.
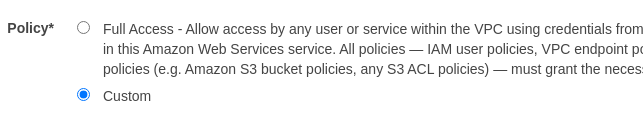
- Now modify the Principal element of the policy by adding the ARN of the IAM users who can access the VPC and removing the unknown ARN.
- Repeat steps for all the vulnerable VPC Endpoints.
